- Home
- Exchange
- Exchange Team Blog
- Basic Authentication and Exchange Online – July Update
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Update: The full timeline for retirement of Basic Authentication in Exchange Online is now published in Basic Authentication Deprecation in Exchange Online – September 2022 Update.
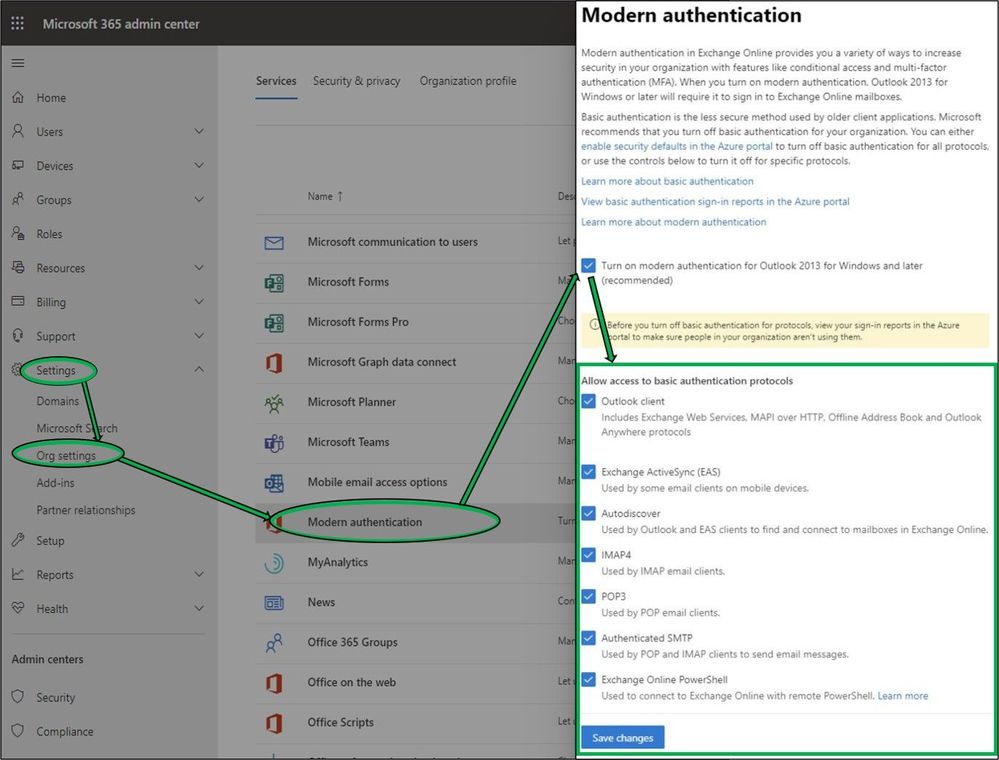
Today we are pleased to announce some new changes to Modern Authentication controls in the Microsoft 365 Admin Center, exposing simpler options for customers to manage both Modern and Basic Authentication requirements within their organizations. Available from within the Admin Center under Settings > Org Settings > Modern Authentication (alternatively, search for “Modern Authentication” in portal Home page Search field), customers may now quickly designate the protocols in their tenant that no longer require Basic Authentication to be enabled.
While additional granularity is available through PowerShell, once Modern Authentication is enabled these new UI options will provide Administrators simpler controls to manage Basic Authentication access to common protocol combinations. These new changes, rolling out to all tenants, align with our entry from the M365 Roadmap.
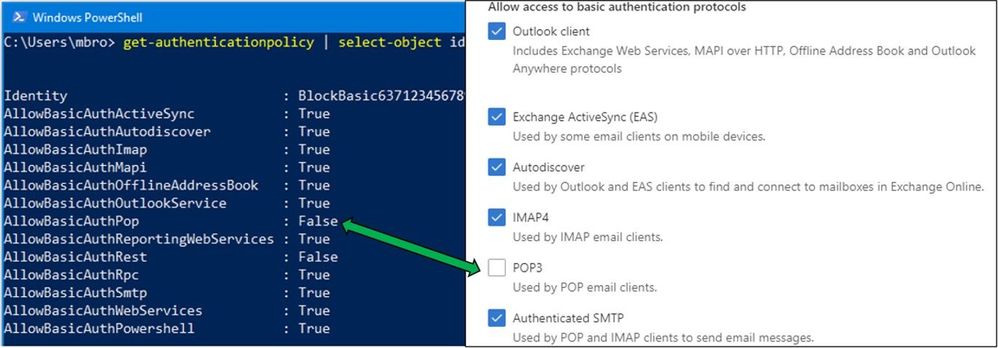
Behind the scenes, these new Modern Auth UI options utilize Authentication Policies. For customers that have not created their own Authentication Policies in the past, modifying any of these selections in the new UI (POP3 in the example below) will automatically create the first new Authentication Policy. This policy is visible only through PowerShell. For advanced customers that may already be utilizing Authentication Policies, changes within the UI will modify their existing default policy. You’ll want to look through your Azure AD Sign-in logs to get a good idea of which protocols clients are using before making any changes.
Additional Information
We realize there may be some confusion around different efforts Microsoft is making to provide more secure environments for our customers. The easiest answer for customers who aren’t using Basic Authentication, and don’t have a complicated auth story, is to enable Security Defaults. Otherwise, while the below isn’t an exhaustive list, we thought it would be a good idea to try to cover a few additional details here.
Modern vs. Basic Authentication: Hopefully by now we don’t need to expand upon the virtues of Modern Authentication. Enabled by default for all new tenants since August 1, 2017, Modern Auth is the superior alternative for all users and applications connecting to Office 365. If you haven’t turned Modern Authentication on yet we certainly recommend it. Just be aware this switch affects all the Outlook for Windows clients in your entire tenant, so make sure you are clear on how it may affect your users.
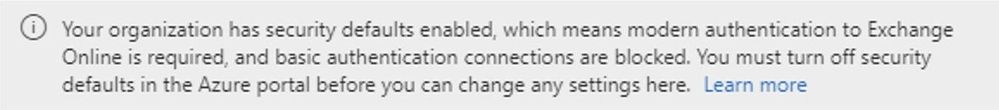
Security Defaults (for organizations without Azure AD Premium licenses): If your tenant was created on or after October 22, 2019, it is possible that Security Defaults are already enabled in your tenant. In an effort to provide basic level of security, Security Defaults are being rolled out to all newly created tenants. Security Defaults block all Legacy/Basic Authentication and enable Modern/Multi-Factor Authentication for all users. We should clarify that Security Defaults are typically tailored for new customers or those who are new to managing their own security story. While the end results are similar, Security Defaults do not utilize Exchange Authentication Policies under the hood. Thus, to prevent overlap and confusion, we restrict the combination of these controls in the new Modern Auth UI. If Security Defaults are enabled in the organization, administrators attempting to use new Modern Auth UI will be presented with the following text. (You should disable Security Defaults only if you understand the risks of using Basic Authentication.)
Conditional Access (for organizations with Azure AD Premium licenses): If you tenant is licensed with Azure AD Premium or EMS licenses then you will be able to block legacy/basic authentication using Conditional Access for a set or all users in your organization. For more information see: How to: Block legacy authentication to Azure AD with Conditional Access.
Authentication Policies: As announced last year, the Exchange Team is planning to disable Basic Authentication for the EAS, EWS, POP, IMAP, and RPS protocols in the second half of 2021. As a point of clarity, Security Defaults and Authentication Policies are separate, but provide complementary features. We recommend that customers use Authentication Policies to turn off Basic Authentication for a subset of Exchange Online protocols or to gradually turn off Basic Authentication across a large organization. While more details will come in future announcements, as mentioned in April, we plan to begin disabling Basic Authentication in existing tenants with no recorded usage as early as October 2020. We will provide notifications via Message Center posts before we disable Basic Authentication for any tenant.
Client SMTP Submission (SMTP AUTH): While SMTP AUTH Basic Authentication will not be deprecated, the use of Basic Authentication within SMTP AUTH is still considered insecure. There are multiple initiatives for SMTP AUTH that are worth calling out, and administrators should have familiarity with each of these:
- As announced in April, we have additionally disabled SMTP AUTH for all new Office 365 tenants by utilizing the SmtpClientAuthenticationDisabled parameter, and we’ll be expanding this effort over the next several months. If your tenant doesn’t need to use SMTP AUTH at all, this option allows the granularity to disable SMTP Auth for individual users via Set-CASMailbox or Set-TranportConfig for tenants. Read more here.
- For customers that still require SMTP AUTH, we’ve got you covered, with new options for implementing OAuth 2.0 for client applications. After updating your SMTP AUTH clients, please make sure you block legacy authentication methods via one of the following:
- Security Defaults (which as mentioned covers all protocols including SMTP AUTH) if enabled will block Basic Authentication access to SMTP AUTH for all end users within a tenant. Security Defaults is being rolled out as default for all new tenants and is the recommended action if it works for your organization.
- Authentication Policies, either via PowerShell or the new UI announced here today, can also block Basic Authentication access to SMTP AUTH for all or groups of users.
Exchange Online PowerShell: As we announced recently, Exchange Online PowerShell V2 module is now fully released and this is what you should use to connect using Modern Authentication. We have also recently announced the preview program which will allow you to run PowerShell scripts with Modern Authentication (using certificates).
If you have any feedback, please let us know in the comments below.
The Exchange Team
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.