- Home
- Microsoft Edge Insider
- Enterprise
- [Feature Request]: PWA pre-installation and protocol handling improvements.
[Feature Request]: PWA pre-installation and protocol handling improvements.
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 17 2023 09:16 AM - edited Jan 17 2023 12:59 PM
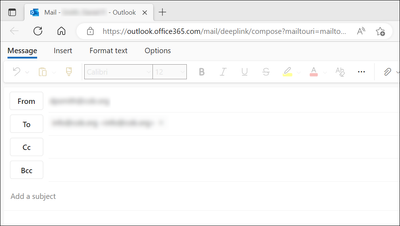
We want to silently (and fully) pre-install the PWA for "Outlook Online" and have it assume the role as the default protocol handler for all "mailto" links. We want the end-user to encounter absolutely no confirmation prompts related to this process. Their first encounter with a "mailto" link should be seamless and immediately direct them to the deeplink location for drafting a new mail message on "Outlook Online":
Here's what we've done so far:
- We're using the "WebAppInstallForceList" GPO to pre-install the PWA for "Outlook Online".
This works "okay", but it takes a deliberate page view of https://outlook.office365.com in order to fully complete the installation of the PWA. We've gotten around this by adding an entry to the user's "RunOnce" registry key to launch Edge and visit that site (yes, we have SSO for Azure enabled). Not ideal, but it works. - We're then using the "Set a default association configuration file" GPO to define "mailto" = "MSEdge.3675880767".
"MSEdge.3675880767 seems to be the common identifier for the "Outlook Online" PWA (at least on Windows 11). This works fine only if the PWA has fully installed itself (see above). Due to timing issues and order of operations, the failure of a PWA to fully install before a "mailto" link is used can cause hiccups. When the "WebAppInstallForceList" GPO does its work, it appears that only a "stub" of the desired PWA is put into place, requiring a manual visit by the user to the PWA's site on the web (see above).
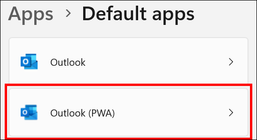
You can also see if the "Outlook (PWA)" entry is available in the list for selecting "Default Apps". It won't appear here unless that first website visit has been is completed:
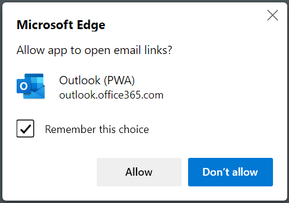
Request: Please fully pre-install the PWA (if enforced by GPO). - Here's where we run into the largest wrinkle we're trying to eliminate. Upon first use of a "mailto" link, the user is prompted by Edge to confirm whether this is okay.
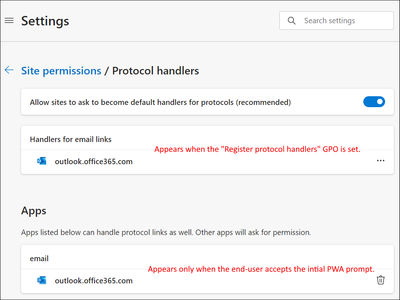
We do not want the end-users to encounter this prompt as we're already pre-installing the PWA and setting it as the default "mailto" handler via GPO. We've tried using the "Register protocol handlers" GPO, but that only adds an entry under the "Handlers for email links" section of "Site permissions / Protocol handers". It doesn't eliminate this prompt. In fact the "Register protocol handlers" GPO doesn't seem to be related to pre-approving the use of PWAs as protocol handlers at all its just for "URLs".
As you can see, the entry under "Apps" only appears when the user accepts the prompt (shown above). We've done a deep-dive into GPO and Chromium settings and there doesn't seem to be a way to add any entries under the "Apps" category for installed PWAs:
Request: Please allow PWAs to be pre-approved for use as a protocol handler via GPO.
EDIT/UPDATE: We've also tried both of the following settings with the "AutoLaunchProtocolsFromOrigins" GPO, but to no effect:[{"protocol": "mailto","allowed_origins": ["https://outlook.office365.com"]}]
[{"protocol": "mailto","allowed_origins": ["*"]}]
In summary:
I hope others are helped by this write-up. We hope that Microsoft can take a look at these issues related to protocol handling and the pre-installation of PWAs in Edge. It would be fantastic if we could have users directly use the Outlook PWA without any prompting or issues related to the pre-installation of the app.
Thanks for your time!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 17 2023 12:02 PM
@Daniel Smith Hello! Thanks for reaching out, appreciate the thoughtful and thorough explanation.
Regarding the first request about pre-install of the PWA, this question has come up previously and our developers have said the browser needs to run at least once if the WebAppInstallForceList policy is used to install apps because the policy regkey is only read once on browser launch.
For the second request about the protocol handlers, have you looked at the AutoLaunchProtocolsFromOrigins policy? I have not tested but the description looked like it might be helpful in your scenario.
-Kelly
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 17 2023 12:51 PM
We've tried both of the following with the "AutoLaunchProtocolsFromOrigins", but to no effect:
[{"protocol": "mailto","allowed_origins": ["https://outlook.office365.com"]}]
[{"protocol": "mailto","allowed_origins": ["*"]}]
As for a first launch of Edge scenario, we tried launching Edge as a service (using the command line switch "--no-startup-window") along with piping in the desired URL. Alas, that didn't work either. Our best hack would be to launch edge via a "hidden" window using vbscript or something similar.
Thanks for engaging us on this!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 23 2023 04:52 PM
@Daniel Smith Hey! I've passed your questions on to the team and will follow up if they share any insights or recommendations for your scenario. Thanks!
-Kelly
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 24 2023 08:46 AM
I was just reading about the "One Outlook" app which Microsoft is working on:
https://mspoweruser.com/microsoft-moves-a-step-closer-to-replacing-windows-11-stock-mail-app-with-th...
If it is truly a glorified "PWA", then I'm wondering if that's where the developers are working to iron out all of the issues related to protocol handling? It would be nice to have something like this that's easier to support than the legacy version of the original Outlook client.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 22 2023 09:32 AM
Hello, has there been any response from the engineers about this?