Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- The Launch of Office 2016: The Most Secure Office EVER
The Launch of Office 2016: The Most Secure Office EVER
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Published
Sep 08 2018 07:30 AM
2,089
Views
Sep 08 2018
07:30 AM
Sep 08 2018
07:30 AM
First published on CloudBlogs on Sep 23, 2015
If you are someone who receives e-mail, writes things, or uses spreadsheets – yesterday was a big day for you. As Satya noted on the Official Microsoft Blog , Office 2016 has launched and is full of new capabilities. The tagline for this release of Office is that it “Takes the work out of working together” – and I think that summarizes its new features and UX perfectly. Check out these in-depth looks at what’s new and improved in Office 2016 – I think you’ll be really impressed. For me, personally, seeing the development of this new version of Office has been a very unique experience. During each stage of the development process, I’ve been blown away by the tremendous amount of teamwork and partnership between the Enterprise Mobility Suite (EMS) team and the engineering teams over in Office. The result is incredible integration and interoperability between these two services. Using them together delivers the scenarios you’ve been requesting . With all of this in mind, I thought it would be helpful to show what makes this the most secure Office ever by elaborating on what’s natively in Office 2016, as well as detailing how EMS and Office 2016 have been engineered to be used together to provide additional security and protection.

 In these instances, the user is given visibility and reminded there may sensitive information in the document they are editing. By giving the user this visibility, they are empowered to make the decisions to help protect confidential and sensitive data.
Parts of Microsoft Intune (from EMS) are also built into the hybrid Office 2016 and Office 365 solution. Organizations now have a rich MDM solution that adds more than 100 additional settings that can be managed from Office 365 to apply policies to the mobile devices being used. Of course, as the organizations MDM needs increase and mature, it is simple to start using the full MDM and MAM capabilities in the full Intune.
To review what Intune capabilities are natively included in Office 365, you can
read this blog post
. Office and EMS are actively working together to empower your users while helping secure your company’s data.
Here’s the critical thing to understand:
When EMS and Office 2016 are used
together
they provide a rich management and Data Loss Prevention set of capabilities that are
only
possible when using EMS. The
other EMM vendors cannot deliver
these Data Loss Prevention capabilities in the Office mobile apps. If you need to be able to manage where users can save corporate documents, or if you want to help manage cut/copy/paste to only corporate apps – it’s EMS that delivers this capability.
To learn more about this, check out previous posts on
Enhanced Data Protection with Windows 10
,
Integrating Windows 10 Identity with EMS
,
Enterprise Mobility App & Data Protection
,
The Cloud-Device Convergence
, and the
Managed Outlook app
.
In these instances, the user is given visibility and reminded there may sensitive information in the document they are editing. By giving the user this visibility, they are empowered to make the decisions to help protect confidential and sensitive data.
Parts of Microsoft Intune (from EMS) are also built into the hybrid Office 2016 and Office 365 solution. Organizations now have a rich MDM solution that adds more than 100 additional settings that can be managed from Office 365 to apply policies to the mobile devices being used. Of course, as the organizations MDM needs increase and mature, it is simple to start using the full MDM and MAM capabilities in the full Intune.
To review what Intune capabilities are natively included in Office 365, you can
read this blog post
. Office and EMS are actively working together to empower your users while helping secure your company’s data.
Here’s the critical thing to understand:
When EMS and Office 2016 are used
together
they provide a rich management and Data Loss Prevention set of capabilities that are
only
possible when using EMS. The
other EMM vendors cannot deliver
these Data Loss Prevention capabilities in the Office mobile apps. If you need to be able to manage where users can save corporate documents, or if you want to help manage cut/copy/paste to only corporate apps – it’s EMS that delivers this capability.
To learn more about this, check out previous posts on
Enhanced Data Protection with Windows 10
,
Integrating Windows 10 Identity with EMS
,
Enterprise Mobility App & Data Protection
,
The Cloud-Device Convergence
, and the
Managed Outlook app
.
 With RMS, a user sharing a protected document can receive an e-mail any time someone attempts to access that document. The original sender gets an e-mail with a link to a document tracking site. In this example, you can see that this document has been successfully opened 16 times, and there have been 14 attempts to open the document by users who were not authorized. In each of those 14 cases EMS blocked the attempt to open the doc.
If you’re the owner of this doc, this report should really get your attention. The document tracking site can also show you a timeline view of this activity:
With RMS, a user sharing a protected document can receive an e-mail any time someone attempts to access that document. The original sender gets an e-mail with a link to a document tracking site. In this example, you can see that this document has been successfully opened 16 times, and there have been 14 attempts to open the document by users who were not authorized. In each of those 14 cases EMS blocked the attempt to open the doc.
If you’re the owner of this doc, this report should really get your attention. The document tracking site can also show you a timeline view of this activity:
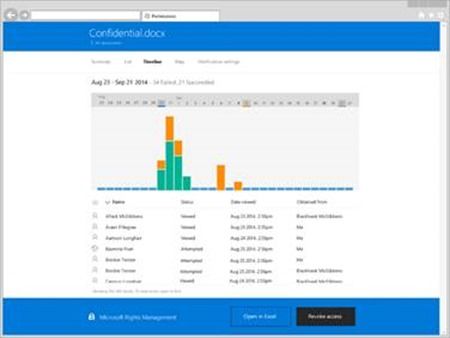 For even greater insight, the document tracking site can show you
where
these attempts to access your document were located. If you were to drill into any of the bubbles below it would take you down to the city or town of these blocked access attempts.
For even greater insight, the document tracking site can show you
where
these attempts to access your document were located. If you were to drill into any of the bubbles below it would take you down to the city or town of these blocked access attempts.
 Also, if, for some reason, you need to revoke access, it’s just a matter of a few clicks to disable access globally.
Also, if, for some reason, you need to revoke access, it’s just a matter of a few clicks to disable access globally.

If you are someone who receives e-mail, writes things, or uses spreadsheets – yesterday was a big day for you. As Satya noted on the Official Microsoft Blog , Office 2016 has launched and is full of new capabilities. The tagline for this release of Office is that it “Takes the work out of working together” – and I think that summarizes its new features and UX perfectly. Check out these in-depth looks at what’s new and improved in Office 2016 – I think you’ll be really impressed. For me, personally, seeing the development of this new version of Office has been a very unique experience. During each stage of the development process, I’ve been blown away by the tremendous amount of teamwork and partnership between the Enterprise Mobility Suite (EMS) team and the engineering teams over in Office. The result is incredible integration and interoperability between these two services. Using them together delivers the scenarios you’ve been requesting . With all of this in mind, I thought it would be helpful to show what makes this the most secure Office ever by elaborating on what’s natively in Office 2016, as well as detailing how EMS and Office 2016 have been engineered to be used together to provide additional security and protection.
It has to be Simple & it has to be Integrated with How Users Work
Over the last couple years, I have written a ton about the importance of data security and the significant amount of work being done by the engineering teams across Microsoft to help users (and the data they’re accessing) be more secure than ever before – while still delivering a great end-user experience. This topic hits home for nearly everyone: We all recognize that if what we build is not simple and integrated with how users work, the solution is seen as too complex and won’t get used. It really is that black and white . If the end product feels too complex or unnatural, users will struggle and often fight using it. This has been a huge area of focus for us, and, as I look at how we are surfacing these user-centric capabilities in Office 2016 and EMS, I feel like we have done a great job of empowering users to stay both productive and protect the company assets. Certainly, having done this is no small feat. It’s the result of making security and productivity key areas of focus, and, with these priorities set first and foremost, we dove deep into the feedback you’ve provided in order to make the functionality and the UX excellent, and integrated with how users work. The final result is polished, un-intrusive, intuitive, and “in-the-flow” of how users get stuff done today.What does it mean to be “The Most Secure Office?”
Across Microsoft we focused on 3 key elements to make Office 2016 optimally secure:- Data Protection and Data Loss Prevention
- Ensure The User is Who They Say They Are
- Protect Data At-Rest and In-motion
Data Protection and Data Loss Prevention
There are Data Protection and Data Loss Prevention capabilities natively built-into Office 2016. To learn more, check out this great blog covering these in-box features. With these features, IT Pros can define policies about the kinds of information and data that, when detected in an Office document, can be flagged to users – thus requesting them to ensure they mean to be working with this data. For example , you can set a policy that, if credit card numbers, passport numbers, social security numbers (and a long list of other sensitive information types) are detected in the document, the user can be shown a “policy tip” to help guide them. Here are some examples of what these policy tips looks like:

 In these instances, the user is given visibility and reminded there may sensitive information in the document they are editing. By giving the user this visibility, they are empowered to make the decisions to help protect confidential and sensitive data.
Parts of Microsoft Intune (from EMS) are also built into the hybrid Office 2016 and Office 365 solution. Organizations now have a rich MDM solution that adds more than 100 additional settings that can be managed from Office 365 to apply policies to the mobile devices being used. Of course, as the organizations MDM needs increase and mature, it is simple to start using the full MDM and MAM capabilities in the full Intune.
To review what Intune capabilities are natively included in Office 365, you can
read this blog post
. Office and EMS are actively working together to empower your users while helping secure your company’s data.
Here’s the critical thing to understand:
When EMS and Office 2016 are used
together
they provide a rich management and Data Loss Prevention set of capabilities that are
only
possible when using EMS. The
other EMM vendors cannot deliver
these Data Loss Prevention capabilities in the Office mobile apps. If you need to be able to manage where users can save corporate documents, or if you want to help manage cut/copy/paste to only corporate apps – it’s EMS that delivers this capability.
To learn more about this, check out previous posts on
Enhanced Data Protection with Windows 10
,
Integrating Windows 10 Identity with EMS
,
Enterprise Mobility App & Data Protection
,
The Cloud-Device Convergence
, and the
Managed Outlook app
.
In these instances, the user is given visibility and reminded there may sensitive information in the document they are editing. By giving the user this visibility, they are empowered to make the decisions to help protect confidential and sensitive data.
Parts of Microsoft Intune (from EMS) are also built into the hybrid Office 2016 and Office 365 solution. Organizations now have a rich MDM solution that adds more than 100 additional settings that can be managed from Office 365 to apply policies to the mobile devices being used. Of course, as the organizations MDM needs increase and mature, it is simple to start using the full MDM and MAM capabilities in the full Intune.
To review what Intune capabilities are natively included in Office 365, you can
read this blog post
. Office and EMS are actively working together to empower your users while helping secure your company’s data.
Here’s the critical thing to understand:
When EMS and Office 2016 are used
together
they provide a rich management and Data Loss Prevention set of capabilities that are
only
possible when using EMS. The
other EMM vendors cannot deliver
these Data Loss Prevention capabilities in the Office mobile apps. If you need to be able to manage where users can save corporate documents, or if you want to help manage cut/copy/paste to only corporate apps – it’s EMS that delivers this capability.
To learn more about this, check out previous posts on
Enhanced Data Protection with Windows 10
,
Integrating Windows 10 Identity with EMS
,
Enterprise Mobility App & Data Protection
,
The Cloud-Device Convergence
, and the
Managed Outlook app
.
Ensure The User is Who They Say They Are
Identity is the foundation of the platform and architecture that empowers users to access and use corporate content across all their devices. At the same time, however, identity is the primary attack vector used by malicious individuals and organizations. Strong identity management is more important today than it has ever been – as noted previously , over 75% of the corporate security breaches are eventually tracked down to weak or compromised user identities. The advice I give organizations is simple: Assume that you’ve been compromised and act accordingly. You should assume that user identities from your organization have been phished and attackers are using valid usernames/passwords to steal from or disrupt your business. One of the ways to prevent these kinds of attacks is to use multi-factor authentication ( MFA ). Office 2016 has native support for enabling multi-factor authentication – meaning the user can be challenged to provide multiple forms of “credentials” to authenticate when requesting access to company data. For example : To get access to a specific Word document, the user may be required to provide a username/password as well as a PIN that is sent to their phone. EMS brings enhanced MFA to Office 2016: With EMS you can set policies that require the user to pass an MFA challenge before they can even open the Office mobile apps. In this scenario, you can get as specific as requiring the user to pass an MFA challenge whenever they are not physically at work. Over the last few months, we have introduced this capability throughout Microsoft. We are all now regularly challenged with MFA to ensure valid users are accessing the corporate content. Using the MFA capabilities of EMS is a core part of our corporate data protection strategy at Microsoft – and it should be a core part of yours, too.Protect Data At-Rest and In-motion
One of the most common ways organizations protect company data is using the Rights Management capabilities that are built into Office. Many (if not most) of you have received protected e-mails through Exchange and Outlook; I send protected e-mail every day. There are two great capabilities from EMS that are natively in Office 2016 in RMS. First , is the ability to open and view protected e-mail – across all your devices. Before July 2015 you could only create and read protected e-mail on Windows devices. In July we added the ability to read these e-mails and documents on iOS devices (Android support is coming soon). We will also soon be extending this functionality for creating and read-protected e-mail and documents on iOS and Android (Windows has been able to do this for years). With Office 2016, IT can set policies that automatically restrict documents to be viewed or edited strictly within the organization or within subsets of the organization. The document essentially becomes self-protecting because it knows who is authorized to open and edit it. You can read more details about this in this blog post . EMS enables these documents to be shared across companies – with partners and customers. You can read much more about this here . The second value delivered by EMS is the ability to view who is accessing or trying to access these protected document with the ability to revoke access instantly. Take a minute to review this post I published following my demo of it at Ignite, and here are a couple of screen shots showing the kind of insights EMS enables: With RMS, a user sharing a protected document can receive an e-mail any time someone attempts to access that document. The original sender gets an e-mail with a link to a document tracking site. In this example, you can see that this document has been successfully opened 16 times, and there have been 14 attempts to open the document by users who were not authorized. In each of those 14 cases EMS blocked the attempt to open the doc.
If you’re the owner of this doc, this report should really get your attention. The document tracking site can also show you a timeline view of this activity:
With RMS, a user sharing a protected document can receive an e-mail any time someone attempts to access that document. The original sender gets an e-mail with a link to a document tracking site. In this example, you can see that this document has been successfully opened 16 times, and there have been 14 attempts to open the document by users who were not authorized. In each of those 14 cases EMS blocked the attempt to open the doc.
If you’re the owner of this doc, this report should really get your attention. The document tracking site can also show you a timeline view of this activity:
 For even greater insight, the document tracking site can show you
where
these attempts to access your document were located. If you were to drill into any of the bubbles below it would take you down to the city or town of these blocked access attempts.
For even greater insight, the document tracking site can show you
where
these attempts to access your document were located. If you were to drill into any of the bubbles below it would take you down to the city or town of these blocked access attempts.
 Also, if, for some reason, you need to revoke access, it’s just a matter of a few clicks to disable access globally.
Also, if, for some reason, you need to revoke access, it’s just a matter of a few clicks to disable access globally.
To see this in action, check out this 5-minute section of the Ignite keynote (2:07:35 to 2:12:04).
With Office 2016, organizations can dramatically limit the risk of sensitive data leakage via the built-in data-loss prevention functionality in the tools you already use every day. These capabilities are dramatically enhanced when EMS is used in conjunction with Office. We have built Office and EMS to be used together to deliver the a rich and empowering work environment for users, while helping protect any organization’s data. For those of you with the luxury of time for additional reading, I really recommend checking out these detailed blog posts covering a handful of specific security and data protection topics:- Enhanced Data Protection (Ignite demo)
- App & Data Protection
- Containing Corporate Data
- Cloud-based Data Protection (podcast)
- Secure Containers (podcast)
- Conditional Access (podcast)
- The “Managed Everything” Model
- Protecting Data in a Mobile-first, Cloud-first World
- The Enterprise Mobility Stack
What’s Next
- Start using Office 365 to get the new 2016 apps!
- If you’re an existing Office 365 customer looking to upgrade, go here to upgrade your business (or here to upgrade your home).
- For even more info on Office 2016, visit: Office.com/2016 .

0
Likes
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.