- Home
- Security, Compliance, and Identity
- Core Infrastructure and Security Blog
- Preparing to Deploy Extended Security Updates
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Update 02.03.2020: Updated post to confirm that Security Only Quality Updates from November 2019 and onward satisfy the pre-requisites for the ESU key.
With the end of support for these Operating Systems on January 14, 2020, many of our customers are asking for help on how to get ready to deploy Extended Security Updates (ESU). To that end, I would like to share the work of Curtis Ricard a Senior Premier Field Engineer on how to use Microsoft Endpoint Configuration Manager (ConfigMgr) to ensure that your clients are ready to receive the ESU updates.
Curtis and I both engage with customers that have chosen to utilize the Extended Security Update program. If you would like to know more about the program please review https://support.microsoft.com/en-us/help/4497181/lifecycle-faq-extended-security-updates
There are a few key points to consider with this program:
- The Extended Security Update (ESU) program is a last resort option for customers who need to run certain legacy Microsoft products past the end of support. It includes Critical* and/or Important* security updates for a maximum of three years after the product’s End of Extended Support date. Extended Security Updates will be distributed if and when available.
- ESUs do not include new features, customer-requested non-security updates, or design change requests.
- All Windows 7 customers will get an update on January 14, 2020 as the operating system is in support until then. Updates for these operating systems after January 14, 2020 will be for ESU customers only. ESU is available for Win 7 Professional & Win 7 Enterprise.
- Customers use the support plan they have; ESU offering does not include technical support*
*If any root cause investigation determines that resolution requires product enhancement(s) available in a more recent release, then customer may be required to upgrade
Also see the “How to get Extended Security Updates for eligible Windows devices” blog
*For licensing purchase questions, please contact your Microsoft Account Team.
If you have chosen to purchase ESU support then there are some prerequisites for your on-premise device(s) that must be met to ensure that your systems will be able to install the ESU updates:
- Install the following SHA-2 code signing support update and servicing stack update (SSU) or a later SSU update:
- For Windows 7 and Windows Server 2008 R2, install at least one of the following servicing stack updates (SSU):
- 4516655 Servicing stack update for Windows 7 SP1 and Server 2008 R2 SP1: September 10, 2019
- 4523206 Servicing stack update for Windows 7 SP1 and Server 2008 R2 SP1: November 12, 2019
- 4531786 Servicing stack update for Windows 7 SP1 and Server 2008 R2 SP1: December 10, 2019
- 4536952 Servicing stack update for Windows 7 SP1 and Server 2008 R2 SP1: January 14, 2020
- For Windows Server 2008, install at least one of the following servicing stack updates (SSU):
- 4517134 Servicing stack update for Windows Server 2008 SP2: September 10, 2019
- 4526478 Servicing stack update for Windows Server 2008 SP2: November 12, 2019
- 4531787 Servicing stack update for Windows Server 2008 SP2: December 10, 2019
- 4536953 Servicing stack update for Windows Server 2008 SP2: January 14, 2020
- For Windows 7 and Windows Server 2008 R2, install at least one of the following security updates:
- 4519976 October 8, 2019—KB4519976 (Monthly Rollup)
- 4525235 November 12, 2019—KB4525235 (Monthly Rollup)
- 4525233 November 12, 2019—KB4525233 (Security-only update)
- 4530734 December 10, 2019—KB4530734 (Monthly Rollup)
- 4530692 December 10, 2019—KB4530692 (Security-only update)
- 4534310 January 14, 2020—KB4534310 (Monthly Rollup)
- 4534314 January 14, 2020—KB4534314 (Security-only update)
- For Windows Server 2008, install at least one of the following security updates:
- 4520002 October 8, 2019—KB4520002 (Monthly Rollup)
- 4525234 November 12, 2019—KB4525234 (Monthly Rollup)
- 4525239 November 12, 2019—KB4525239 (Security-only update)
- 4530695 December 10, 2019—KB4530695 (Monthly Rollup)
- 4530719 December 10, 2019—KB4530719 (Security-only update)
- 4534303 January 14, 2020—KB4534303 (Monthly Rollup)
- 4534312 January 14, 2020—KB4534312 (Security-only update)
- Install and activate the ESU key.
- For information about how to install and activate the ESU key, see the “How to get Extended Security Updates for eligible Windows devices” blog on the Microsoft Tech Community website.
Once you have the prerequisites in place, the following update will help you verify that your eligible Windows 7 SP1 devices can continue to get the ESUs after the end of support date of January 14, 2020. (Installing this update has no impact on getting security updates between now and January 14, 2020) https://support.microsoft.com/en-us/help/4528069/update-for-eligible-windows-7-and-server-2008-r2-de...
Note: After activation, you can then continue to use your current update and servicing strategy to deploy ESU through Windows Update, Windows Server Update Services (WSUS) or other update management solutions that you prefer.
Now that all of that is covered, you are faced with deploying the new keys to all the systems that you purchased support for. The key for ESU are Multiple Activation Keys (MAK) and you cannot use KMS auto activate them. The Volume Activation Management Tool (VAMT) is supported for online and proxy activations. If your systems have internet access, then you can leverage ConfigMgr to ensure that the prerequisites and the appropriate ESU keys are in place and activated without VAMT.
You can leverage PowerShell to quickly check if the required patches are installed. For example:
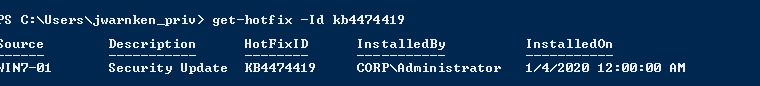
get-hotfix -Id kb4474419
Will quickly determine if the SHA2 code signing patch has been installed.
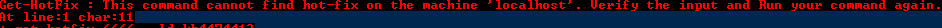
And quickly error out if it is not installed.
You can use that to create a compliance item to check all your systems to determine which have the required patches and which need to have them installed. An example of a compliance item script to check would be
Function lookuphotfix ($Hotfixid)
{
$hotfixResult = Get-HotFix -ComputerName $env:Computername | Where-Object {$_.HotfixID -eq $HotfixID}
if($hotfixResult) {return $true}
}
$strCompliant = "Non-Compliant"
If (lookuphotfix kb4474419 -eq $true){$StrCompliant = "Compliant"} #SHA-2 Update - REQUIRED
write-host $strCompliant
Once all the required prerequisites are in place you can then use a compliance item to deploy the keys. Here links to example of PowerShell scripts to do that, simply add your ESU key to the appropriate $ESUKEY = "<INSERT-ESU-KEY-HERE>" line(s).
In addition to the sample scripts you can also utilize a set of sample configuration items and baselines available on via my GitHub repository
They are available individually or as a zip file
Download the zip file and extract the contents so that you can import the baselines.
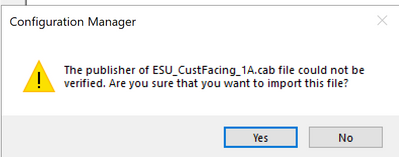
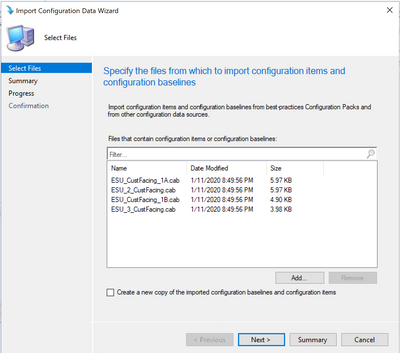
You will be prompted to for each of the baselines that the publisher could not be verified and to confirm that you want to import the files.
After confirming the selection for each of the files you will see 4 cab files to be imported
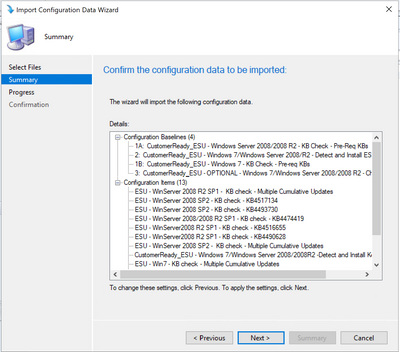
When you select next, you see the detailed list of the configuration baselines and configuration items that will be added.
Select next and then close to complete the import.
The following baselines are intended for use on clients that have Internet access:
- Baseline 1A: This baseline is intended for Server 2008/2008R2 clients, and checks for OS-specific pre-requisite KBs. You can deploy the remediation baseline (Baseline 2, below) to systems that are compliant with this KB check.
- Baseline 1B: This baseline is intended for Windows 7 clients, and checks for Windows 7 pre-requisite KBs. You can deploy the remediation baseline (Baseline 2, below) to systems that are compliant with this KB check.
- Baseline 2: This baseline will detect the state of the ESU key and remediate (Detect & Install ESU Key) if needed. It should be deployed to clients that meet the KB pre-requisites (see baselines 1A and 1B) and it needs to be updated with the your ESU keys before deployment.
- Baseline 3: This checks for an optional KB we released, that is a non-security update. If this update installs successfully, it indicates the client has an installed/activated ESU license.
Update the scripts to include your ESU key(s) and deploy to your systems.
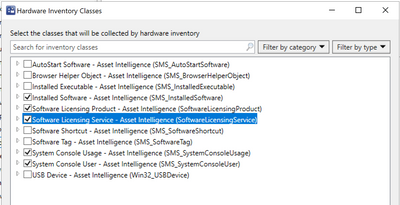
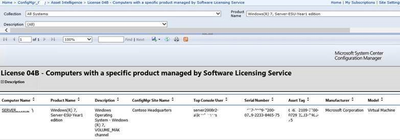
One other item to note is that there are Asset Intelligence reports available that interact with the Software Licensing Service, allowing you to report on ESU keys
Hopefully you will find this helpful and check back in next time when we talk about options for systems without internet connectivity.
Resources
- ITPro FAQ end of support Win 7: https://support.microsoft.com/en-us/help/4527873/itpro-faq-about-end-of-support-for-windows-7
- ESU Lifecycle FAQ: https://support.microsoft.com/en-us/help/4497181/lifecycle-faq-extended-security-updates
- Update to verify eligible Win 7 SP1 devices can get ESUs: https://support.microsoft.com/en-us/help/4528069/update-for-eligible-windows-7-and-server-2008-r2-de...
- Blog: “How to get ESUs for eligible Windows devices” https://techcommunity.microsoft.com/t5/Windows-IT-Pro-Blog/How-to-get-Extended-Security-Updates-for-...
Common Questions
Answers sourced from reference materials as well as confirmed with the Microsoft Product Group where applicable, unless noted as otherwise.
- Q: Is there a work around for Quality Update requirement?
- A:
“There is no work around. This (October or newer monthly rollup) is required – as it was written in the article. “The November 2019 or a later security-only update package can be used as a substitute for the monthly rollup in the Installation prerequisites.
- Q: Do we have to apply the Quality Update moving forward or could be apply security only?
- A: “You can go back to Security Only (for the remaining updates through 14-Jan-2020) after applying the October or newer monthly roll up (in preparation for the ESU) ” (Of course, ESUs will contain only Critical or Important Security updates)
- Q: If we have never installed the Quality Update, do we know how much drive space that will take?
- A: The October Security Monthly Quality Rollup (KB4519976) is 308 MB to download. Applying the update will take a similar amount of space.
- Q: Why isn’t KMS available as a deployment option for ESU?
- A: “KMS is not supported for the ESU MAK process. KMS would have required re-architecting to support ESU. This was determined to be too high of a risk for our enterprise customers and for our Windows development teams. Any work to re-architect KMS would have resulted in considerable instability of Windows Server 2008 R2 at a time when customers need it to be absolutely stable.”
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.