- Home
- Security, Compliance, and Identity
- Core Infrastructure and Security Blog
- Network Security Group Monitoring
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Intro
Brad Watts here to explore monitoring of your Network Security Groups (NSGs). I was approached recently by a customer wanting to better understand changes being made to the many NSGs in their environment. Working with them, we came up with an Azure Workbook that provides a centralized view of both current settings on your NSGs along with any changes that have been made.
Sneek Peak
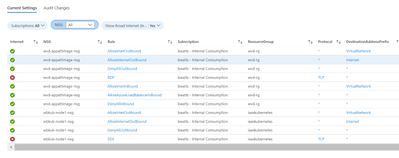
Before we jump into implementation let’s look at the result. Our Workbook has two tabs. The first tab is “Current Settings” and uses Azure Resource Graph to pull in current NSG settings.
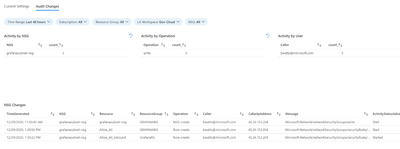
On the “Audit Settings” tab we are focusing on the changes made to NSGs
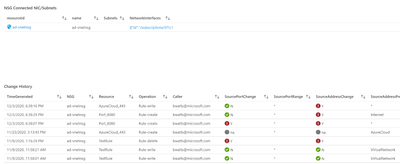
If you select one of the changes from the “NSG Changes” table, it will show you what NIC/Subnet it’s connected to along with all the changes over the last 90 days.
Prerequisites
If your interested in implementing this Workbook you need to be aware of a few requirements:
- Whoever is using the Workbook will need at least read access to the NSGs they are wanting to monitor. This is because we are using Azure Resource Graph to pull this information.
- For the “Audit Change” tab to work you need to send you’re Azure Activity Logs to a Log Analytics Workspace.
Azure Activity log - Azure Monitor | Microsoft Docs
- Whoever is using the Workbook will need to be able to read the data in the Log Analytics workspace that you sent the Azure Activity Logs to.
Implementing
Hopefully, everyone is still interested and want to take a look at this in your environment. Well lets walk through importing the workbook!
Step 1: Get the Workbook
You can find a copy of this workbook in my Github repo. You just need to copy the content of this JSON file to import it.
https://raw.githubusercontent.com/bwatts64/AzureMonitor/master/Workbooks/NSGWorkbook.json
Step 2: Create a Workbook
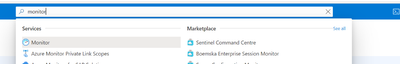
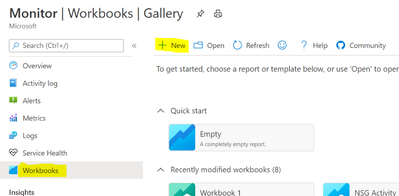
In the Azure Portal bring up Azure Monitor by searching for Monitor
In Azure Monitor select the “Workbook” tab and choose “New”
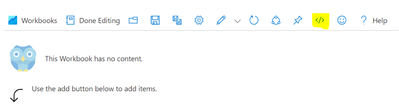
This will open a Workbook in Edit mode. Do to the “Advanced Editor” (</>)
In the “Advanced Editor” paste the content of the JSON file from my GitHub repo and click on “Apply”
That’s it. You know have the Workbook to test in your environment. Make sure you “Save” the workbook and also click on the “Done Editing” to get the full experience.
Summary
Being able to easily visualize both you’re current NSGs along with any changes made to them over time is essential for anyone managing NSGs in Azure. In this solution we are using an Azure Workbook along with Log Analytics and Azure Resource Graph to give you that centralized view. I hope this makes your life easier and please suggest improvements to the Workbook. I always consider these things works in progress! A similar Workbook for Azure Firewalls is in progress.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.