- Home
- Security, Compliance, and Identity
- Core Infrastructure and Security Blog
- Microsoft Defender for Identity - Azure ATP Daily Operation
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Hi IT Pros,
I would like to continue the blog about Microsoft Defender for Identity, this blog article is focused on daily operation. The SecOp Team who traces all attacks against Identities stored in the on-prem Active Directory domain controllers, may find it very much related to operators' work.
It is part 2 of "MD for Identity" topic. Part 1 is about MD for Identity focused on setup and troubleshooting, it could be found here
Please review and give your feedback.
_________________
In Cyber Environment, there is an estimation of 81% breaches originated from compromised identities. With that high level of Identity lost, protecting the privileged accounts and monitoring their activities within Active Directory perimeter is of utmost importance.
The Microsoft Defender for Identity (Azure Advanced Threat Protection) service could serve for that main purpose and should be part of the Corporate 's defender strategy.
Daily operation of Microsoft Defender for Identity is key to identify the identity breaches and identity attacks.
Microsoft Defender for Identity Information integrated with Cloud App Security (CAS) service.
By default MD for Identity is integrated with CAS, account timeline, account activity, assessment information is displayed in Cloud App Security portal under the first column menu items named Dashboard, Investigation, Control and Alert.
The recommendation for CAS portal use includes the following:
- When using Microsoft Defender for Identity service together with Cloud app security service, closing alerts in one service will not automatically close them in the other service. You need to decide where to manage and remediate alerts to avoid duplicated efforts.
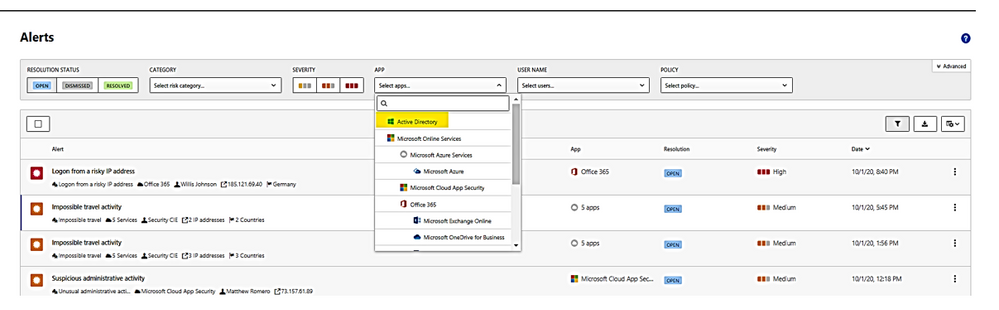
- Microsoft Defender for Identity alerts are displayed within the Cloud App Security Alerts queue. To view, filter alert by app: “Active Directory” as shown:
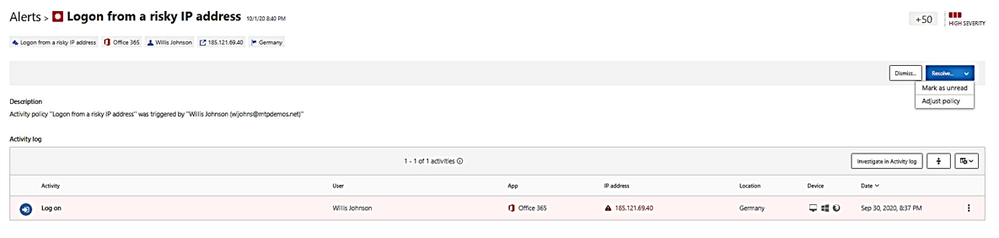
- Alert could be dismissed or resolved as “unread” as “adjust policy.”
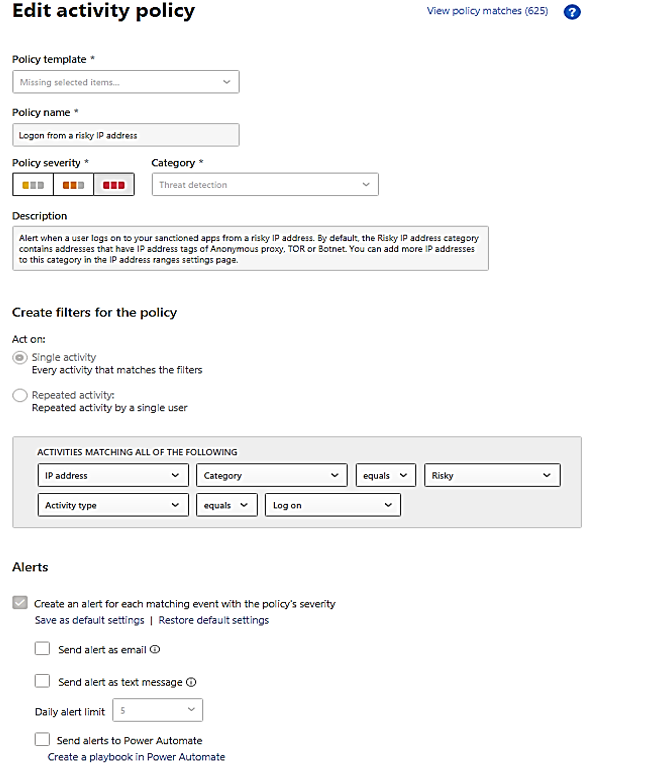
A “Resolve” with action of adjusting policy and make change to policy:
- You could filter alerts by policy, there are about 72 built-in policies plus your custom policies. The identity policies or AD related policies are included in the following table:
|
Policy Name |
Policy Description |
|
Suspicious additions to sensitive groups |
Attackers add users to highly privileged groups. |
|
Suspected skeleton key attack (encryption downgrade) |
Encryption downgrade is a method of weakening Kerberos so password hash could be obtained by hackers. |
|
Suspected brute force attack (LDAP) |
In a brute-force attack, an attacker attempts to authenticate with many different passwords for different accounts until a correct password is found. |
|
Suspected brute force attack (Kerberos, NTLM) |
Same as above |
|
Network mapping reconnaissance (DNS) |
Collect DNS server data which contains a map of all the computers, IP addresses, and services on your network. |
|
Suspicious communication over DNS |
Attackers on an effected computer may abuse the DNS protocol, which is often less monitored and is rarely blocked, |
|
Unusual administrative activity (by user) |
users perform multiple administrative activities in a single session with respect to the baseline learned, |
|
Activity was performed by a terminated user. |
A terminated user performs an activity in a sanctioned corporate application. |
|
Impossible travel |
activities are detected by the same user in different locations within a time period. |
|
Activity from an infrequent country |
activity is detected from a location that was not recently or never visited by the user or by any user in the organization. |
|
Activity from anonymous IP addresses
|
identifies activity from an IP address that has been identified as an anonymous proxy IP address and it may be used for malicious intent. |
|
Unusual, impersonated activity (by user) |
users perform multiple impersonated activities in a single session with respect to the baseline learned, |
|
Unusual file deletion activity (by user)
|
users perform multiple file deletion activities in a single session with respect to the baseline learned, |
|
Multiple failed login attempts |
users perform multiple failed login activities in a single session with respect to the baseline learned, |
|
Multiple storage deletion activities |
users perform multiple storage deletion or DB deletion activities in a single session with respect to the baseline learned. |
|
Risky sign-in |
Azure Active Directory (Azure AD) detects suspicious actions that are related to user accounts. |
|
Suspected DC Shadow attack (domain controller promotion) |
Attackers create a rogue DC and make AD replication it. |
|
Suspected identity theft (pass-the-ticket) |
lateral movement technique in which attackers steal a Kerberos ticket from one computer and use it to gain access to another computer. |
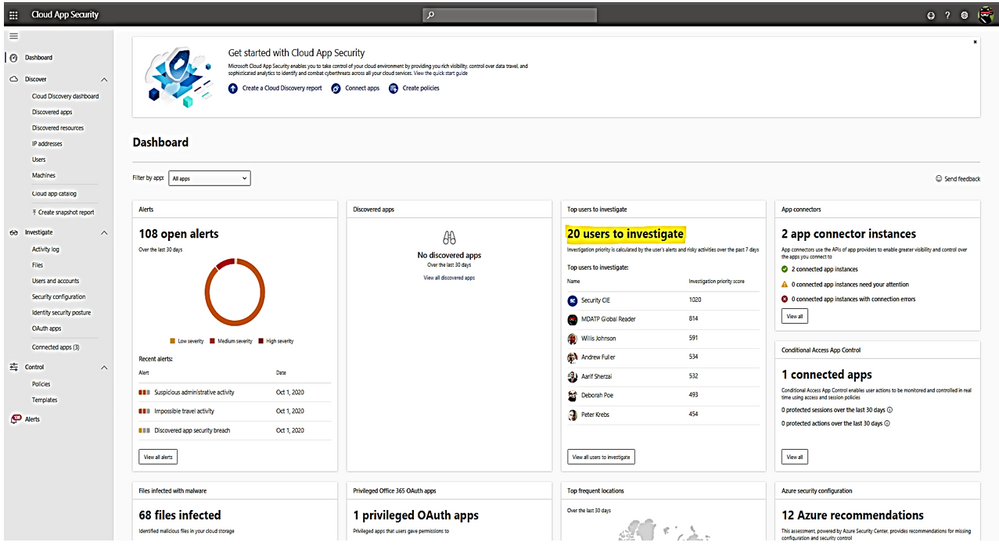
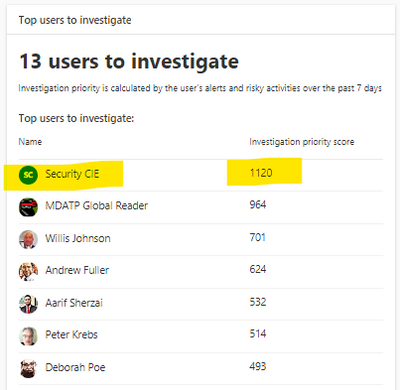
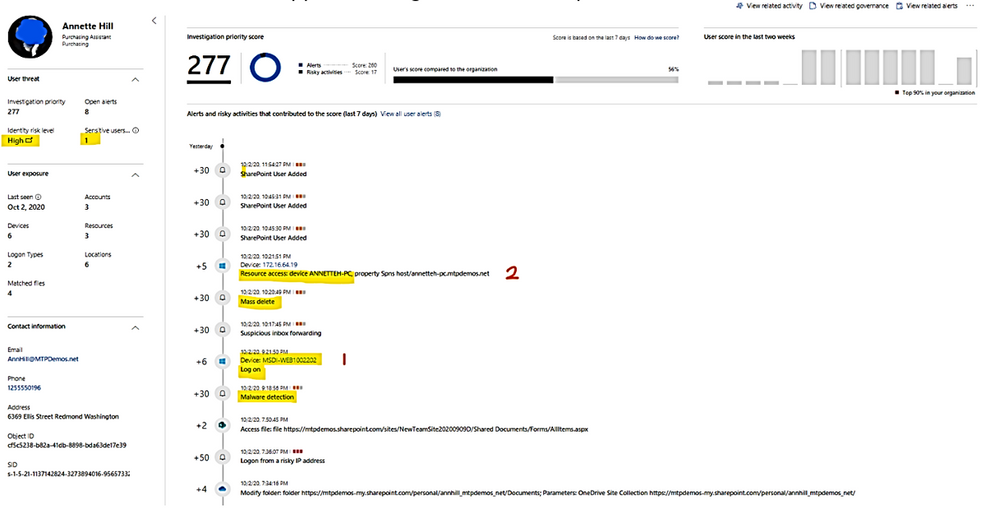
Cloud App Security Dashboard - Investigation Priority Score for Users:
- CAS dashboard shows top users who need to be investigated.
- Evaluated data come from Microsoft Defender for Identity , Microsoft Cloud App Security as well as Azure AD Identity Protection
- Score points are based on security alerts, risky activities, and potential business and asset impact related to each user.
- Calculation is done over a period of 7 days.
Recommended investigation steps for suspicious users
- Choose the “Top users to investigate”.
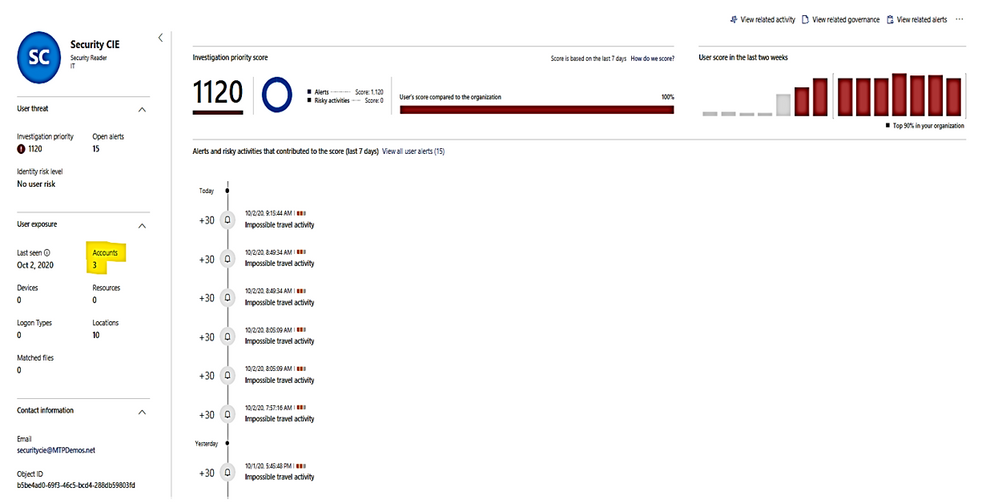
- Investigate a User:
Microsoft Defender for Identity alert evidence and lateral movement paths provide clear indications when users have performed suspicious activities or indications exist that their account has been compromised.
We need to take the following actions:
- Gather information about the user.
- Investigate activities that the user performed.
- Investigate resources the user accessed.
- Investigate lateral movement paths.
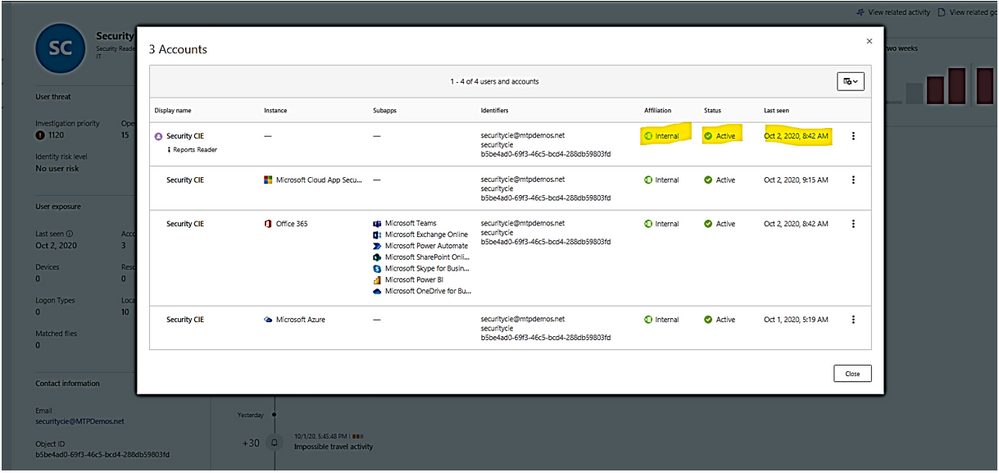
- Who is the user and what are the multiple accounts been used?
- Is the user a sensitive user (such as admin, or on a watchlist, etc.)?
- What is their role within the organization?
- Are they significant in the organizational tree?
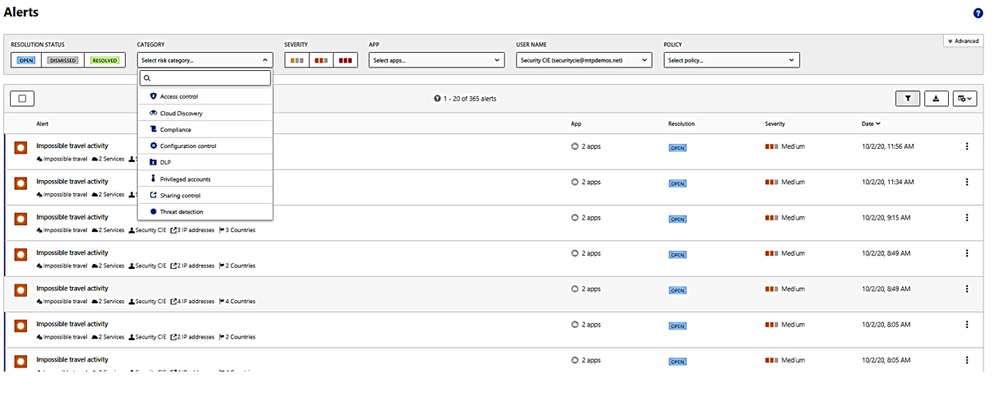
II. Suspicious User’s activities to investigate:
- Does the user have other opened alerts in Microsoft Defender for Identity, or in other security tools such as Windows Defender-ATP, Azure Security Center and/or Microsoft CAS?
The alerts could be filtered and viewed by one or multiple categories included:
- Access control,
- Cloud Discovery (Reconnaissance),
- Compliance, Configuration control,
- DLP (Data Lost Prevention),
- Privileged accounts,
- Sharing control,
- Threat detection.
2. What is the activities done by this User? 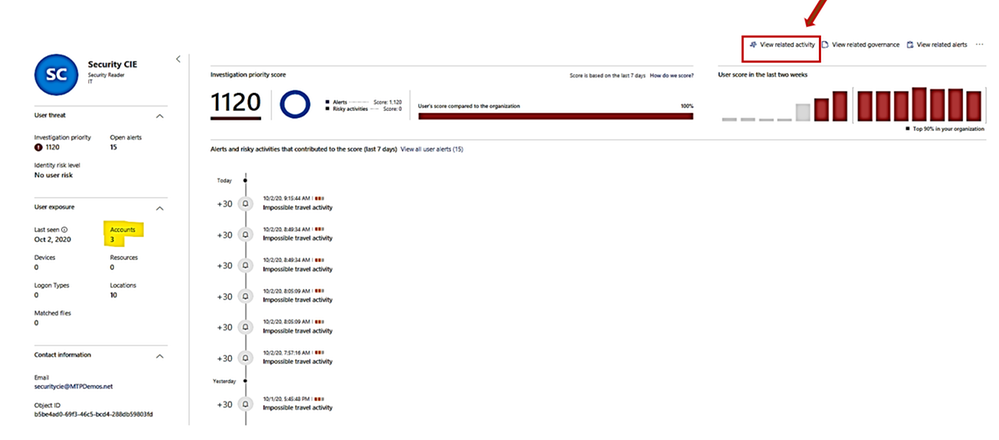
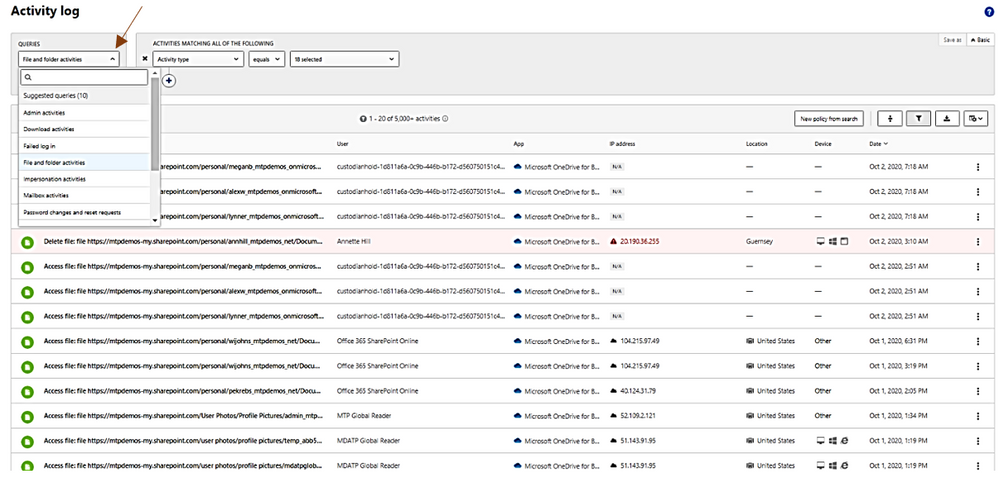
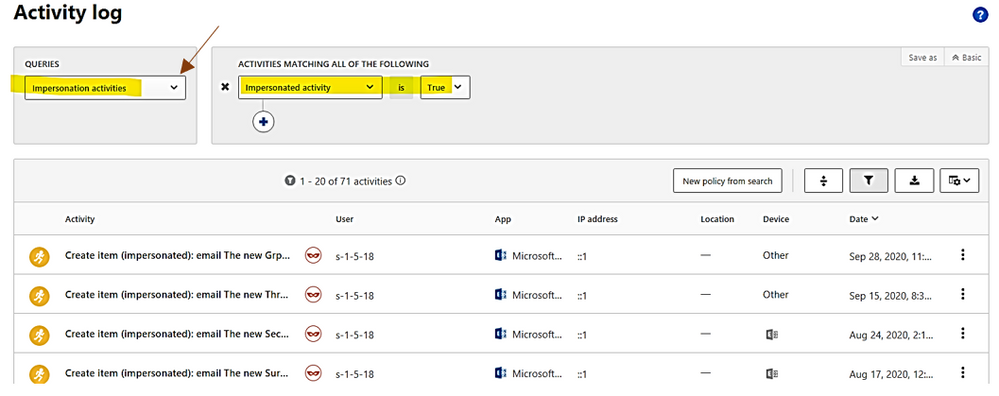
In activities, you could choose the following queries for investigation: Admin activities, Domain activities, Failed log in, File and folder activities, Impersonation activities, Mailbox activities, Password changes and reset requests, Security risk, Sharing activities, Successfully log in, your saved custom query
3. Did the user have multiple failed logon attempts in a brief period?
4. Which resources did the User access to?
5. Did the user access high value resources?
6. Was the user supposed to access the resources they accessed?
7. Which computers did the user log in to?
8. Was the user supposed to log in to those computers?
9. Is there a lateral movement path (LMP) between the user and a sensitive user?
LMP-Impersonate privilege account.
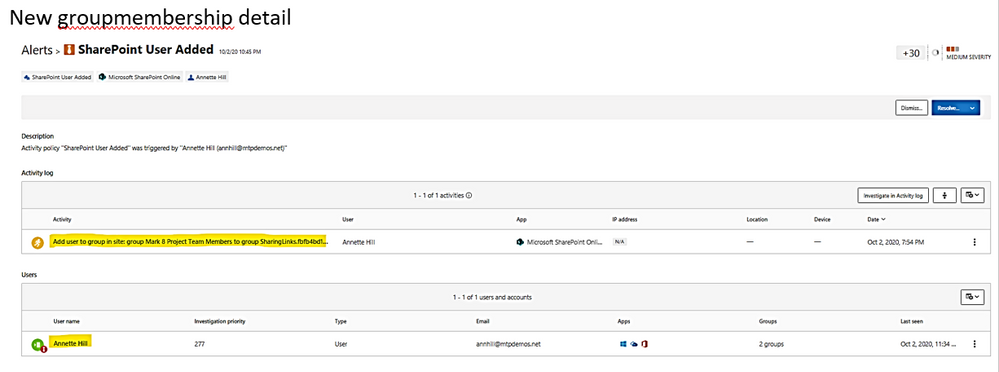
LMP-Suspicious group membership has been changed.
Click on each timeline 1, 2, 3 below to get the group names of which new membership is added.
New groupmembership detail
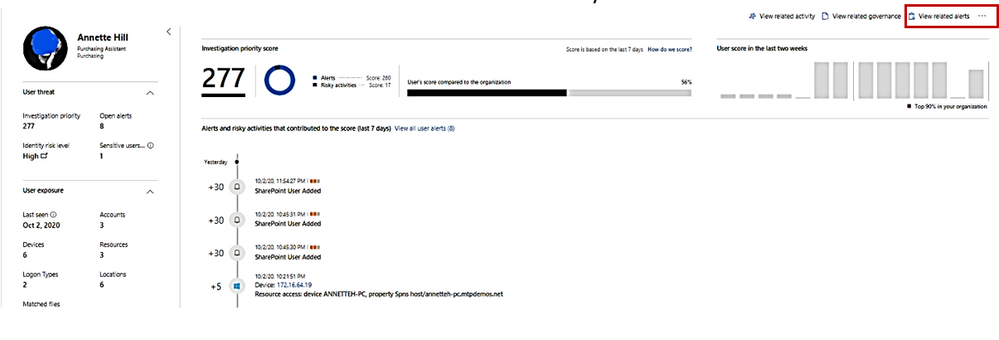
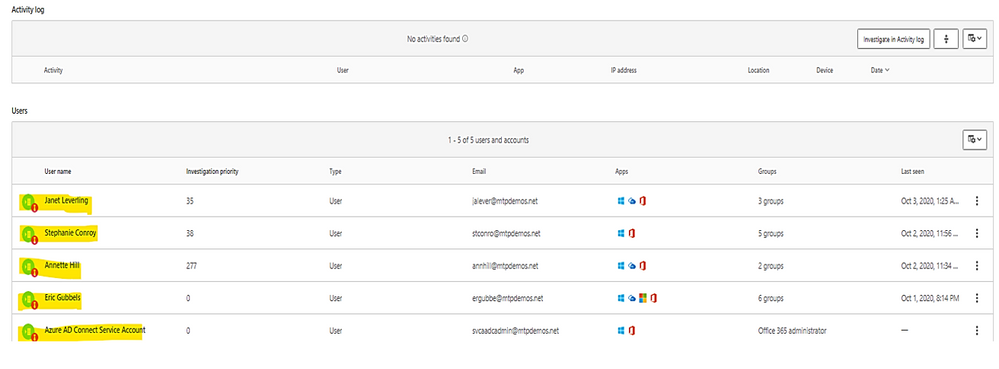
10. View all other alerts about the related User by click on link “view all User alerts”.
All Alerts related to the User.
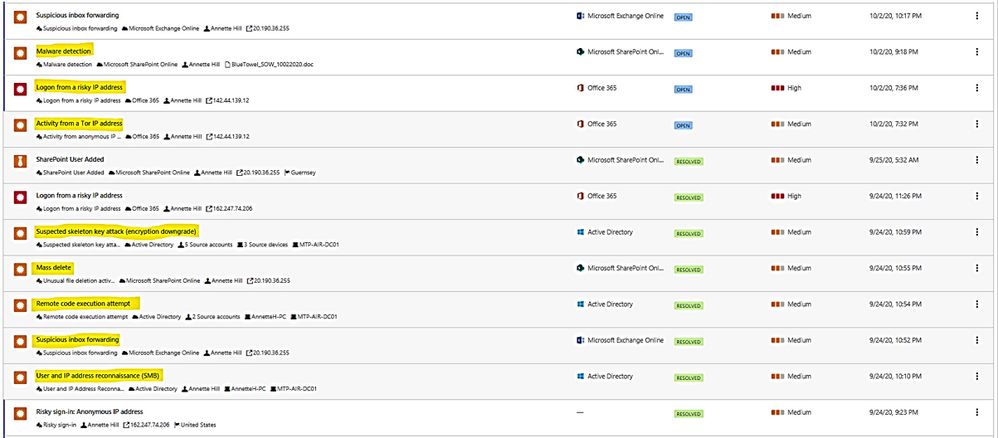
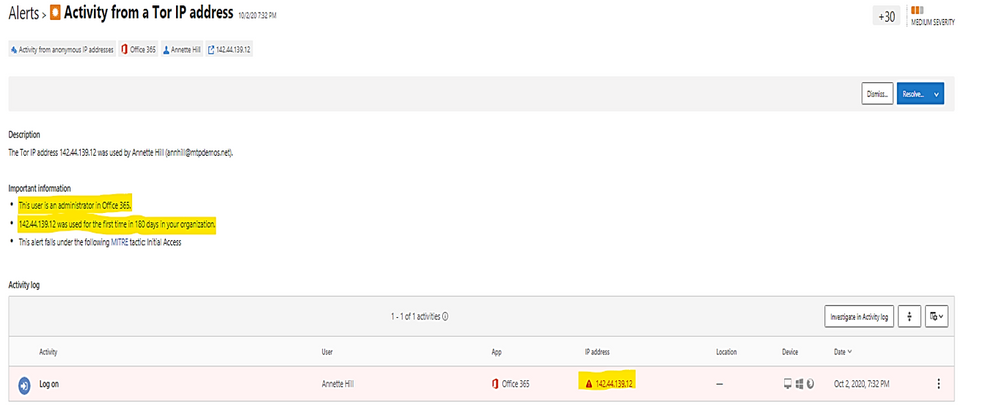
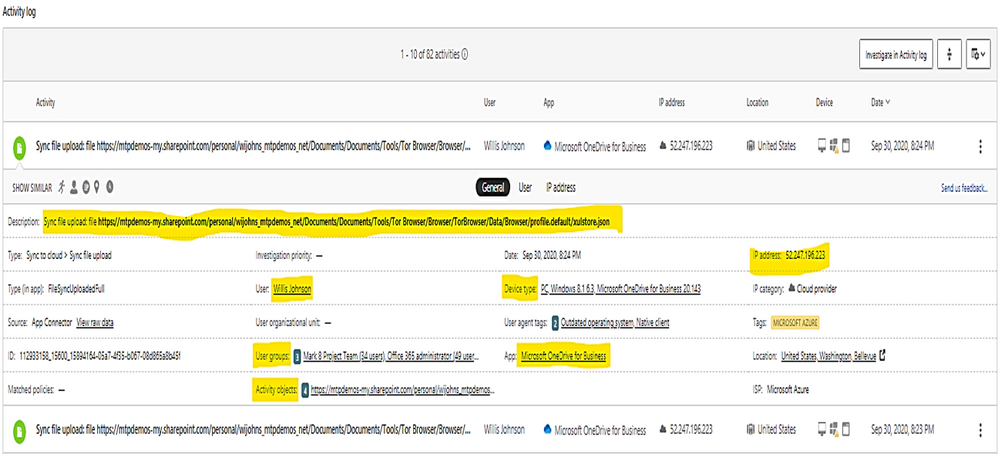
Example: alert on Tor IP address being used
(Tor directs Internet traffic through a free, worldwide, volunteer overlay network consisting of more than seven thousand relays to conceal a user's location and usage from anyone conducting network surveillance or traffic analysis.)
To get all Tor IP, anonymous IP address connection in Alert by using policy filter named “Activity from anonymous IP address.”
Click on each item to get the details.
The details shown the answer to the following questions:
- What are the Tor IP addresses been used?
- Who is the User involved?
- What are the File names been uploaded downloaded to Tor IP address?
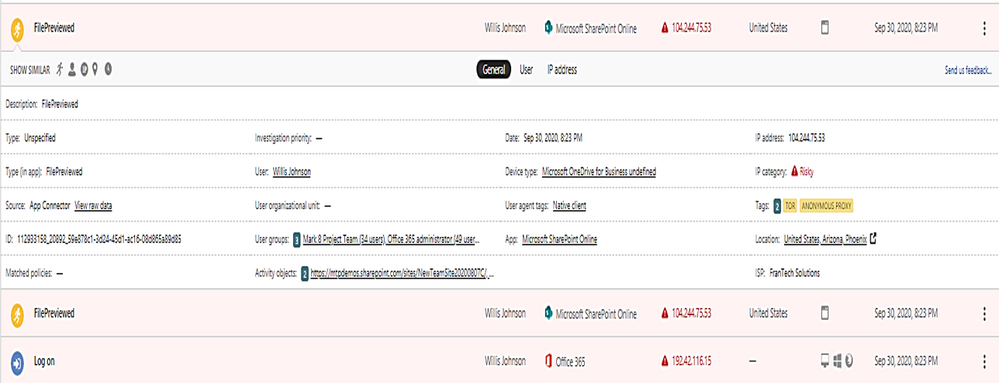
You could do more search by clicking on the following icons:
Example: alert on mass deletion of files:
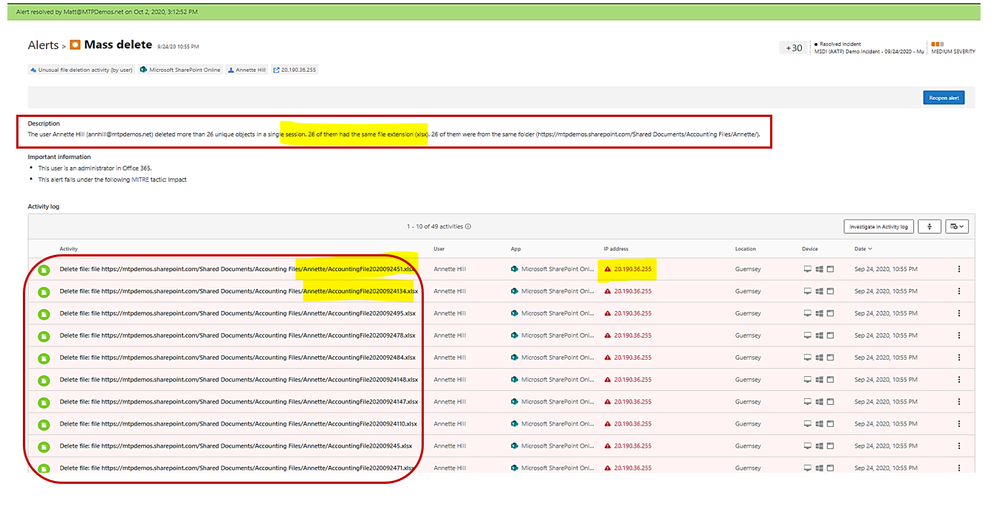
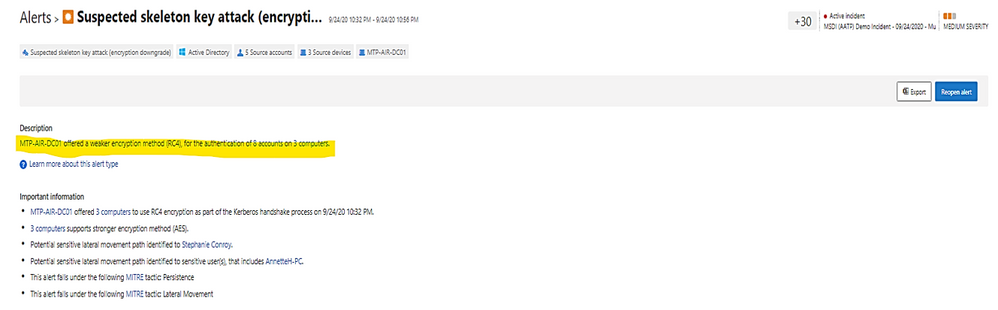
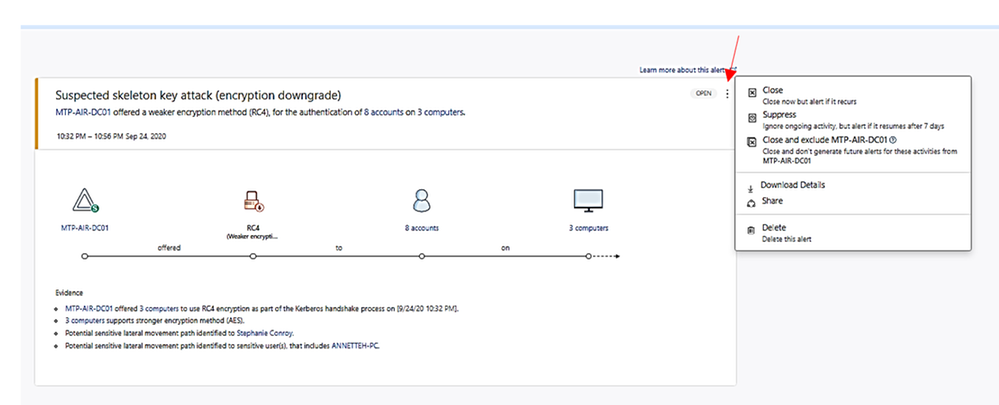
Example: alert on skeleton attack by downgrading encryption method on multiple admin accounts.
(the “Skeleton Key” attack is capable of “unlocking” and providing privileged access to every single employee account within the enterprise. The powerful malware strain allows cybercriminals to bypass Active Directory (AD) systems that only implement single factor authentication.)
In the alert page, the accounts marked with “red tie” icons are internal admin.
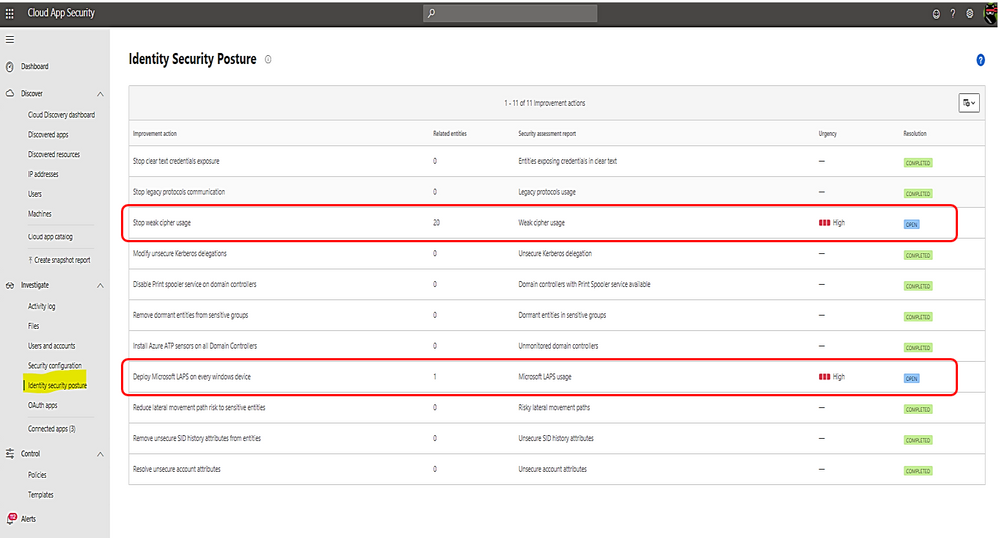
Microsoft Defender for Identity identity security posture:
- Identify misconfigurations and legacy components which represent one of the greatest threat risks to organization.
- Provide links to documents for remediation and preventive action.
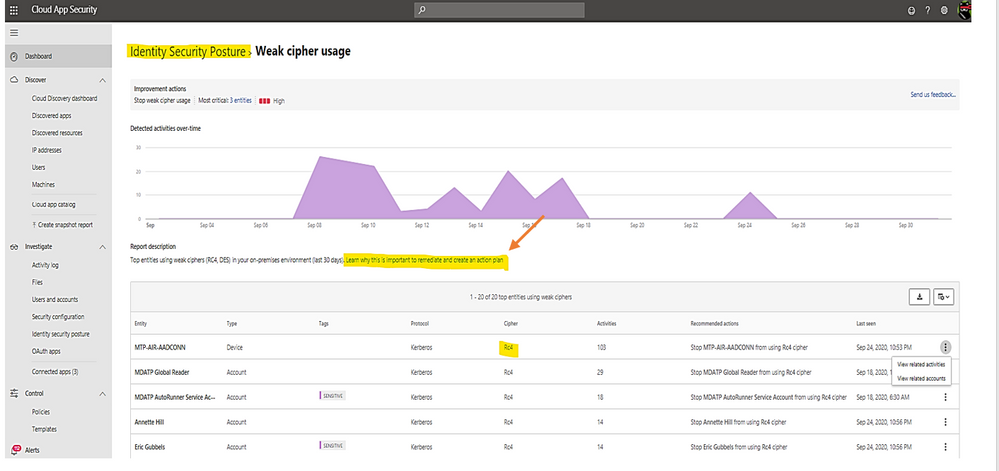
Identity security posture assessment of credentials exposed in clear text, legacy protocol usage, weak cipher usage, unsecure Kerberos delegation, DC with spooler service, sensitive group, rogue DCs, LAPS (Local Administrator Password Solution to be randomized and stored in AD) usage, risky lateral movement paths, unsecure SID history attributes, unsecure account attribute.
Click on any row item marked as “open” to view the posture detail and follow link to the remediated document.
Click on the link to view Microsoft document about the posture and remediation information and then, make a plan for remediation action.
Once you have the remediation solution implemented successfully, Microsoft Defender for Identity portal will automatically mark the related item as “completed” as shown:

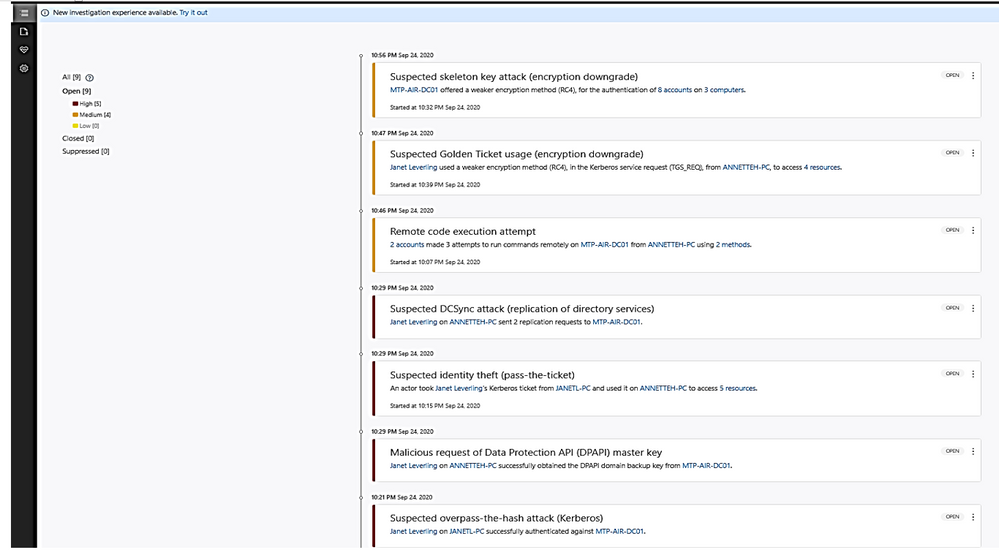
Alerts in Microsoft Defender for Identity’s portal
- Microsoft Defender for Identity security alerts explain the suspicious activities detected within your on-premises network by the sensors installed on domain controllers, and the actors and computers involved in each threat.
- Alert evidence lists contain direct links to users and computers.
- Microsoft Defender for Identity security alerts are divided into the following phases:
Click on the alert item to view detail and decide to close, suppress, exclude DC or delete alert.
- Suppress: Suppressing an activity means you want to ignore it for now, and only be alerted again if there is a new instance.
If there is a newly similar event after seven days, you will be alerted again.
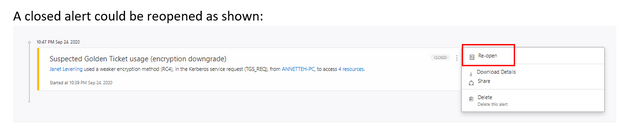
- Reopen: You can reopen a closed or suppressed alert.
- Delete: Alert is deleted from the instance and you will NOT be able to restore it. After you click delete, you will be able to delete all security alerts of the same type.
A closed alert could be reopened as shown:
I hope the information presented in this blog post is useful to your Microsoft Defender for Identity daily operation.
Reference:
AATP alert, Cloud App Security alert
- https://docs.microsoft.com/en-us/azure-advanced-threat-protection/suspicious-activity-guide?tabs=ext...
- https://docs.microsoft.com/en-us/cloud-app-security/monitor-alerts
- https://docs.microsoft.com/en-us/azure-advanced-threat-protection/mcas-integration
End of mainstream support for Azure ATA
Verizon data breach report
- https://www.securelink.com/blog/81-hacking-related-breaches-leverage-compromised- credentials/
Video
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.