- Home
- Security, Compliance, and Identity
- Core Infrastructure and Security Blog
- Microsoft Defender for Endpoint - MD ATP Daily Operation – Part 2
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
NOTE: As of late September, the Microsoft Defender ATP product line has been renamed to Microsoft Defender for Endpoint!
Dear IT Pros,
I would like to continue on Part 2 of the Windows Defender ATP Operation with tasks handled by ATP operators, ATP administrator.
_________________________________________________
Creating Alert Notification
Alert Notification settings are configured for the purpose of sending alert email message to Security Team and other teams.
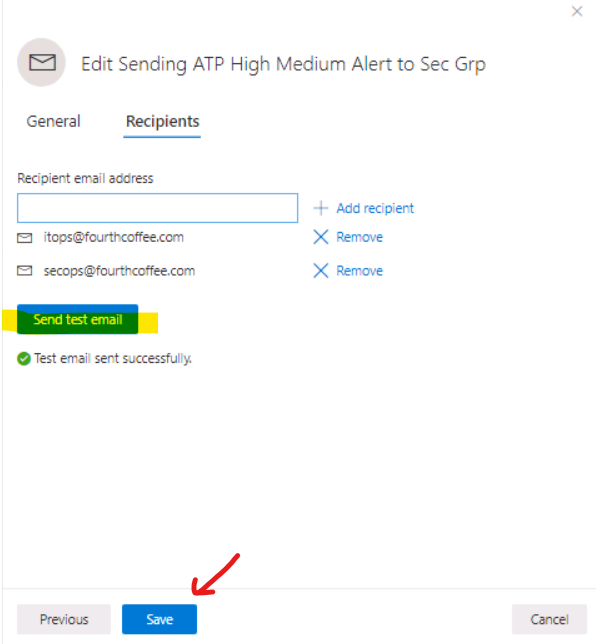
To setup Alert Notification:
- In ATP Portal, go to Settings\General\Alert notification
- Add Item
- Enter Rule name, eg: Sent High Severity Alert to Secops Team
- Choose options: include organization name, include tenant-specific portal link, include device information
- Choose alert severity: High, Medium, Low
- Next,
- Enter Group's email address
- Send test email and Save
Live Response to remote device
Live response gives you the remote access to target device by remote shell connection. It enables security admin to run command, script and collect forensic data, send suspicious entities for analysis, remediate threats, and proactively hunt for emerging threats on the remote device.
To Enable Live Response for ATP devices:
- In ATP Portal, go to Settings\General\Advanced features
- Turn on Live Response
- Turn on (optional) Live Response unsigned script execution
- Save Preferences

To Run Live Response Remote Access to Device:
- Client Prerequisite:
- Windows 10 version 1909 or later.
- For other Windows 10 versions: Make sure to install appropriate updates (live response feature included in these updates).
Windows 10-1903: KB4515384
Windows 10-1809 (RS5): KB4537818
Windows 10-1803 (RS4): KB4537795
Windows 10-1709 (RS3): KB4537816
- The Target Machine is member of a Device Group with Semi or Full Remediation of Automation Level as shown :
For Dynamic Device Group, please refer to "ATP Daily Operation – Part 1" for more detail.
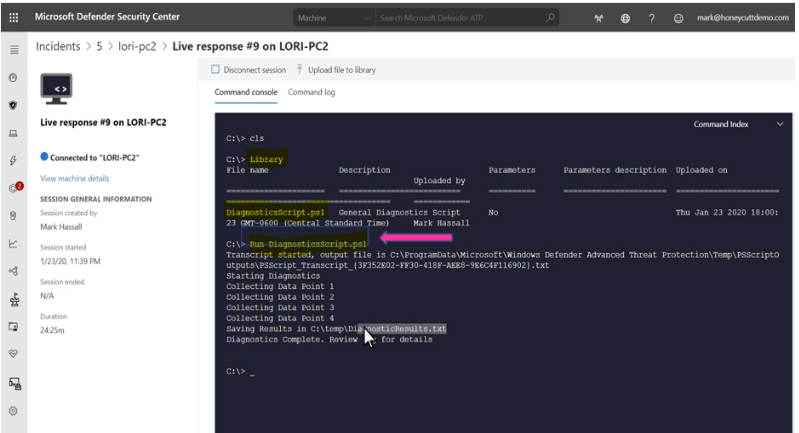
To Run the command or script in live response session.
In live response session, you could run one of the commands in the following table of commands:
|
Command |
Description |
|
cd |
Changes the current directory. |
|
cls |
Clears the console screen. |
|
connect |
Initiates a live response session to the device. |
|
connections |
Shows all the active connections. |
|
dir |
Shows a list of files and subdirectories in a directory. |
|
download <file_path> & |
Downloads a file in the background. |
|
drivers |
Shows all drivers installed on the device. |
|
fg <command ID> |
Returns a file download to the foreground. |
|
fileinfo |
Get information about a file. (10GB max size limit) |
|
findfile |
Locates files by a given name on the device. |
|
help |
Provides help information for live response commands. |
|
persistence |
Shows all known persistence methods on the device. |
|
processes |
Shows all processes running on the device. |
|
registry |
Shows registry values. |
|
scheduledtasks |
Shows all scheduled tasks on the device. |
|
services |
Shows all services on the device. |
|
trace |
Sets the terminal's logging mode to debug. |
Advanced commands
The following advanced commands are for the user roles that are granted the ability to run advanced live response commands such as ATP Administrator Role:
|
ADVANCED COMMANDS |
|
|
Command |
Description |
|
analyze |
Analyses the entity with various incrimination engines to reach a verdict. |
|
getfile |
Gets a file from the device. (3GB max size limit) |
|
run |
Runs a PowerShell script from the library on the device. |
|
library |
Lists files that were uploaded to the live response library. (250MB max size limit) |
|
putfile |
Puts a file from the library to the device. Files are saved in a working folder and are deleted when the device restarts by default. |
|
remediate |
Remediates an entity on the device. The remediation action will vary depending on the entity type: |
|
undo |
Restores an entity that was remediated. |
To run Powershell Script in live response:
The library stores files (such as scripts) that can be run in a live response session at the tenant level. PowerShell scripts must first be placed in the library before you can run them.
Upload the script file in the library and run script
Click Upload file to library.
- Click Browse and select the file.
- Provide a brief description.
- Specify if you'd like to overwrite a file with the same name.
- If you'd like to be known what parameters are needed for the script, select the script parameters check box. In the text field, enter an example and a description.
- Click Confirm.
- (Optional) To verify that the file was uploaded to the library, run the library command.
- Run the script with command: Run scriptname.ps1
Cancel a command
Anytime during a session, you can cancel a command by pressing CTRL + C.
Using this shortcut will not stop the command in the agent side. It will only cancel the command in the portal.
Automatically run prerequisite commands
Some commands have prerequisite command’s to run parallelly. If you don't run the prerequisite command, you would get an error. For example, running the download command without fileinfo will return an error.
You can use the auto flag to automatically run prerequisite commands,:
getfile c:\Users\user\Desktop\work.txt -auto
Apply command parameters
When using commands that have prerequisite commands, you can use flags:
<command name> -type file -id <file path> - auto
Supported output types
Live response supports table and JSON format output types. For each command, there's a default output behavior. You can modify the output in your preferred output format using the following commands:
- -output json
- -output table
Note
Fewer fields are shown in table format due to the limited space. To see more details in the output, you can use the JSON output command so that more details are shown.
View the command log
Select the Command log tab to see the commands used on the device during a session. Each command is tracked with full details, ID, Command line, Duration, Status and input or output side bar
Examples:
- Analyze a file
analyze file "C:\Users\CMAdmin.FourthCoffee\Downloads\KnownMalicious.exe"
- Analyze File in remote machine and Auto Download to local Workstation in the “Downloads” Folder:
analyze -type file -id C:\Users\CMAdmin.FourthCoffee\Downloads\KnownMalicious.exe -auto > AnalyzedKnownMalicious.txt
- Remediating a file (delete file)
C:\>remediate -type file -id C:\Users\CMAdmin.FourthCoffee\Downloads\FreeVideo.exe -auto
or
C:\>remediate file C:\Users\CMAdmin.FourthCoffee\Downloads\FreeVideo.exe -auto
- To download file from the remote target device to your local workstation
C:\getfile "C:\Users\CMAdmin.FourthCoffee\Downloads\FreeVideo.exe" -auto
or
C:\> download "C:\Users\CMAdmin.FourthCoffee\Downloads\FreeVideo.exe" -auto
- To list on connection of the remote target device
C:\> connections
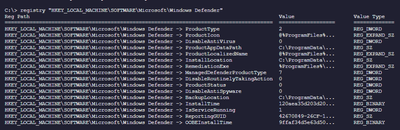
- To list the registry key and value of the remote target device
C:\> registry "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender"
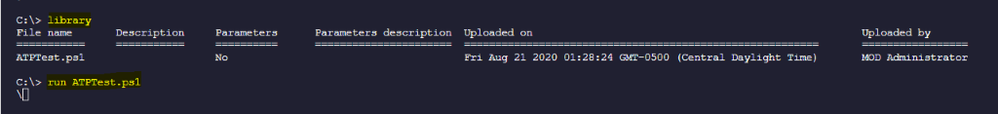
- Creating a test script, upload to Library and run script:
Example: creating ATPTest.ps1 with the following content:
Dir c:\users\CMAdmin.Contoso.com\downloads > C:\temp\dowload_files.txt
Upload script named “ATPTest.ps1” to Library and run the script
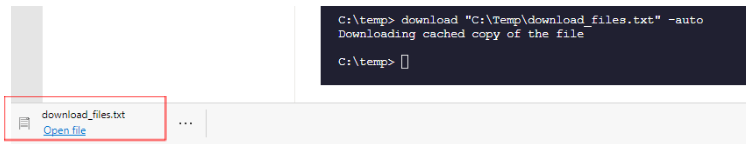
Download result of run content to your local workstation under “downloads” folder
Download “C:\Temp\download_files.txt” -auto
I hope the information is useful to your daily ATP operation monitoring.
Cheer!
References:
Live Response Investigation:
Video about Live Response
__________________________
Disclaimer
The sample scripts are not supported under any Microsoft standard support program or service. The sample scripts are provided AS IS without warranty of any kind. Microsoft further disclaims all implied warranties including, without limitation, any implied warranties of merchantability or of fitness for a particular purpose. The entire risk arising out of the use or performance of the sample scripts and documentation remains with you. In no event shall Microsoft, its authors, or anyone else involved in the creation, production, or delivery of the scripts be liable for any damages whatsoever (including, without limitation, damages for loss of business profits, business interruption, loss of business information, or other pecuniary loss) arising out of the use of or inability to use the sample scripts or documentation, even if Microsoft has been advised of the possibility of such damages.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.