- Home
- Security, Compliance, and Identity
- Core Infrastructure and Security Blog
- Configure Selective Password Synchronization With AADConnect
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Namaste everyone, my name is Varun Kohli, I am an Identity and Security Consultant at Microsoft Services, India.
Through this blog I would like to share details about how we can configure AADConnect to synchronize password hashes to Azure AD for a specific set of people.
UPDATE (3/17/21): The product group has released guidance on selective password hash synchronization, and it can be found here: Selective Password Hash Synchronization for Azure AD Connect
Problem Statement:
We generally see two sets of customers, the first who want to use the modern identity for cloud applications and have decided to synchronize the hashes from on-premise identity systems (Active Directory) and the second who are not comfortable with password hash synchronizations to public cloud and hence use the traditional methods for accessing the cloud applications like ADFS.
This blog especially focuses on the 2nd set of customers who would like to take a gradual approach to modern identity and would like to start slow in their adoption by only targeting a small set of users for synchronizing password hashes.
For instance, in some cases customers may like to have password hashes on Azure AD but only for some set of users. There are many use cases for these scenarios, for e.g. supporting Kerberos based applications in Azure AD or in the lift and shift migration approach for cloud applications. e.g. see Use Enterprise Security Package in HDInsight
The password hash synchronization method provides many advantages and enables the applications for Modern cloud identity. See How password hash sync works
Approach:
For users whose password hash need to be synchronized to Azure AD, we’ll use the ‘adminDescription’ AD attribute as filter. In this example, we will synchronize the password hash when user’s ‘adminDescription’ value equals ‘SyncHash’.
We will create two custom synchronization rules in AADConnect, one that will synchronize users along with their password hashes, and the other that will synchronize users but not their password hash. The default rule with password sync enabled will be disabled.
Highly recommend to first implement this in Dev/Test environment.
Change Summary:
Summarizing all activities that you’ll need to perform to configure AADConnect for selective password hash sync:
- Disable default synchronization rule with password hash sync enabled
- Create custom sync rule that will synchronize users to Azure AD with password hashes
- Create custom sync rule that will synchronize users to Azure AD without password hashes
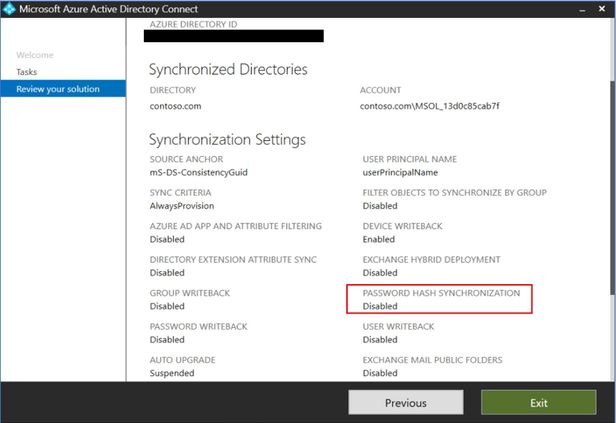
- Enable password hash sync through AAD Connect configuration wizard.
- Validate password sync.
Steps to configure AADConnect for selective password sync:
- On the AADConnect server, validate Password Hash Sync is disabled before making this change
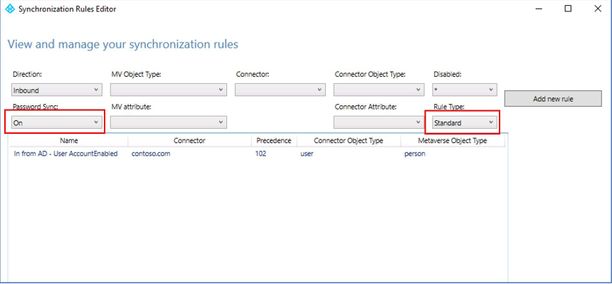
- Open Synchronization Rules Editor and select view filter as ‘Password Sync’ is ‘On’ and ‘Rule Type’ ‘Standard’
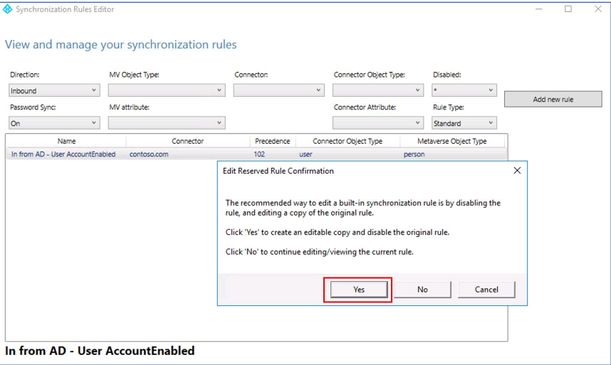
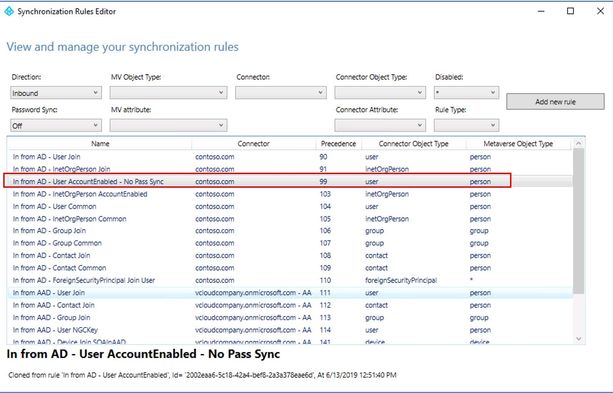
- Select ‘In from AD – User AccountEnabled’ rule and click ‘Edit’. A popup will show up suggesting creating an editable copy and disable the original rule. Click ‘Yes’
- First, we’ll configure sync rule without password hash sync.
- Provide name to this custom rule e.g. ‘In from AD - User AccountEnabled - No Pass Sync’.
- Change precedence to ‘99’ or whatever minimum available value.
- Keep both ‘Enable Password Sync’ & ‘Disabled’ checkboxes unchecked and click ‘Next’
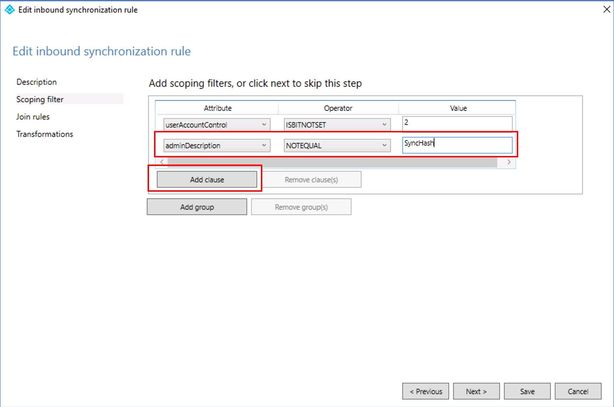
- At ‘Scoping filter’ screen, click ‘Add clause’ and select ‘adminDescription’ NOTEQUAL ‘SyncHash’. Click ‘Next’
- No changes required on ‘Join Rules’ and ‘Transformations’ screen. Click on ‘Save’
- New custom rule with No Password Hash sync will be created.
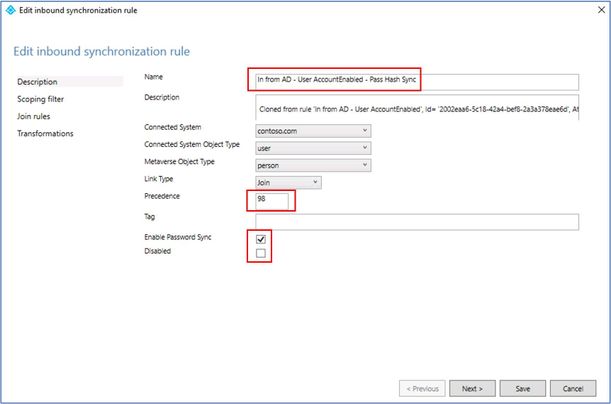
- Now we’ll create another custom rule but with Password Hash Sync enabled. Again, look for ‘In from AD – User AccountEnabled’ standard rule, select the rule then click on ‘Edit’. Click ‘Yes’ when prompted to create new rule.
9. Create custom rule with password hash sync enabled.
- Provide name e.g. ‘In from AD - User AccountEnabled - Pass Hash Sync’.
- Change precedence to ‘98’ or whatever minimum available value.
- Select ‘Enable Password Sync’ checkbox and click ‘Next’
- At ‘Scoping filter’ screen, click ‘Add clause’ and select ‘adminDescription’ EQUAL ‘SyncHash’ and click ‘Next’
11. No changes required on ‘Join Rules’ and ‘Transformations’ screen. Click on ‘Save’
12. Make sure you have just one rule enabled with Password Sync. We’ll keep standard rule ‘In from AD - User AccountEnabled’ as disabled to have password hash flow only from the custom we created above.
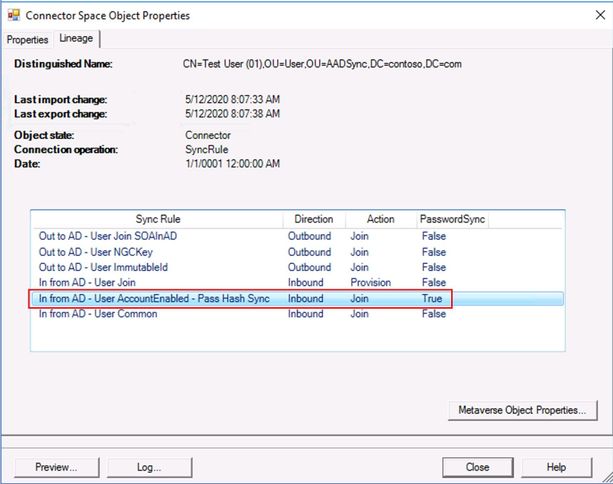
13. To validate that custom rules are getting applied, perform ‘Full Sync Preview’ for random users with and without ‘adminDescription’ flag updated.
14. Users with ‘AdminDescription’ equals ‘SyncHash’ should have ‘Pass Hash Sync’ rule getting applied.
15. Users with no ‘AdminDescription’ flag set should have ‘No Pass Sync’ rule getting applied.
16. After validating through Full Sync preview, execute Full Sync Cycle to let new custom rules commit for all users.
Start-ADSyncSyncCycle -PolicyType Initial
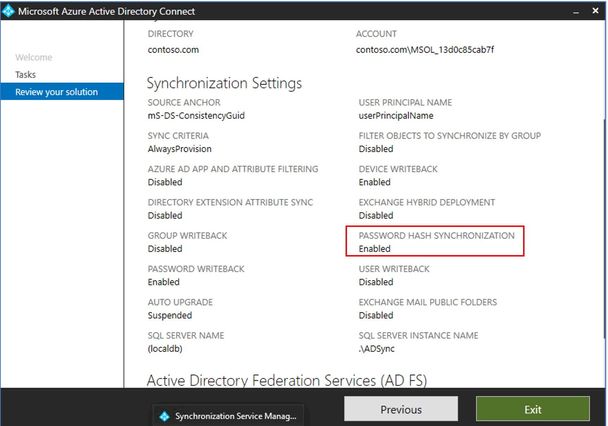
17. After the Full Sync is completed, validate that the custom rules got applied for all users. At this point, you can enable password hash sync through AAD Connect configuration wizard.
18. To confirm users with ‘adminDescription’ flag set only are getting their password synched to Azure, look for following event logs on AAD Connect server.
|
Event ID |
Event Sample |
Cause |
|
656 |
Password Change Request - Anchor : H552hI9GwEykZwof74JeOQ==, Dn : CN=Viola Hanson,OU=Cloud Objects,DC=contoso,DC=local, Change Date : 05/01/2013 16:34:08 |
Password synchronization indicates that a password change was detected and tries to sync it to Azure AD. This identifies the user or users whose password changed and will be synced. Each batch contains at least one user and at most 50 users. |
|
657 |
Password Change Result - Anchor: eX5b50Rf+UizRIMe2CA/tg==, Dn : CN=Viola Hanson,OU=Cloud Objects,DC=contoso,DC=local, Result : Success. |
Users whose password successfully synced. |
Other References:
AADConnect Password Sync Events
Thanks for reading! I hope this helps you on your Azure and Azure AD journey!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.