- Home
- Security, Compliance, and Identity
- Core Infrastructure and Security Blog
- Azure Monitor - Alert Notification via Teams
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Hi there, Bruno Gabrielli here again to talk about how to get alert notification using a Teams channel.
I apologize because this is going to be a long post with all the steps to achieve the notification goals, so please bear with me if you’re interested in getting the configuration done.
Lots of customers are using Teams channel as notification mechanism in their alert management process. They find it very helpful because Teams can be used over mobile devices and browsers without relying on your company laptop. Apparently, there’s no built-in activity in Azure Monitor out of the box to notify an alert via Teams, but we DO have all the pieces that we need.
In this post I will drive you through the Azure Monitor configuration which is behind the Teams channel alert notification mechanism.
First and foremost, a Teams and a Teams channel need to exist. We will not cover this part since it is out of scope, however, should you need information on how to accomplish the pre-requisites you can rely on the following articles:
- Create a team from scratch at https://support.microsoft.com/en-us/office/create-a-team-from-scratch-174adf5f-846b-4780-b765-de1a0a...
- Create a channel in Teams at https://support.microsoft.com/en-us/office/create-a-channel-in-teams-fda0b75e-5b90-4fb8-8857-7e102b0...
With that said, here we are with some steps that will be completed in the Azure portal. Let’s see them in detail.
Step 1: Create a blank Logic App
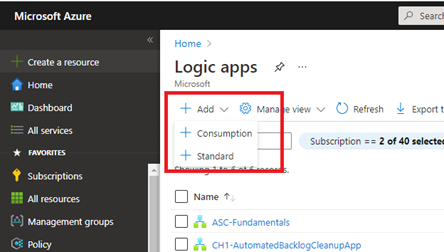
For this step, you need to login to the Azure portal and create a new Logic App. For the purpose of this article, I decided to name it SendAlertNotificationToTeamsChannel, but you can choose the name you prefer the most and according to the company standard you have in place.
- Once you’re in the right place, click on the Add menu and select the Logic App type you want to create. The available types are: Standard and Consumption. You can find all the necessary info in the page Pricing and billing models for Azure Logic Apps at https://docs.microsoft.com/en-us/azure/logic-apps/logic-apps-pricing
- Once you have selected the billing model that best suite your needs, you will be presented with a page in which you will select/enter basic initial information, such as:
- Subscription
- Resource Group
- Logic App name
- Region
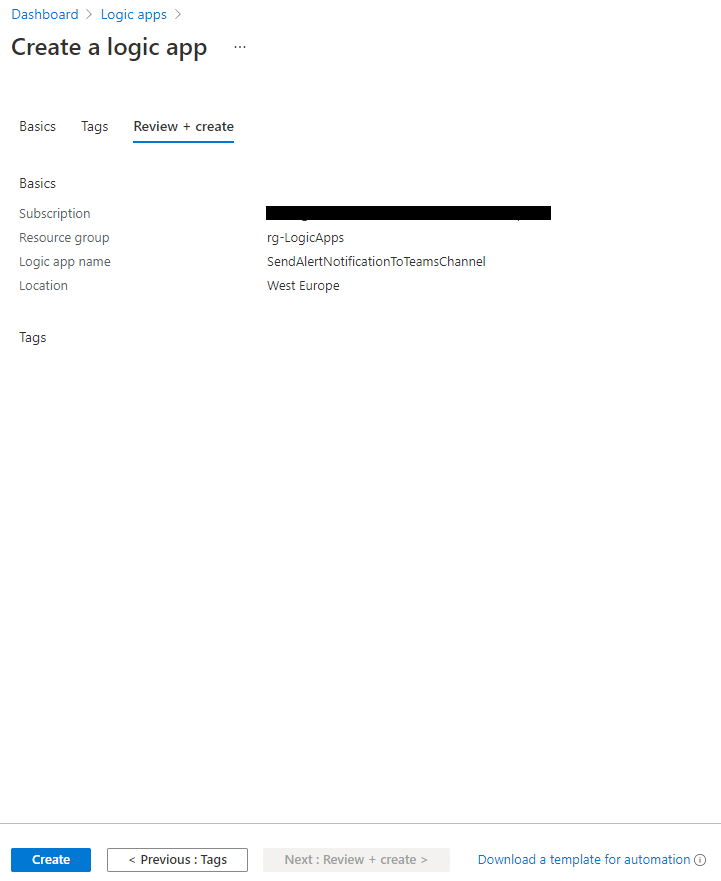
- As you can see from the above screenshot, you can also choose to associate the Logic App with an ISE and or to enable Log Analytics for observability purpose (which is always recommended). Specify the Tags if used and then click on the Review + create button. Once the validation process has finished click on the Create button.
- The deployment of a new Logic App will start. Once completed click on the Go to resource button to get redirected on the newly created Logic App designer page for editing.
Step 2: Configure the Logic App
- In the Logic App designer page, click on When a HTTP request is received. This will be our trigger.
- After the selection, you will be presented with the Logic App designer canvas. This is where we will do all our remaining configurations starting with the trigger activity we just added.
- Configure the activity with the JSON schema that the trigger will use. Since the request will contain the alert’s JSON payload, you can refer (and use) the sample schema you can find in the article Common alert schema definitions at https://docs.microsoft.com/en-us/azure/azure-monitor/alerts/alerts-common-schema-definitions .Copy the sample alert payload from the page, click on Use sample playload to generate schema, paste the content and click Done
- Now let’s have some fun with the notification formatting. Since I preferred to create different activities to notify specific information according to the type of alert (i.e., Metrics, Log Analytics or Application Insight alerts), I created 3 separate but similar activities which differ only in some parts that are related in the information to be sent. If you prefer having just one notification activity for all alert type, jump to step 7
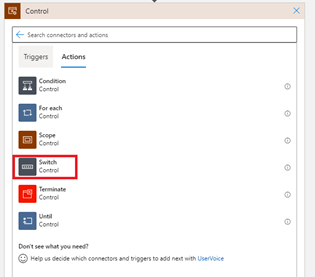
- To create a condition used to decide which notification activity to use, click on the New Step, in the search box type Control
- Select the Control group and then select the Switch activity to add it to the canvas. For groups with lots of activities, you can enter the activity name or part of it in the search box.
- To configure this activity:
- Click on the On field and select monitoringService from the Dynamic content list
- Click on the Equals and enter the string corresponding to the alert type you’re going to create the notification for. For the possible values to be used you can refer at the samples in the Common alert schema definitions at https://docs.microsoft.com/en-us/azure/azure-monitor/alerts/alerts-common-schema-definitions located under the Alert context paragraph. In this example we will use the Metric alerts (excluding availability tests) section, hence as value we will enter Platform.
- If you like to configure specific notification activities, click on the +sign between the 2 blocks and add a new case and configure it accordingly (for configuration step, refer to step b above) or add the notification activity as a new action inside the specific case (see next steps)
- Click on the On field and select monitoringService from the Dynamic content list
- Now we can move on with the notification activity. As we did for the Switch action, click on New step (or click on Add an action if you’re adding it as a child action as result of choice made during step 4)
- Follow what has been described in steps 5 and 6 using Microsoft Teams as group and Post a message (V3) (Preview) as action
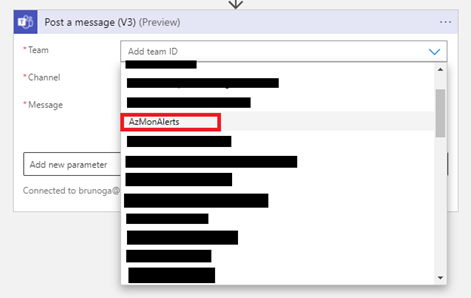
- Once added, this activity needs some configuration:
- Team ID
- Channel
- Message
- As far as the Team ID and the Channel go, you can select them from a drop-down list
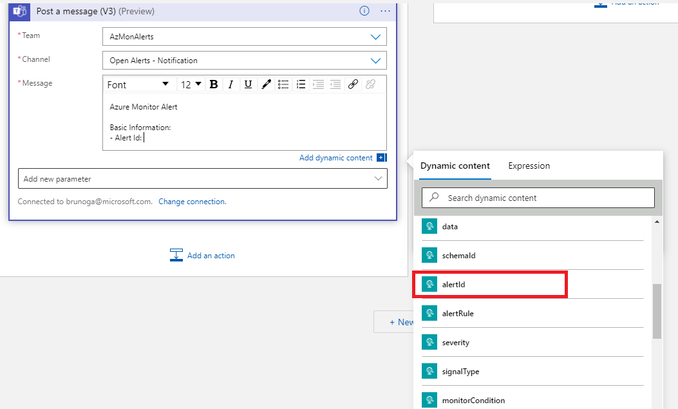
- With regards to the Message body part, this is representing the information sent through the notification. Here you can enter static text formatted as you like, dynamic content as well as formulas. In my example I started with a kind of title and followed with sections under which there are the info I wanted to send. For the static text, you just need to write it. For the dynamic content and/or formulas, once you decided the line where to put it, click on Add dynamic content and select it from the side panel click in the Message canvas and either select it from the Dynamic content list or assemble it using the Expression builder
In this post, since I got everything correctly parsed from the trigger activity (the When a HTTP request is received), I will go use the dynamic content only. For instance, after heving put some text like – Alert Id: I will select alertId content from the list
- Repeat the above step for all the field you want to make part of the message such as Alert Rule Name, Severity, Description, etc.
- As far as the Team ID and the Channel go, you can select them from a drop-down list
- Once the activity configuration is complete, repeat the steps 8, 9 and 10 if you want to add more specific notification activity or click on Save when done.
Step 3: Configure the Action Group
Now that the Logic App has been created, we need to configure an Action Group to use it in order receive our alerts as expected.
From the Azure Monitor blade, follow the steps below:
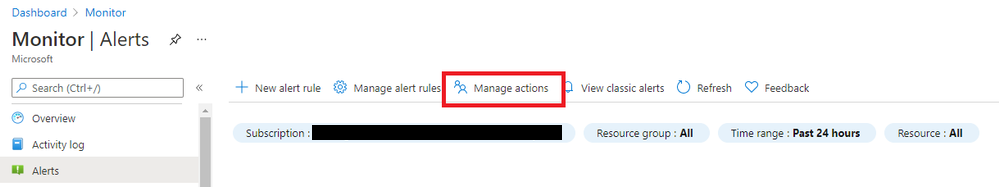
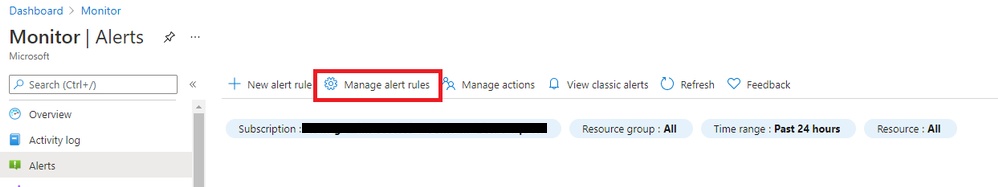
- From the Alerts page, click on Manage actions
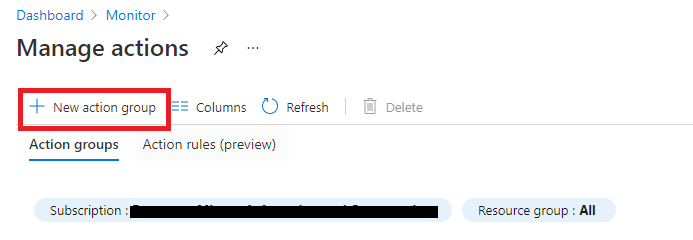
- Click on New action group
- Enter the necessary basic information and click on Next: Notifications >
- Subscription
- Resource group
- Action group name
- Display name
- Leave everything unchanged click on Next: Actions >
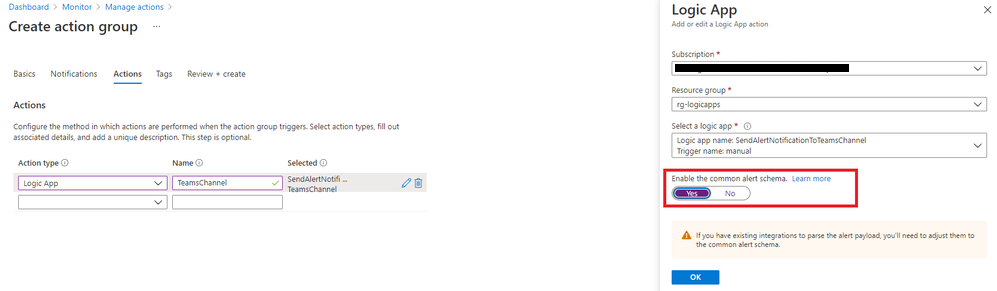
- Configure the following according to what has been created before:
- Action type
- Name
- Selected
, making sure to enable the common alert schema and select
- Click on Next: Tags >and configure the Tags if necessary. Then click on Next: Review + create >and the on Create
Step 4: Add the new action group to your alerts
Now that we have the Action group created and configured, we need to add it to all the alerts we want to notify:
- From the Alerts page, click on Manage alert rules
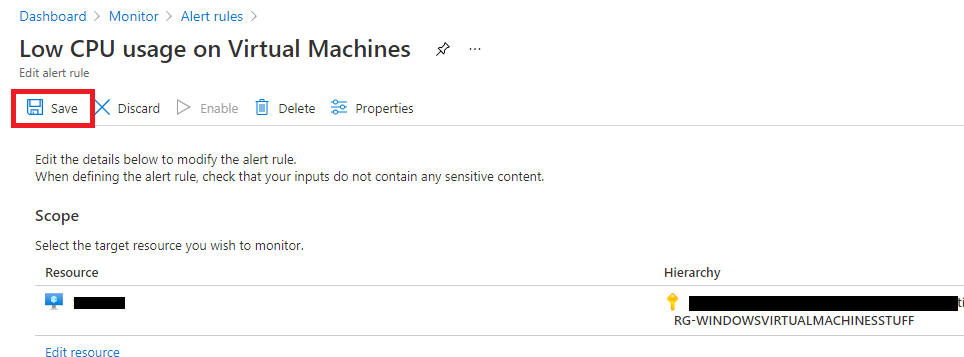
- Identify the alert you want to notify (i.e., the Low CPU usage on Virtual Machines) and click on it to edit
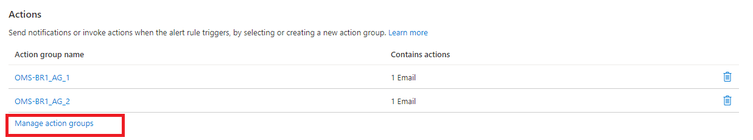
- In the Actions section, add the new action group to the existing one (or remove them if not necessary anymore) by clicking on the Manage action groups
- Select the newly created (and de-select the selected ones if necessary) and click Select
- Click Save to save and apply the changes
Step 5: Test, test, test
As always when re-using something from others, we gotta make sure it works in our environment. What’s better than a deep test session? Play with the alert rules you configured to generate some alert and see if it gets notified. If everything went smoothly, we should get notifications similar to the one below in our Teams:
Hope that will make the Alert Management process as well as the Notification process easier and usable enough.
Thanks for reading through the entire loooooong post ![]()
Disclaimer
The sample scripts are not supported under any Microsoft standard support program or service. The sample scripts are provided AS IS without warranty of any kind. Microsoft further disclaims all implied warranties including, without limitation, any implied warranties of merchantability or of fitness for a particular purpose. The entire risk arising out of the use or performance of the sample scripts and documentation remains with you. In no event shall Microsoft, its authors, or anyone else involved in the creation, production, or delivery of the scripts be liable for any damages whatsoever (including, without limitation, damages for loss of business profits, business interruption, loss of business information, or other pecuniary loss) arising out of the use of or inability to use the sample scripts or documentation, even if Microsoft has been advised of the possibility of such damages.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.