Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Home
- Microsoft Intune and Configuration Manager
- Configuration Manager Archive
- Using a custom certificate store for Configuration Manager client authentication certificates
Using a custom certificate store for Configuration Manager client authentication certificates
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Published
Oct 16 2018 09:08 PM
2,215
Views
Oct 16 2018
09:08 PM
Oct 16 2018
09:08 PM
First published on TECHNET on Oct 25, 2016
Author: Ray Rosen , Microsoft Premier Field Engineering
Public Key Infrastructure (PKI) is used in varying degrees in different organizations, and since System Center Configuration Manager 2007, it has been leveraged to support Internet Based Client Management. PKI is also an option to identify systems, as the Discovery Data Manager automatically approves clients when a PKI certificate is used for client identity. As long as the site systems that handle client communication trust the client authentication certificate chain, then the client receives service.
When an organization stands up PKI simply to support Configuration Manager, no contention exists within the computer’s certificate personal store. This is the default location where a new certificate is installed for the computer. However, when an organization heavily leverages PKI, the default personal store may contain a number of certificates, and the situation may complicate the usage of certificates for Line of Business (LOB) applications, Configuration Manager, or both.
Configuration manager allows the administrator to specify strings or attributes in the certificate subject or subject alternative name to select a certificate, but when the Configuration Manager client certificate’s presence in the personal store affects a LOB application, the fact that Configuration Manager is ‘OK’ provides little relief to the administrator. To better handle the scenario, the admin may instead specify a custom certificate store for selecting a client authentication certificate, which eliminates any conflict with other applications. Here’s an example of how to leverage this capability.
First we need a certificate template to issue certificates for client authentication. Use the same process as always to duplicate the Workstation Authentication template for this purpose and give the template a meaningful name, but do not enable Autoenrollment.
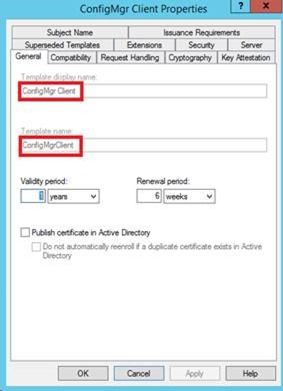
Note that Template name will omit spaces that exist in Template display name . Also set the security on the template for Domain Computers and Domain Controllers to Read and Enroll the certificate. Autoenroll is not required since we will use a script to issue the certificate.

Once the template is created, instruct the Certificate Authority to issue the certificate. When complete, it will appear in the main Certificates Templates screen:

Next, a script needs to run on each client to perform the following:
So why use a script instead of Autoenroll? The goal is to avoid contention in the personal store, and the fastest way to ensure a clean personal store is to move the certificate out of the personal store immediately after it is installed. This option does not exist for Autoenrollment.
A sample script to do this is posted here , however please note that this script will only work on Windows 8 and Windows Server 2012 or later. The script needs to run as local system or administrator on every client, and depending on the environment, this can be accomplished by one of the following:
Whichever method you choose, the script needs to run at least as frequently as the number of days specified before expiration so you can ensure that a new certificate always replaces an expiring one before it expires.
After the script has executed, the site properties can be modified to use the custom store as specified in your script:

On the next machine policy poll after committing the site properties change, the clients will use the new settings and look for a client authentication certificate in the custom store. Once found, it will be used to update the client’s registration with its primary site and become the client’s new crypto identity.
Ray Rosen , Microsoft Premier Field Engineering
Author: Ray Rosen , Microsoft Premier Field Engineering
Public Key Infrastructure (PKI) is used in varying degrees in different organizations, and since System Center Configuration Manager 2007, it has been leveraged to support Internet Based Client Management. PKI is also an option to identify systems, as the Discovery Data Manager automatically approves clients when a PKI certificate is used for client identity. As long as the site systems that handle client communication trust the client authentication certificate chain, then the client receives service.
When an organization stands up PKI simply to support Configuration Manager, no contention exists within the computer’s certificate personal store. This is the default location where a new certificate is installed for the computer. However, when an organization heavily leverages PKI, the default personal store may contain a number of certificates, and the situation may complicate the usage of certificates for Line of Business (LOB) applications, Configuration Manager, or both.
Configuration manager allows the administrator to specify strings or attributes in the certificate subject or subject alternative name to select a certificate, but when the Configuration Manager client certificate’s presence in the personal store affects a LOB application, the fact that Configuration Manager is ‘OK’ provides little relief to the administrator. To better handle the scenario, the admin may instead specify a custom certificate store for selecting a client authentication certificate, which eliminates any conflict with other applications. Here’s an example of how to leverage this capability.
First we need a certificate template to issue certificates for client authentication. Use the same process as always to duplicate the Workstation Authentication template for this purpose and give the template a meaningful name, but do not enable Autoenrollment.

Note that Template name will omit spaces that exist in Template display name . Also set the security on the template for Domain Computers and Domain Controllers to Read and Enroll the certificate. Autoenroll is not required since we will use a script to issue the certificate.

Once the template is created, instruct the Certificate Authority to issue the certificate. When complete, it will appear in the main Certificates Templates screen:

Next, a script needs to run on each client to perform the following:
- Create a custom certificate store if one does not exist.
- Request a new certificate if one does not exist in the custom store.
- Request a new certificate if all existing certificates are about to expire in the custom store.
So why use a script instead of Autoenroll? The goal is to avoid contention in the personal store, and the fastest way to ensure a clean personal store is to move the certificate out of the personal store immediately after it is installed. This option does not exist for Autoenrollment.
A sample script to do this is posted here , however please note that this script will only work on Windows 8 and Windows Server 2012 or later. The script needs to run as local system or administrator on every client, and depending on the environment, this can be accomplished by one of the following:
- Using a startup script via GPO
- Setting up a Task Scheduler task to call it from a network share via GPO
- If already a Configuration Manger client and a HTTP MP will persist, a Compliance Settings script, package deployment, etc. could do the job.
Whichever method you choose, the script needs to run at least as frequently as the number of days specified before expiration so you can ensure that a new certificate always replaces an expiring one before it expires.
After the script has executed, the site properties can be modified to use the custom store as specified in your script:

On the next machine policy poll after committing the site properties change, the clients will use the new settings and look for a client authentication certificate in the custom store. Once found, it will be used to update the client’s registration with its primary site and become the client’s new crypto identity.
Ray Rosen , Microsoft Premier Field Engineering
0
Likes