- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 10 2021 10:33 AM
We have a script that detects successful logins to our system by using the Search-UnifiedAuditLog. If they’re from outside of our country, we immediately block these accounts and boot them off our tenant. (This is our homemade GeoFencing I guess.) Today we received an alert of the following (generated by our script).
Critical and/or Blocked IPs:
IP | Location | Date Signed-In | User ID (One of them) | Action |
102.x.x.x | Lagos, Nigeria | 2021-12-10 12:48:56 | BLOCKED: Critical |
That @microsoftsupport.com address (i've blanked out the full email address, it's not all x's ) is a legit Microsoft domain. But obviously the location is very scary to us. We have no record of that account as one in our Azure AD. Not as a guest, nothing. So I have no idea how or why this person is authenticating to our domain.
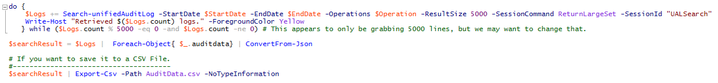
Our script grabs audit logs via the following command:
Basically, that generated the following entry in the exported data today. I've removed a lot of data, indicated by xxx's
UserKey | 00000000-0000-0000-0000-000000000000 |
UserType | 0 |
Version | 1 |
Workload | AzureActiveDirectory |
ClientIP | 102.x.x.x |
ObjectId |
|
UserId | |
AzureActiveDirectoryEventType | 1 |
ExtendedProperties | System.Object[] |
ModifiedProperties | System.Object[] |
Actor | System.Object[] |
ActorContextId | xxxxxxxxx |
ActorIpAddress | 102.x.x.x |
InterSystemsId | xxxxxxxx |
IntraSystemId | xxxxxxx |
SupportTicketId | |
Target | System.Object[] |
TargetContextId | xxxxxxxx |
ApplicationId | xxxxxxx |
DeviceProperties | System.Object[] |
ErrorNumber | 0 |
I will say we saw something kind of similar a few months back. Whereby one of our users shared a file with an external user via email. When the external user clicked on the OneDrive link they received from us, they authenticated with their work-account email/password which must have been from there o365 domain and different than their actual email account. For some reason, that too recorded in our system as if they auth’d to our Azure, even though we don’t have them setup as a guest or anything. The difference being, in that case, this was somewhat intentional, in the one we are reporting today, this was completely out of nowhere!
Any help is appreciated.