- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 06 2021 07:00 PM
Hello all, my Azure subscription has security groups that allow unrestricted inbound or outbound access on port and protocol combinations. Allowing unrestricted inbound/ingress or outbound/egress access can increase opportunities for malicious activity such as hacking, loss of data, and brute-force attacks or Denial of Service (DoS) attacks. How can I configure the allowed ports by assigning a policy to my subscription. Is there a built-in policy for that?
- Labels:
-
Azure Policy
-
network security groups
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 07 2021 12:54 AM - edited Jan 07 2021 02:42 AM
@nabi04 Typically I would use specific rules for specific resources in NSG rules, rather than blanket policy.
For example your web server for "Application A" might want to accept incoming traffic from your AppGateway on port 443, and be able to talk to the database server for "Application A" on 1433. In contrast, the web server for "Application B" would have different rules because you don't want it to talk to the database server for "Application A".
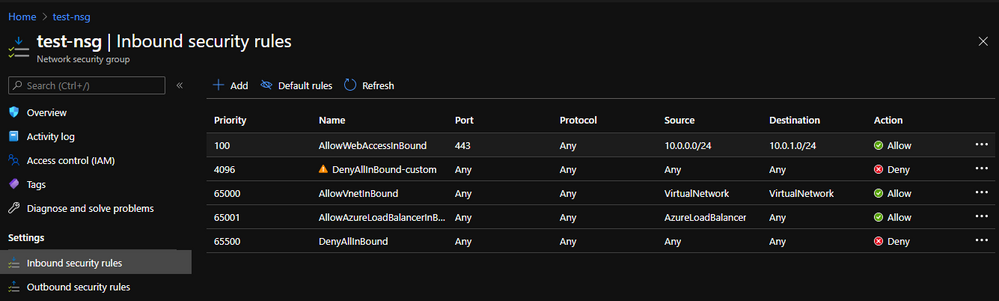
The NSGs do come with default "allow all" rules, and these can be turned off by putting a "Deny All" at the bottom of your custom list of rules, on a low priority- 4,096. For example:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 07 2021 01:13 AM
Hi you need to define a flow matrix to have a clear view which service talk to which service through wich protocol . Do we need to open port 80 while the service is a dns ? (Example). You also need to document all your NSG so people can see clearly what is the goal and don't create a rule a top of that . For group of servers create application security group to facilitate nsg rules management .
You are exposed some kind of attacks only if you expose endpoints to the public . Sometimes you don't have choice but sometimes you don't need services publicly exposed and in this case make it private .
One exercise you can do is also evaluate the risks according to the type of workloads and give a status of the remediation using Azure Defender .In fact builtin many security policies are handled by Azure Defender formerly Azure Security Center .