- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 21 2022 07:56 AM - edited Jun 21 2022 07:59 AM
I have both my Azure File Share and My Azure File Sync going through private endpoints, Azure File Share works fine and I'm able to access the shares directly on-prem with no issues. I also have Azure File Sync setup on one of my file servers and I want it to sync to one of the Azure File Shares I created for redundancy. I'm able to register the server on Azure File Sync fine and create a sync group, but when I go to create a cloud endpoint I get the following error:
Cloud endpoint '********'
Code: MgmtForbidden
Details: Failed to provision a replica group.
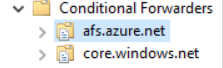
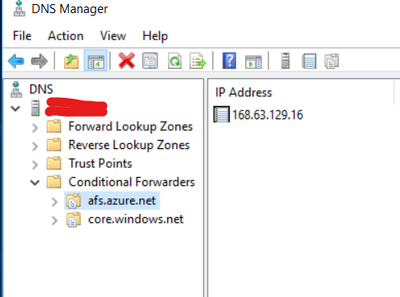
I have a site-to-site-vpn setup between my on-prem and azure ad that's up and running fine. I also setup conditional forwarding for core.windows.net & afs.azure.net to point to the IP address of a DNS server that I created in Azure Cloud. My DNS server then uses a conditional forward to point core.windows.net & afs.azure.net to Azure's DNS address 168.63.129.16.
On Prem(Points to DNS Server IP:
On Azure DNS Server (Points to 168.63.129.16):
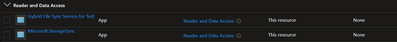
I even double checked that the file sync service has access to the file share:
I can resolve the hostnames of both private endpoints but I can only ping the IP address of the File Share Private endpoint is there something I'm missing?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 21 2022 08:22 AM
I was able to figure this out for anyone else who has this issue, as Microsoft does not provide clear documentation anywhere regarding this use case that I know of:
You need to go to the storage account you want to access and change the Network settings to "Enabled from selected virtual networks and IP addresses"
Then you have to check off in Exceptions:
Hope this helps anyone else!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 10 2022 02:07 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 07 2023 10:51 AM
@ike_bai1022 , you truly helped me move forward, with something that I have been struggling for quite some time!! Much appreciate you sharing the solution here! Your solution did help me, to successfully create the cloud end point for the first time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 09 2023 04:56 PM
Yes, it need to allow before you can access, not sure it's a security concern that not enable by default