- Home
- Azure
- Azure Virtual Desktop
- PUBLIC PREVIEW: Announcing public preview of Azure AD joined VMs
PUBLIC PREVIEW: Announcing public preview of Azure AD joined VMs
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 14 2021 11:26 AM
We are excited to announce the public preview of Azure AD joined VMs support for Azure Virtual Desktop. This feature allows customers to easily deploy Azure AD joined session hosts from the Azure portal and access them from all clients. VMs can also be automatically enrolled in Intune for ease of management. Support for storing FSLogix profiles on Azure files will be available in a future update.
Getting started:
The documentation to deploy Azure AD joined session hosts will guide you through the key steps needed to enable this functionality.
- Labels:
-
AVDUpdate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 28 2021 03:39 PM
I managed to create two different Host Pools, each with its VM and application publishing, working 100%.
but now i'm trying to create again and the VMs are only with the status Unavailable, with this error it is not possible to work with access via RDP publishing.
I've already performed both procedures
https://docs.microsoft.com/en-us/azure/virtual-desktop/troubleshoot-agent#error-vms-are-stuck-in-una...
but without success, any other procedure to perform and try to fix this error?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 30 2021 10:13 AM
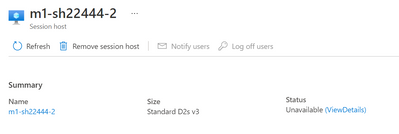
@mcavalcantitecmicrosof Was there any error during the deployment itself?
When going to the Host pool / Session host section in the Azure portal, if you select a host pool that is marked unavailable and clicked the ViewDetails option:
What do you see as failed (HealthCheckFailed) in the document that opens up. It should look like this:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 10 2021 12:17 AM
Excluding the Azure Windows VM sign-in does work for me however it also blocks MFA on Jamf Connect Login (MDM) which is a bigger concern for the organisation.
Any advice pls?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 10 2021 05:57 AM
Hey Nikonline - I encountered such issues and this is what I did to resolve.
- Navigate to the Host Pool
- Click "Access Control (IAM)"
- Click "Role Assignments"
- Click "Add"
- Find "Virtual Machine Administrator Login" or "Virtual Machine User Login"
- In my case I selected Administrator
- Add Security Group or user
For my MFA CA Policy:
- Cloud Apps:
- Exclude "Azure Windows VM Sign-in"
- Exclude "Windows Virtual Desktop"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 10 2021 06:47 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 08 2022 08:28 PM
Would just like to confirm that you can access/login to AAD-Joined session hosts from an Azure AD Registered Device using your AAD credentials?? The docs state it below (third point) but when I have tested this it doesn't work; it does however work fine when the local PC is AAD Joined.
Does it need to be a certain edition of Windows 10?
Connect using the Windows Desktop client
The default configuration supports connections from Windows 10 using the Windows Desktop client. You can use your credentials, smart card, Windows Hello for Business certificate trust or Windows Hello for Business key trust with certificates to sign in to the session host. However, to access the session host, your local PC must meet one of the following conditions:
- The local PC is Azure AD-joined to the same Azure AD tenant as the session host
- The local PC is hybrid Azure AD-joined to the same Azure AD tenant as the session host
- The local PC is running Windows 10, version 2004 and later, and is Azure AD registered to the same Azure AD tenant as the session host
To enable access from Windows devices not joined to Azure AD, add targetisaadjoined:i:1 as a custom RDP property to the host pool. These connections are restricted to entering user name and password credentials when signing in to the session host.
https://docs.microsoft.com/en-us/azure/virtual-desktop/deploy-azure-ad-joined-vm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 09 2022 12:03 AM
@ahart3 Make sure you have assigned these AAD users in the RBAC roles(e.g. Virtual Machine Contributor or Virtual Machine User Login) of the VMs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 09 2022 01:29 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 09 2022 10:32 PM - edited Mar 09 2022 10:34 PM
@ahart3 Cool! nice to know. You can then corporate these AAD joined VMs to Intune for added security its like a GPO but a flat structure. Also Virtual Machine Administrator Login role will assign a local admin privileges for that user on the session host, as for Virtual Machine User Login, it will only assign as a non admin role inside the session host.
- « Previous
- Next »