- Home
- Azure
- Azure Virtual Desktop
- Re: PUBLIC PREVIEW: Announcing public preview of Azure AD joined VMs
PUBLIC PREVIEW: Announcing public preview of Azure AD joined VMs
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 14 2021 11:26 AM
We are excited to announce the public preview of Azure AD joined VMs support for Azure Virtual Desktop. This feature allows customers to easily deploy Azure AD joined session hosts from the Azure portal and access them from all clients. VMs can also be automatically enrolled in Intune for ease of management. Support for storing FSLogix profiles on Azure files will be available in a future update.
Getting started:
The documentation to deploy Azure AD joined session hosts will guide you through the key steps needed to enable this functionality.
- Labels:
-
AVDUpdate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 14 2021 11:55 AM
@David Belanger Wohoo!
How does this fit with the recent announcement about Cloud PC?
https://www.youtube.com/watch?v=V14Ia2uwrtk
Trying to figure out if we are better off with AVD "Personal" machines. vs a CloudPC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 14 2021 12:04 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 14 2021 03:45 PM
@David Belanger
Can someone please explain this statement from the documentation?
"Azure Virtual Desktop doesn't currently support single sign-on for Azure AD-joined VMs."
The whole point of setting up Azure AD Joined VM for me is to achieve single sign on end-to-end including my apps like Office, Teams etc.
FYI - SUPER DUPER Excited to get rid of domain controllers now ! This is great progress. Loving it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 14 2021 04:03 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 15 2021 06:28 AM
Solution- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 15 2021 06:49 AM
That's pretty cool - even for cloud-only companies. I used the evening to build it into my community tool =)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 15 2021 07:00 AM
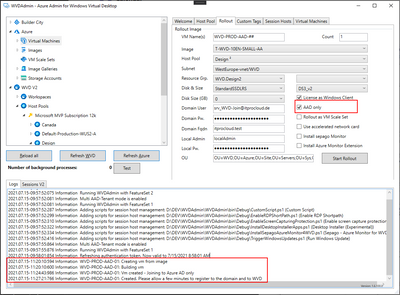
@David Belanger Hi, I created a new host pool with AAD, it is a validation hostpool. I tried to access the AVD but getting error a "login attempt failed" error. I am trying with my UPN to login to the Azure AD VM. I have added myself as "Virtual machine user login" RBAC role but still no luck. Anyone experiencing the same issue?.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 15 2021 07:58 AM
@amal_azurewvd I have the same issue. I followed all the steps at this location and still got the error.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 15 2021 08:00 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 15 2021 08:51 AM
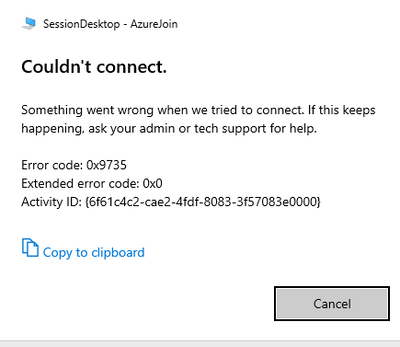
@amal_azurewvd I get this error in the web client: We couldn't connect to the remote PC because of a security error. If this keeps happening, ask your admin or tech support for help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 15 2021 11:16 PM
I think the security error may be related to MFA. I was able to get around it in the desktop client by using a PIN to log in as advised in this link:
I can't get in with the web client though, and have entered targetisaadjoined:i:1 in the RDP Properties, so not sure what the problem is.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 16 2021 04:32 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 16 2021 01:48 PM
I also have targetisaadjoined:i:1 in the RDP Properties...
Anyone encountering this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 16 2021 02:02 PM
Microsoft, can this be fixed?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 18 2021 05:32 AM
@Chris_Gilles_1337 You just need to exclude „Azure Windows VM Sign-in“ from the CA policy requiring MFA beside the already mentioned RDP settings. At least this worked for me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 18 2021 05:38 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 19 2021 02:30 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 19 2021 02:45 AM
@Xandven_ Your source is at least outdated. Latest technical information about the public preview can be found here: https://docs.microsoft.com/de-de/azure/virtual-desktop/deploy-azure-ad-joined-vm
I have both personal and pooled VMs in my lab setup AAD joined and Intune managed. Compliance policies are applied to both types correctly, so that you can eval them in CA policies accordingly.
So, my answer is not an official Microsoft one, but from all these observations I would say: Yes, host pools can be Intune managed in this public preview.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 19 2021 07:50 AM
hi guys
im experiencing an error when trying to connect to my AADJ VM using Remote Desktop app.
Prereqs are all met :
- device from which i try the connection is aadjoined to the same tenant.
- remote desktop app user is added via IAM with AVD User Login role
- targetisaadjoined:i:1 added to rdp advanced properties
- validation env checked
what else can be missing ?
i can only access my VM from the web client , there is no error there and it works from every device.
Device State |
+----------------------------------------------------------------------+
AzureAdJoined : YES
EnterpriseJoined : NO
DomainJoined : NO
Device Name : VM-AzureAD-0
+----------------------------------------------------------------------+
| Device Details |
+----------------------------------------------------------------------+
DeviceId : 2b4f6a7b-02ab-4cb5-a220-1fdde507e7e4
Thumbprint : 4C5F4A2D4D8D55093DDE48F7453621FE8382F2B9
DeviceCertificateValidity : [ 2021-07-19 11:01:49.000 UTC -- 2031-07-19 11:31:49.000 UTC ]
KeyContainerId : 21313e88-443a-4391-b4ca-dcdda5e9ee38
KeyProvider : Microsoft Software Key Storage Provider
TpmProtected : NO
DeviceAuthStatus : SUCCESS
+----------------------------------------------------------------------+
| Tenant Details |
+----------------------------------------------------------------------+
TenantName : xxxxxx
TenantId : xxxxxx
Idp : login.windows.net
AuthCodeUrl : https://login.microsoftonline.com/xxx
AccessTokenUrl : https://login.microsoftonline.com/xxxx/oauth2/token
MdmUrl : https://enrollment.manage.microsoft.com/enrollmentserver/discovery.svc
MdmTouUrl : https://portal.manage.microsoft.com/TermsofUse.aspx
MdmComplianceUrl : https://portal.manage.microsoft.com/?portalAction=Compliance
SettingsUrl :
JoinSrvVersion : 2.0
JoinSrvUrl : https://enterpriseregistration.windows.net/EnrollmentServer/device/
JoinSrvId : urn:ms-drs:enterpriseregistration.windows.net
KeySrvVersion : 1.0
KeySrvUrl : https://enterpriseregistration.windows.net/EnrollmentServer/key/
KeySrvId : urn:ms-drs:enterpriseregistration.windows.net
WebAuthNSrvVersion : 1.0
WebAuthNSrvUrl : https://enterpriseregistration.windows.net/webauthn/xxx/
WebAuthNSrvId : urn:ms-drs:enterpriseregistration.windows.net
DeviceManagementSrvVer : 1.0
DeviceManagementSrvUrl : https://enterpriseregistration.windows.net/manage/xxx/
DeviceManagementSrvId : urn:ms-drs:enterpriseregistration.windows.net
+----------------------------------------------------------------------+
| User State |
+----------------------------------------------------------------------+
NgcSet : NO
WorkplaceJoined : NO
WamDefaultSet : YES
WamDefaultAuthority : organizations
WamDefaultId : https://login.microsoft.com
WamDefaultGUID : {xxxx} (AzureAd)
+----------------------------------------------------------------------+
| SSO State |
+----------------------------------------------------------------------+
AzureAdPrt : YES
AzureAdPrtUpdateTime : 2021-07-19 14:45:18.000 UTC
AzureAdPrtExpiryTime : 2021-08-02 14:45:17.000 UTC
AzureAdPrtAuthority : https://login.microsoftonline.com/xxx
EnterprisePrt : NO
EnterprisePrtAuthority :
+----------------------------------------------------------------------+
| Diagnostic Data |
+----------------------------------------------------------------------+
AadRecoveryEnabled : NO
Executing Account Name : xxxxx
KeySignTest : PASSED
+----------------------------------------------------------------------+
| IE Proxy Config for Current User |
+----------------------------------------------------------------------+
Auto Detect Settings : YES
Auto-Configuration URL :
Proxy Server List :
Proxy Bypass List :
+----------------------------------------------------------------------+
| WinHttp Default Proxy Config |
+----------------------------------------------------------------------+
Access Type : DIRECT
+----------------------------------------------------------------------+
| Ngc Prerequisite Check |
+----------------------------------------------------------------------+
IsDeviceJoined : YES
IsUserAzureAD : YES
PolicyEnabled : NO
PostLogonEnabled : YES
DeviceEligible : NO
SessionIsNotRemote : NO
CertEnrollment : none
PreReqResult : WillNotProvision
For more information, please visit https://www.microsoft.com/aadjerrors
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 15 2021 06:28 AM
Solution