- Home
- Azure
- Azure Virtual Desktop
- Re: Error when connecting to MVD - 0x3000047
Error when connecting to MVD - 0x3000047
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 20 2020 09:53 AM
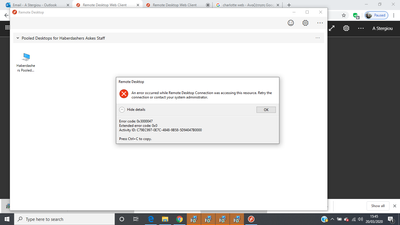
I have recently deployed WVD thanks to the current global crisis. It is working well for most of our users, apart from one. When she tries to connect to WVD via the web client, she gets this:
When connecting via the Windows client, she gets this:
As far as I know, she is the only member of staff who gets this. She's using Windows 10 Home on a laptop, has tried multiple browsers and is using a DSL ISP (Sky in this instance).
I've tried running "Get-RdsDiagnosticActivities" but it comes back with "There were no activities found"
Any ideas?
Thanks,
Ian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 23 2020 11:43 AM
Hi, i'm literally facing the same issue:
Error code: 0x3000047
Extended error code: 0x0
Activity ID: AB903267-6E4A-42F5-8087-8F0CB8C10000
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 23 2020 08:14 PM
Thanks for the feedback. Any thoughts on what could be different for those user's devices?
For reference, I filed the tracking item for investigation:
Item 25683128 : Reports of error 0x3000047 when connecting to WVD
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 24 2020 05:17 AM
same issue both via web and client
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 24 2020 06:38 AM
Check that both catalogs Azure AD and your AD DS contain this problem user and this account was synced between these catalogs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 24 2020 10:09 AM
Solution@Sergey Osherov I think you are on the right track. Here's what we see internally:
Client gets an Error during Orchestration.
Orchestration failed. Code=0x80075a1e, symbolicCode: E_PROXY_ORCHESTRATION_UNKNOWN_ERROR, message: Failed to add user = ≤USERNAME REMOVED≥ to group = Remote Desktop Users. Reason: Win32.ERROR_NO_SUCH_MEMBER, target: (null):4
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 25 2020 06:42 AM - edited Mar 25 2020 06:56 AM
@David Belanger OK, so that's interesting.
In AD, she's k.user@domain.com while in AAD she's a.user@domain.com. Both accounts are linked but have different UPNs in either service. I take it that's the problem then?
/edit Actually, no, somehow she's managed to end up with two accounts in O365, one synced from AD and a cloud account. Of course, she's trying to use the Cloud account to get in. What fun.
Thank you for your help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 25 2020 09:25 AM
The UPNs must be the same in on-prem DC(-s) and Azure AD.
What we've just done was to:
- Open “Active Directory Domains and Trusts”
- On the left hand side of the new window, right click on “Active Directory Domains and Trusts”, and select “Properties”
- Type in the domain suffix of the user allowed to use WVD, in to the “Alternative UPN suffixes” box, and then click “Add”.
- Modify the user logon name property of the respective user from (e.g:) username@contoso.local to username@domain.tld (as the user has it in O365 / AAD tenant)
- Try again.
TLDR;
Make sure the O365 UPN is the same with the User Logon Name in local Active Directory.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 11 2020 06:25 PM
hello norphus
i also have the same problem now
if you solve your problem can you tell us the solution
regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 17 2020 05:43 AM
It happens to us as well. I add the user through Graph API. The user can't access it for up to 40 minutes. Then the user is able to log in to the WVD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 07 2020 02:22 PM
Thank you.
This solved my problem with a session pool where the VMs were not joined to the Azure AD DS domain, but were in an internal domain, with a separate isolated domain controller on a VM within the same subscription.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 22 2020 04:23 AM
- Click Start, click Administrative Tools, and then click Computer Management.
- In the console tree, click the Local Users and Groups node.
- In the details pane, double-click the Groups folder.
- Double-click Remote Desktop Users, and then click Add.
- In the Select Users dialog box, click Locations to specify the search location.
- Click Object Types to specify the types of objects that you want to search for.
- In the Enter the object names to select (examples) box, type the name you want to add.
- Click Check Names.
- When the name is located, click OK.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 26 2020 06:38 AM - edited May 26 2020 07:23 AM
It happens to us as well:
the user has the same UPN in AD and AAD
the user is member of local Remote Desktop User on the WVD Computer
Any guide to diagnose and fix the problem?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 28 2020 03:08 AM
same , trying to connect to newly deployed host pool based on 2004 win 10 (
connnection to old host pool (same tenant, same domain same upn ) goes well
(( not sure how to troubleshhot this
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 28 2020 08:08 AM
Same issue, but at the beginning everythig was OK with the first Hoospool, and now I can´t connect. I created two more pool and with the same result
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 28 2020 11:56 AM
I had a similar issue today in my 2004 lab environeemnt, but i only had to reboot my DC and RDSH server.
I would suggest you to check UPNs in your DC and check the rights.
(Rights are per apps in 2019 deployment types, so if you created a new pool you need to add the same users to the new pool).
Once i did re-subscribed the connection worked.
Hope it help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 01 2020 10:44 AM - edited Jun 01 2020 10:47 AM
My setup worked fine with the default gallery image (Win10 multi-session with Office ProPlus). I then created a custom image and ran all the time into 0x3000047. Tried reboots and checked my UPN suffixes. All looked good, error persisted.
My custom image was with the brand new Windows 10 2004 with Office 365 ProPlus image. Not sure if it had any thing to do with it. Image was sysprepped, captured and published to the shared image gallery.
My observation was that the Session Host(s) created kept their original computer names. The machine was also joined to the domain with the original name, not rdsh-0 what I expected. I manually renamed the session host and rejoined, this did not help.
Finally decided to recreate my custom image based on Windows 10 1908 with Office. This time it worked fine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 03 2020 01:27 PM
I had the same error from one of my user and found out that Virtual PC was not connected or dropped out of our domain. We ended up reconfiguring VDI for that user. @Norphus
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 05 2020 03:23 PM - edited Jun 05 2020 03:24 PM
same issue here - 0x3000047 for W10 2004 - based custom image. Will try 1909 base next week.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 24 2020 10:09 AM
Solution@Sergey Osherov I think you are on the right track. Here's what we see internally:
Client gets an Error during Orchestration.
Orchestration failed. Code=0x80075a1e, symbolicCode: E_PROXY_ORCHESTRATION_UNKNOWN_ERROR, message: Failed to add user = ≤USERNAME REMOVED≥ to group = Remote Desktop Users. Reason: Win32.ERROR_NO_SUCH_MEMBER, target: (null):4