- Home
- Azure
- Azure Virtual Desktop
- Error "the connection was denied because the user account is not authorised"
Error "the connection was denied because the user account is not authorised"
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 23 2022 03:52 PM
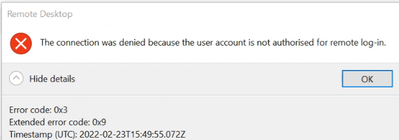
We have a handful of users on our AVD deployment who are unable to connect to a session. They are able to sign into RD Client, see the applications in their feed and refresh the feed. However when they try to connect to a desktop or remote app, it fails with the error message "the connection was denied because the user account is not authorised for remote log-in" and with error code 0x3
We have checked the Azure group entries, their M365 licensing and cannot find a cause.
Is anyone able to diagnose the issue or recommend a fix?
Thanks
David
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 24 2022 12:22 PM
Hi @David Overton,
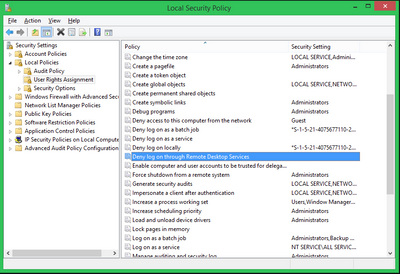
May be you have some GPO setup to deny certain groups/individuals from using RDP, and it got applied to the AVD session hosts?
Something like this:
hope this will be helpful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 25 2022 04:30 AM
@michael_moshkovich Unfortunately that is not the issue. We do have a deny group, but it is empty in AD and Azure AD. I double checked, the user's account to make sure they were not part of that group, so not applicable both ways.
I also tried adding the user to the local VM's Remote Desktop Users group and suddenly they are able to sign in without issue. I have other users in the same domain who are able to sign in without being added to the Remote Desktop Users local group.
I looked at the logs and in WVDErrors and I see these 3 lines consistently for a user who fails to sign in.
TimeGenerated [UTC] | ActivityType | Source | Code | CodeSymbolic | Message | ServiceError | Operation |
| 24/02/2022, 13:20:33.197 | Connection | Client | 9,223 | SSL_ERR_ACCESS_DENIED | SSL_ERR_ACCESS_DENIED | FALSE | ClientRDPConnect |
| 24/02/2022, 13:20:35.118 | Connection | RDGateway | -2,147,467,259 | ConnectionFailedReverseUngracefulClose | The Session Host did not respond to the service attempt to gracefully terminate the connection. | FALSE | GatewayConnectionActive |
| 24/02/2022, 13:21:25.772 | Connection | RDStack | 12 | NotAuthorizedForLogon | This user isn't authorized so sign in to the session host. | FALSE | Authorization |
Given that the VMs are not AzureAD domain joined, I have seen that the SSL error could be associated with users who might be AzureAD joined, so I took the precaution of enabling the PKU2U policy setting, but this also made no difference.
Any pointers appreciated.
David
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 12 2022 06:00 AM
@David Overton Were you able to resolve this issue. I have something very similar. A windows 11 machine cannot connect, but we use the credentials on other machines, and it works fine to log in. This one machine just has the problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 14 2022 04:40 PM
The workaround was a group policy that added the users who could not connect natively to the AVD. The group policy added the users to the Remote Desktop Users group on each of the AVD hosts.