- Home
- Azure Data
- Azure SQL Blog
- Azure SQL Database Connectivity and Network Security improvements
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Azure SQL Database Connectivity and Network Security improvements
Reviewers:- Andreas Wolter, Rajesh Setlem
We are proud to announce several improvements to Azure SQL Database and Azure Synapse Analytics (formerly Azure SQL DW) in the areas of Connectivity and Network Security.
Customers can now choose to connect to SQL Database and Azure Synapse via the private endpoint and deny all public access via the firewall rules.
GA of Private Link for Azure SQL Database and Azure Synapse Analytics
Now in general availability, Private Link enables users to have private connectivity from a Microsoft Azure Virtual Network to Azure SQL Database and Azure Synapse.
This feature creates a private endpoint which maps a private IP Address from the Virtual Network to your Azure SQL Database and Azure Synapse.
From security perspective, Private Link provides you with data exfiltration protection on the login path. Additionally, it does not require adding of any IP addresses to the firewall or changing the connection string of your application.
Private Link is built on best of class Software Defined Networking (SDN) functionality from the Azure Networking team. Clients can connect to the Private endpoint from within the same Virtual Network, peered Virtual Networking the same region, or via VNet-to-VNet connection across regions. Additionally, clients can connect from on-premises using ExpressRoute, private peering, or VPN tunneling. More information can be found here
SQL Database Query Editor supports Private Link
Previously, for using Query Editor ( in Azure Portal) customers would add their Client Ip address in the Azure SQL Database firewall. With this new functionality, customers can run Query Editor and connect via private endpoints without having any dependency on IP based firewall. More information can be found here
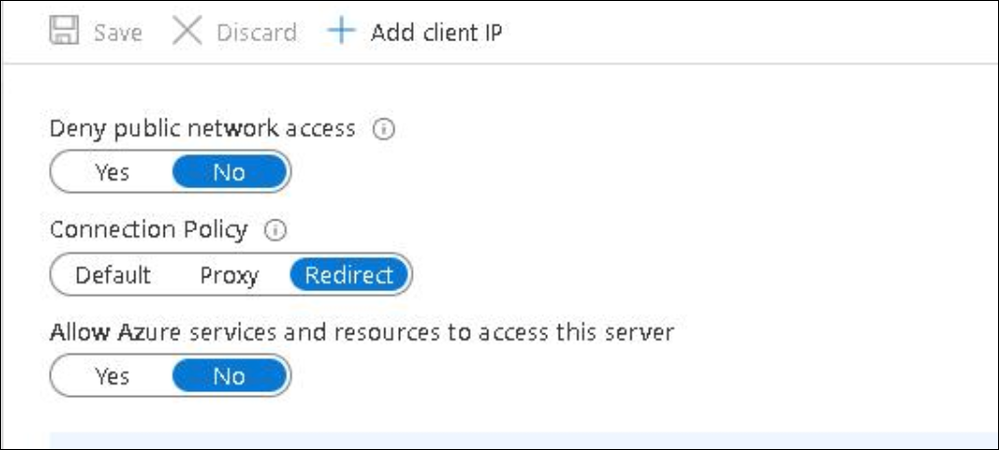
Server level Connectivity Settings
We have made multiple improvements that allow you to control connectivity settings for Azure SQL Database and Azure Synapse . These setting are at the logical server level i.e. they apply to all SQL Databases and Azure Synapse instances created on a server. Note that once these settings are applied they take effect immediately and may result in connection loss for your clients if they do not meet the requirements for each setting. At present these settings are only available in US West 2, US East, US South Central with other regions soon to follow. More information can be found here
Ability to set Connection Policy
Connection policy determines the requirements for clients to establish connections to Azure SQL Database or Azure Synapse instances.
Deny Public network access
While Private Link allows access via private endpoint only, we recognize that there are cases where customers may need a mix of private and public connectivity To support these scenarios, we have provided the ability to deny Public Network access to SQL Database.
When this setting is set to Yes only connections via private endpoints are allowed. When this setting is set to No clients can connect using private or public endpoint.
GA of Azure SQL Auditing to Azure Storage account behind VNet and Firewall
Customers can now choose a Storage account destination for their Azure SQL Auditing that is behind VNet and Firewall to write their database events. This improvement will provide more security for auditing and support a safer writing pipeline for sensitive databases. To learn more, visit Write audit to a storage account behind VNet and firewall.
In summary, we hope these improvements shall provide customers with more options to secure connections made to SQL Database and Azure Synapse instances and to meet the compliance requirements within their organizations where they need to connect to Azure SQL DB and Azure Synapse over private endpoint. We look forward to your feedback on these features.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.