- Home
- Security, Compliance, and Identity
- Microsoft Sentinel Blog
- What’s new: Microsoft Teams connector in Public Preview
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
This installment is part of a broader series to keep you up to date with the latest features in Microsoft Sentinel. These installments will be bite-sized to enable you to easily digest the new content.
Great news! You can now use an in-built connector to connect Microsoft Teams logs to your Microsoft Sentinel workspace. You may have already been doing this with a custom connector using the Office 365 API but now this functionality is available via an in-built connector in Sentinel.
With collaboration software becoming even more critical with the shift in work patterns that has taken place this year, monitoring these systems has become a priority for many organizations. The information that can be ingested using the Microsoft Teams connector includes details of actions such as file downloads, access requests sent, changes to group events, mailbox operations, Teams events (such as chat, team, member, and channel events), as well as the details of the user who performed the actions.
Connecting Microsoft Teams logs to Azure Sentinel enables you to view and analyze this data in your workbooks, query it to create custom alerts, and incorporate it to improve your investigation process, giving you more insight into your Office 365 security.
How to enable Microsoft Teams log ingestion in Microsoft Sentinel
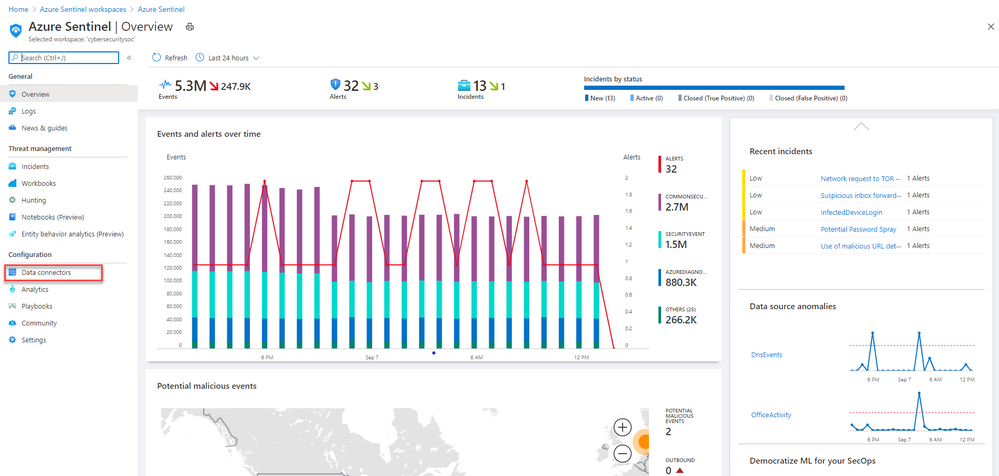
- From the Azure Sentinel navigation menu, select Data connectors.
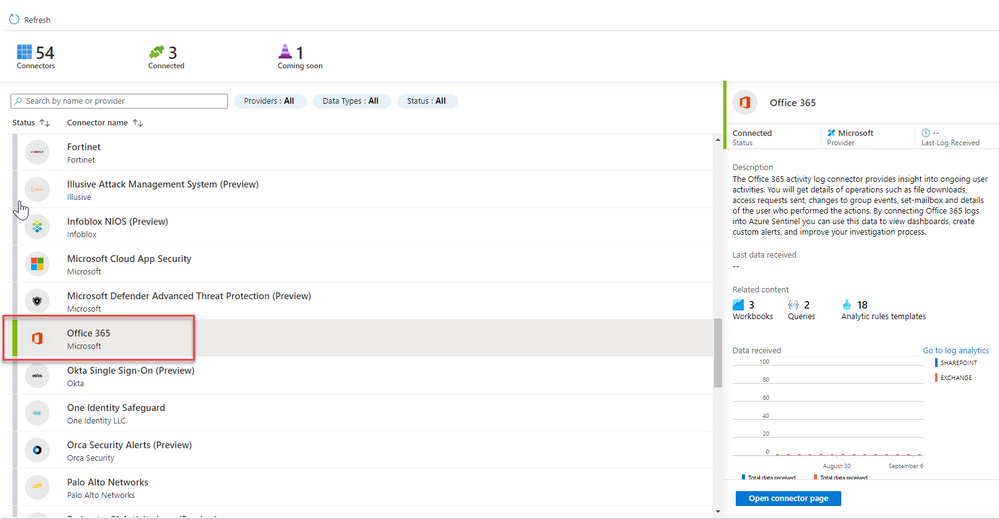
- Select Office 365 from the data connectors gallery, and then select Open Connector Page on the preview pane.
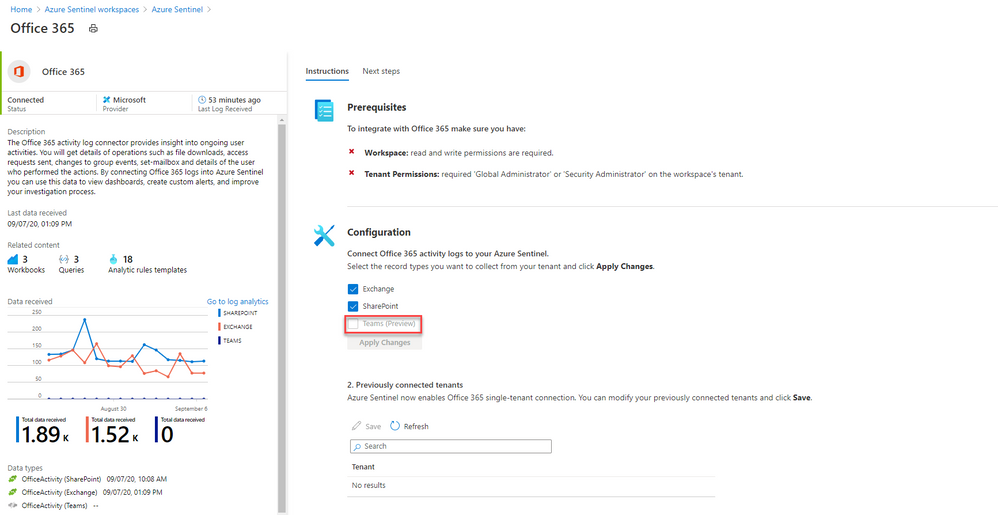
- On the Office 365 connector page, under Configuration select the tick box with Teams (Preview) and click Apply Changes.
And that’s it! You will now have Teams logs from your O365 tenant connected to your Sentinel workspace.
Get Started Today!
Try out the new connector and let us know your feedback using any of the channels listed in the Resources.
You can also contribute new connectors, workbooks, analytics and more in Azure Sentinel. Get started now by joining the Microsoft Sentinel Threat Hunters GitHub community and follow the guidance.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.