- Home
- Security, Compliance, and Identity
- Microsoft Sentinel Blog
- What's New: Azure Sentinel Logic Apps Connector improvements and new capabilities
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Azure Sentinel Logic Apps connector is the bridge between Sentinel and Playbooks, serving as the basis of incident automation scenarios. As we prepare for new Incident Trigger capabilities (coming soon), we have made some improvements to bring the most updated experience to playbooks users.
Note: existing playbooks should not be effected. For new playbooks, we recommend using the new actions.
Highlights:
- Operate on most up-to-date Incidents API
- New dynamic fields are now available
- Less work to accomplish incident changes
- Assign Owner ability in playbooks
- Format rich comments in a playbook
What's new?
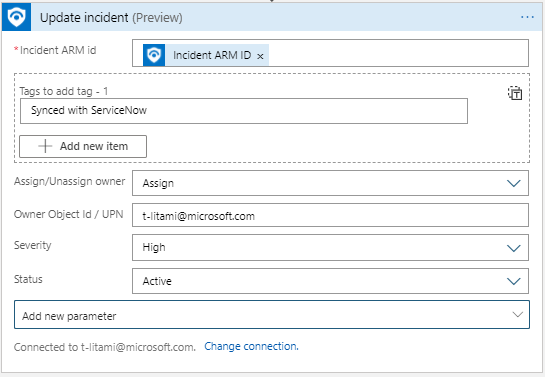
Update Incident: One action for all Incident properties configuration
Now it is simpler to update multiple properties at once for an incident. Identify the Incident you want to operate on and set new values for any field you want.
Update Incident replaces the actions: Change Incident Severity, Change Incident Status, Change Incident Title, Change Incident Description, Add/Remove Labels. They will still work in old playbooks, but eventually will be removed from the actions gallery for future use.
Assign Owner in playbooks
As part of new Update Incident, it is now possible to assign an owner to an incident in a playbook. For example, based on incident creation time and SecOps staffing information (for example, from a you can assign the incident to the right shift owners:
- Set Assign/Unassign owner to Assign
- Set Owner with the Object ID or User Principal Name.
Post Rich Comments with HTML editor
Recently, Azure Sentinel added support for HTML and Markdown for Incident Comments. Now, we added an HTML editor to the Add comment to Incident so you can format your comments.
One identifier for working on Azure Sentinel Incidents
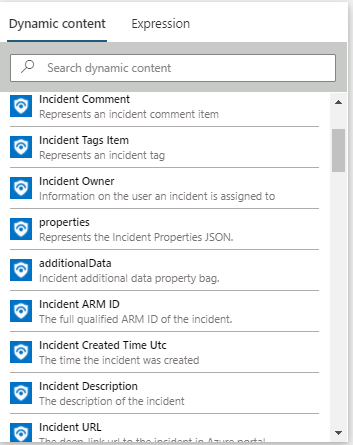
Previously, you had to supply 4 fields in order to identify the incident to update. New Update Incident and Add Comment to Incident require only one field (instead of 4) to identify the incident that meant to be changed: Incident ARM ID.
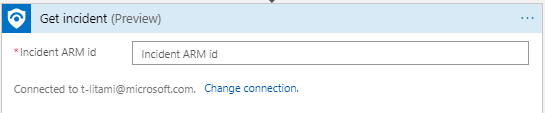
If your playbooks start with Azure Sentinel Alert trigger (When an Azure Sentinel Alert is Triggered), use Alert - Get Incident to retrieve this value.
Get Incident: Now with most updated Sentinel API
Alert - Get Incident allows playbooks that start with Azure Sentinel Alert Trigger (When an alert is triggered) to reach the incident that holds the alert.
Now, new fields are available and are aligned to the Incident API.
For example, Incident URL can be included in an Email to the SOC shared mailbox or as part of a new ticket in Service Now, for easy access to the incident in the Azure Sentinel portal.
This action's inputs have not changed, but the response became richer:
In addition, we supplied another action called Get Incident which allows you to identify incidents using the Incident ARM ID, so you can use any other Logic Apps trigger and still get Incident details. It returns the same Incident Schema. For example, if you work with another ticketing system which supports triggering Logic Apps, you can send the ARM ID as part of the request.
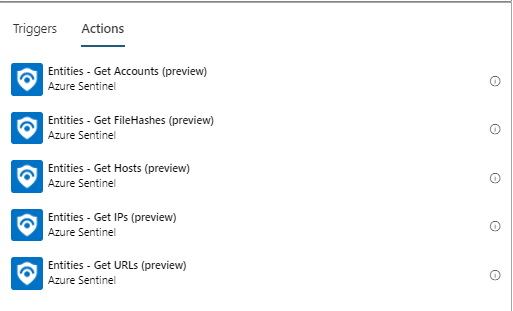
Get Entities: names change
As we prepare for our new Incident Trigger experience, when entities will be received both from incidents an alerts, we changed the name of the actions Alert - Get IPs/Accounts/URLs/Hosts/Filehashes to Entities - Get IPs/Accounts/URLs/Hosts/Filehashes.
Learn more
Azure Sentinel Connector documentation
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.