- Home
- Security, Compliance, and Identity
- Microsoft Sentinel Blog
- New Azure Sentinel connectors
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Today, we are announcing over a dozen new connectors for leading security solutions that enable data collection and automation scenarios in Azure Sentinel. Customers have diverse environments with different security solutions. These connectors make it easy for customers to collect and analyze their security data from these different security solutions at cloud scale. New workbooks and analytic rule templates are also available to help you monitor these new data sources and detect threats immediately. Refer to the documentation for a complete list of data connectors and Azure Logic Apps custom connectors that you can leverage in Azure Sentinel.
VMware Carbon Black
Use the Carbon Black data connector to ingest Carbon Black events, audit logs and notifications in Azure Sentinel. There is a new workbook as illustrated below, and analytic rule templates on critical threats and malware detections to help you get started immediately.
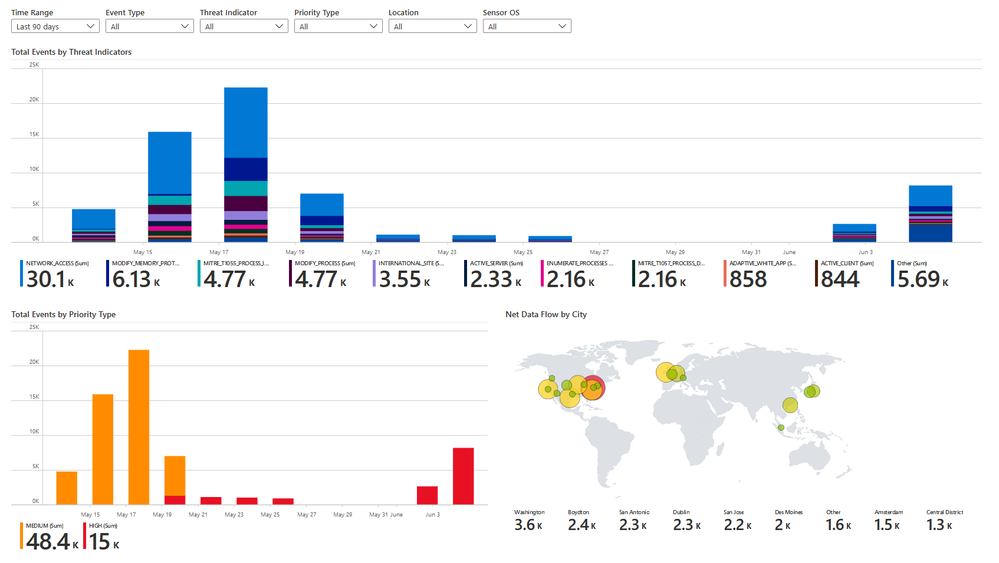
Sophos XG Firewall
Collect Sophos XG Firewall logs using the Sophos data connector and the related workbook to monitor the network traffic and firewall status. Furthermore, enable the port scans and excessive denied connections analytic rules to create custom alerts and track as incidents for the ingested data.
Okta SSO
Okta Single Sign-on audit and event logs can now be easily ingested using the Okta SSO data connector. Monitor user activity and authentication status using the workbook. Enhance your threat detection capability with analytics to track invalid user logins, geolocation logins and password spray attacks.
Symantec
Two new data connectors for Symantec enable you to ingest Symantec Proxy SG (Secure Gateway) and Symantec VIP logs. Use the new workbooks for these data sources to monitor their gateway and authentication logs. Out-of-the-box analytic rule templates for excessive failed authentications, suspicious URL access and denied client and proxy traffic can help with threat detection capabilities as well.
Qualys VM
Use the new Qualys VM data connector to ingest Qualys Vulnerability Management detections. There is a new workbook to monitor Qualys reported vulnerabilities in Azure Sentinel as illustrated below. Detections for new high severity vulnerabilities and high volume of vulnerabilities can enable customized alert generation and incident management in Azure Sentinel.
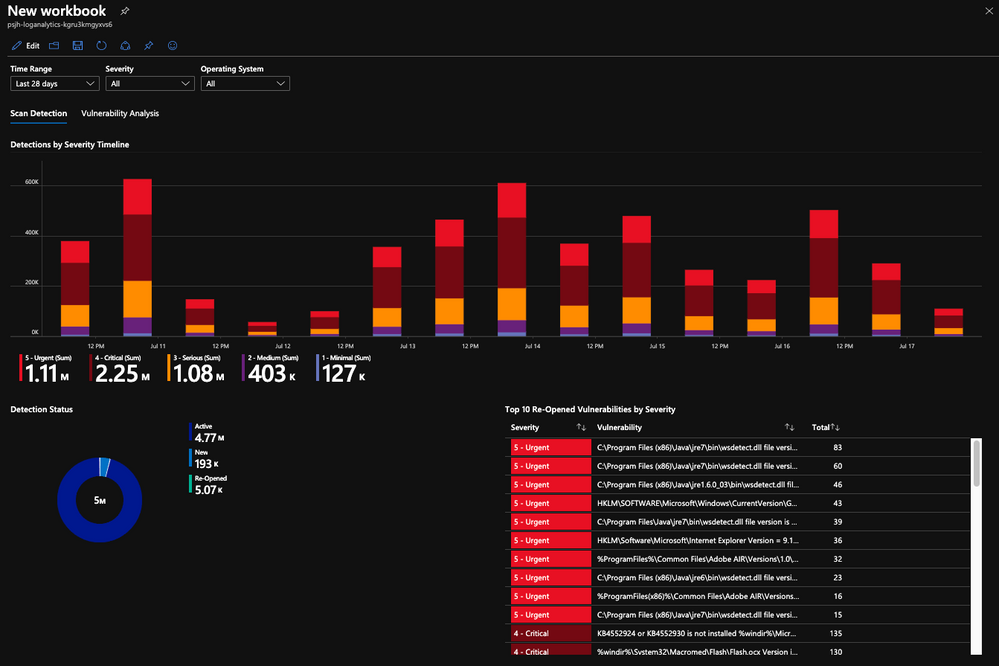
Vectra AI
Use the Vectra data connector to ingest detection analytics from Vectra and the related workbook to drill down into the behavioral analytics and create custom alerts. Refer to the Vectra AI announcement for detailed information.
Proofpoint TAP
Proofpoint Targeted Attack Protection (TAP) logs and events can now be ingested using the Proofpoint TAP data connector. Visualize the message and click logs and events data using the workbook. Use the analytics for malware attachment and malware links clicked for enhanced alerting and incident management.
Infoblox NIOS
Collect your Infoblox Network Identity Operating System (NIOS) logs using the Infoblox NIOS data connector. Drilldown into the DHCP and DNS logs using the workbook. Detect threats using the DHCP starvation attacks and excessive DNS domain queries analytics.
RiskIQ
Tap into threat intelligence feeds from RiskIQ using RiskIQ Azure Logic App connector in playbooks to enrich analytics, incidents and investigation experiences in Azure Sentinel as illustrated below. Deploy one or more of the RiskIQ enrichment playbooks available on the Azure Sentinel GitHub repository to your Azure Sentinel workspace to get started now!
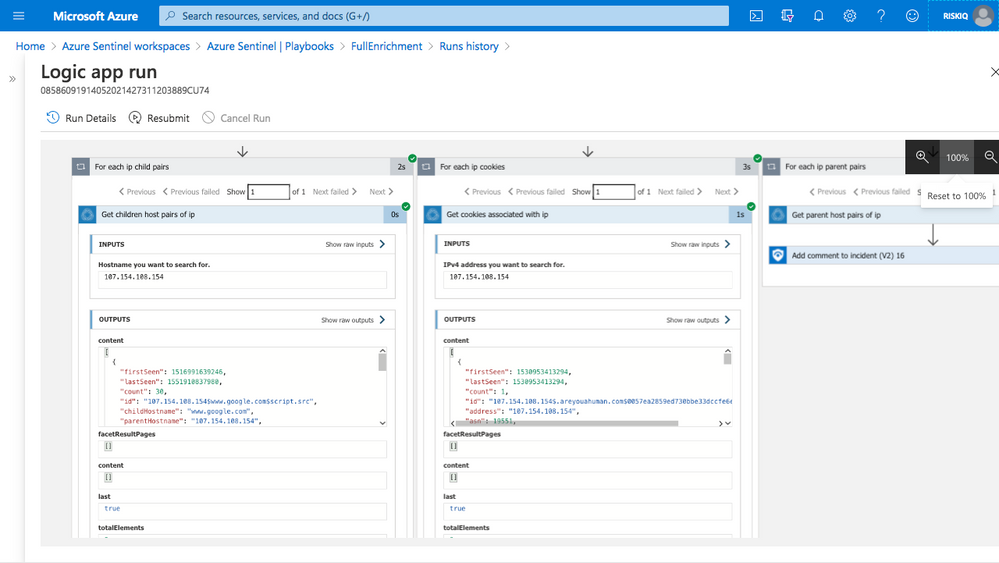
Pulse Connect Secure
Ingest Pulse Connect Secure logs in Azure Sentinel using the Pulse Connect Secure data connector. Monitor your VPN device logs using the workbook. Use the high volume of failed logins and multiple failed VPN user logins analytics to generate custom alerts and manage as incidents.
Perimeter 81
Perimeter 81 activity logs can be ingested using the Perimeter 81 data connector. Use the Perimeter 81 overview workbook to monitor activities like login failure. Create custom alerts using the Perimeter 81 data in Azure Sentinel to detect threats.
Alcide kAudit
Identify anomalous Kubernetes behavior by ingesting the Alcide kAudit activity logs and detections using the Alcide data connector. Build your custom workbooks to monitor the data and create custom analytic rule templates to detect threats using this data.
Illusive Networks
Illusive Attack Management System data connector enables you to ingest Illusive's attack surface analysis data and incident logs. You can view this data in dedicated dashboards that offer insight into organization's attack surface risk (ASM workbook) and track unauthorized lateral movement in your organization's network (ADS workbook).
Orca Security
Ingest Orca Security alerts in Azure Sentinel using the Orca security data connector. Build your custom workbooks to monitor the data and create custom analytic rule templates to detect threats using this data.
Eset
Ingest Eset Security Management Center firewall, threat and audit events using the Eset data connector. Use the workbook to monitor threats pertaining to users and hosts and the Eset SMC detections to get alerted on critical threats and sites blocked by Eset.
Closing
Try out the new connectors, workbooks, and analytics in Azure Sentinel, and let us know your feedback using any of the channels listed in the Resources.
You can also contribute new connectors, workbooks, analytics and more in Azure Sentinel. Get started now by joining the Azure Sentinel Threat Hunters GitHub community and follow the guidance.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.