- Home
- Security, Compliance, and Identity
- Microsoft Sentinel
- Is there a way to aggregate multiple alerts into one incident in Sentinel
Is there a way to aggregate multiple alerts into one incident in Sentinel
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 28 2020 01:41 AM
Within Sentinel we see alerts from various different portals such as Defender Security Center. In the Defender Security Center we have one overview for alerts and one for incidents. One Defender incident can contain multiple alerts, but in Sentinel these alerts are not aggregated. Is there a way to aggregate these alerts in Sentinel into one incident? I really like the incident view in Defender Security Portal, where I see all relevant alerts in one view.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 28 2020 06:44 PM
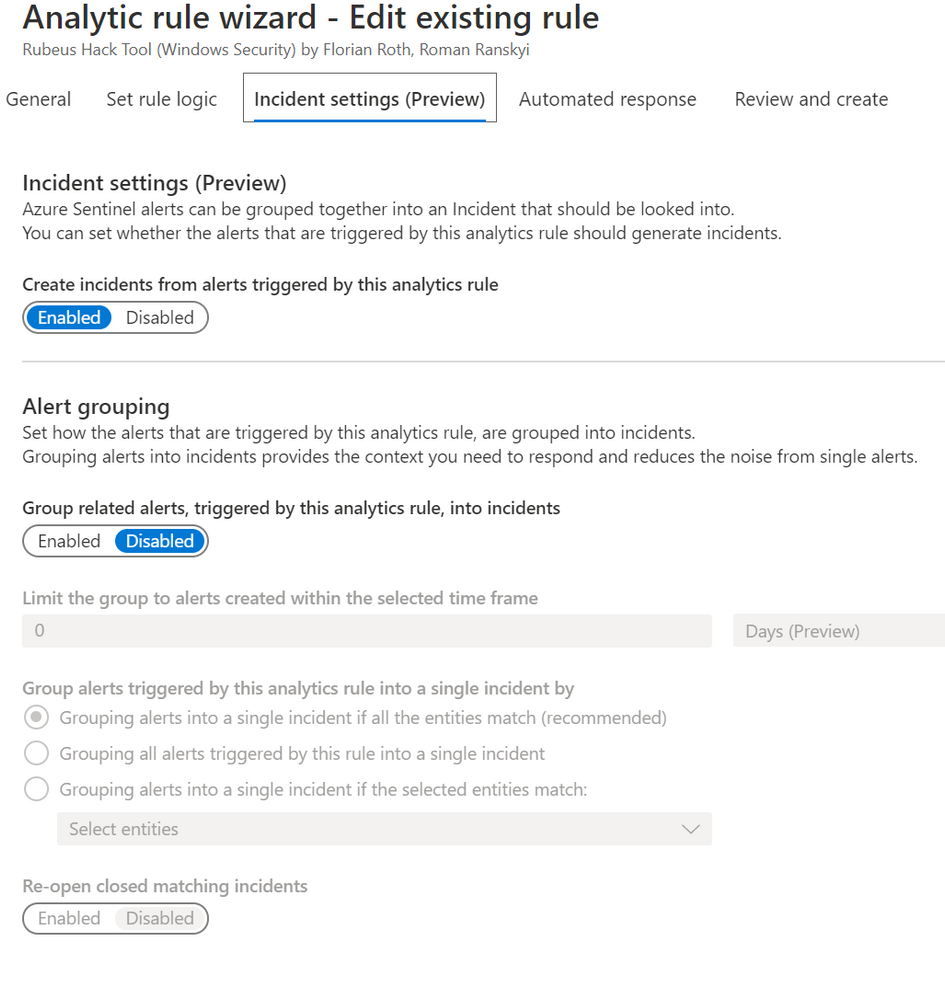
@CurlX have you looked at the Analytic Wizard recently? We now have the ability to group alerts into one incident in public preview:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 29 2020 12:33 AM
I see this option for custom analytics, but not for the in-built ones like "Create incidents based on Microsoft Defender Advanced Threat Protection alerts"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 29 2020 04:04 AM
@CurlX You are correct in that what @Sarah_Young presented only works for Scheduled alerts (sadly). In regards to alerts coming from other Azure security resources, you have no control over them and how they are formatted.
It would probably be worth adding this to the Azure Sentinel Feedback forum at https://feedback.azure.com/forums/920458-azure-sentinel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 30 2020 01:44 AM
@Gary Bushey Thank you, this confirms my assumption. I have opend an "issue / reques".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 01 2020 01:40 AM
@CurlX: One option is to create a scheduled rule for the MDATP alerts. There are differences to account for:
- You need a scheduled rule for each alert aggregation is needed for, and exclude it from the Microsoft rule for MDATP alerts.
- The scheduled rule creates a single alert for multiple MDATP alerts happening in the scheduling window. If you need multiple alerts, say one for each entity, there is a private preview for a feature enabling this. Note that those alerts can still be grouped.
- Lastly, it does imply an up to 5 minutes of additional latency.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 27 2020 09:15 AM
Thank you very much for the information.
I am already using this feature and I am having good results.
One problem I am experiencing is with a grouping function. I configured to group by [account]. When a query is executed, the logs point to two different users, but it generated only one ticket containing the two different entities in the same incident, even with a grouping option per [account].
The correct one should open two incidents, one for each [account], right?
I grouped the rule by the field [id_incident], using the entity [account]. In the raw logs, two types of [incident_id] were generated and only one use case was created containing the two accounts. The correct thing should be two incidents, because there were two different [id_incidents]. Am I correct in my thinking?
Can you help me
in that regard?
Example:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 27 2020 02:44 PM
@luizao_lf : I think that the feature you are looking for is "event grouping" rather than "alert grouping". The former will split each result of the rule query into a differnt alert. See more in the documantation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 28 2020 05:52 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 20 2021 07:42 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 21 2021 04:48 AM