- Home
- Security, Compliance, and Identity
- Microsoft Sentinel Blog
- Azure Sentinel Side-by-Side with QRadar
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Special thanks to “Ofer Shezaf”, “Yaniv Shasha” and “Bindiya Priyadarshini” that collaborating with me on this blog post
As highlighted in my last blog post about Azure Sentinel’s Side-by-Side approach with Splunk, there are in fact reasons that enterprises are using Side-by-Side architecture to take advantage of Azure Sentinel. Side-by-Side is not only about having both SIEMs operating at the same time, but it also provides flexibility for migration of existing SIEM and SOAR use cases to Azure Sentinel.
This blog describes how Azure Sentinel can be used Side-by-Side with QRadar.
The following options are available to ingest Azure Sentinel alerts into QRadar:
- Using the Microsoft Graph Security API
- Using a Logic App flow that streams the alerts to Event Hub. You can read about using Logic Apps here.
This blog post is going to cover the integration with Microsoft Graph Security API.
QRadar can collect events from data sources by using a plug-in called Device Support Module (DSM). IBM provides a DSM to collect data from the Microsoft Graph Security API.
Let’s start the configuration!
Preparation & Use
The following tasks describe the necessary preparation and configurations steps.
- Onboarding Azure Sentinel
- Registration of an application in Azure AD
- Preparation steps in QRadar
- Configuration steps in QRadar
- Using Azure Sentinel alerts in QRadar
Onboarding Azure Sentinel
Onboarding Azure Sentinel is not part of this blog post; however, required guidance can be found here.
Registering an Application in Azure AD
The steps required to register an app in Azure are described here. The registered app requires read access to the SecurityEvents.Read.All field in Microsoft Graph Security API.
For further configuration in QRadar, make a note of following settings:
- The Azure AD Application ID
- The Azure AD Application Secret
- The Tenant ID
Preparation Steps in QRadar
Using the Microsoft Graph Security API DSM to collect alerts from Azure Sentinel requires the following RPMs to be installed on QRadar:
- Protocol Common RPM
- Microsoft Graph Security API Protocol RPM
Download the latest version of RPMs from http://www.ibm.com/support and run the following commands to install the RPMs.
yum -y install DSM-DSMCommon-7.3-20190708191548.noarch.rpm
yum -y install PROTOCOL-MicrosoftGraphSecurityAPI-7.3-20200501003005.noarch.rpm
Preparation Steps in QRadar
Now it is time to use the QRadar portal.
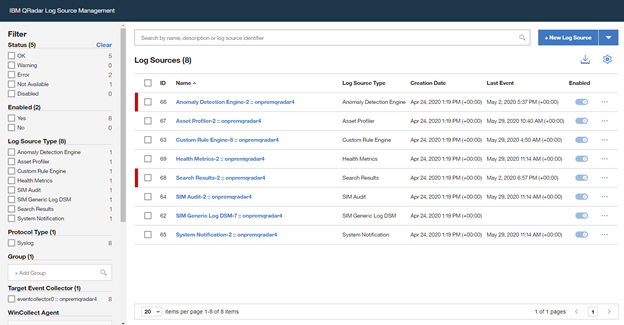
Log on to the “QRadar portal“and click on “Admin“tab
Open the “QRadar Log Source Management“ screen and click on the “+New Log Source” button
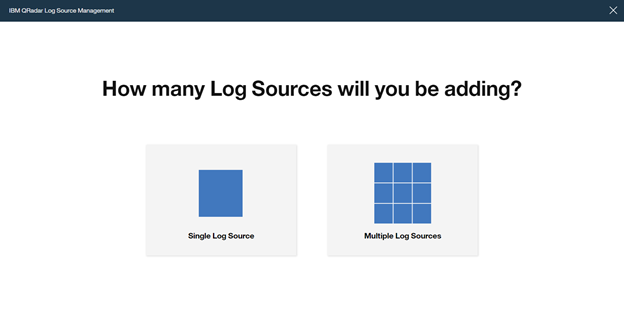
Select “Single Log Source”
Search for "Universal DSM", select it and click on “Step 2: Select Protocol Type”
Search for "Microsoft Graph Security API", select it and click on "Step 3: Configure Log Source Parameters”
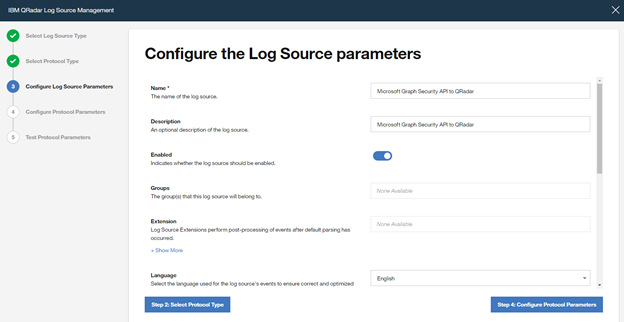
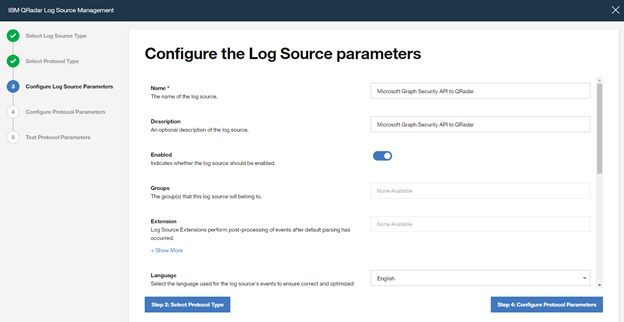
Type a "Name" and a "Description", and configure "other parameters" , and click to "Step 4: Configure Protocol Parameters"
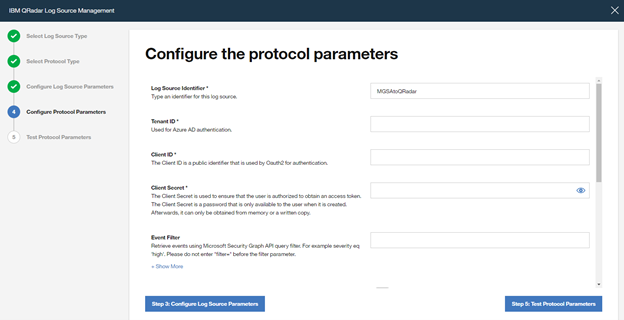
Add a "Log Source Identifier" and specify the parameters noted above when registering the Azure AD app (Azure AD Client ID, Azure AD Client Secret and Tenant ID).
If you want to filter only Azure Sentinel alerts from Microsoft Graph Security API, use the following filter in the parameter "Event Filter".
provider eq 'Azure Sentinel'
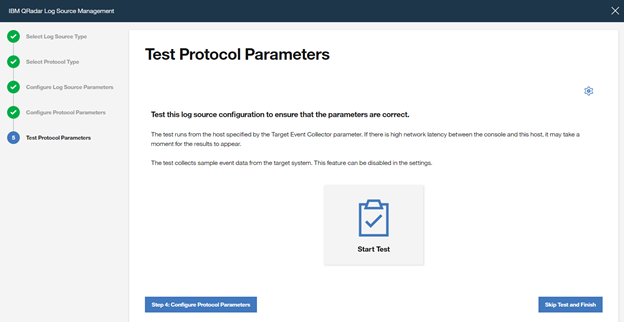
Click on “Step 5: Test Protocol Parameters” to continue with the wizard.
If you want to validate the configuration, click ”Start Test”, otherwise finish the configuration by clicking “Skip Test and Finish”.
Once the wizard is closed, the created "Log Source" is shown on the "Log Source Management" screen.
However, the configuration is not finished yet, it must be deployed in the "QRadar Admin portal". Click on "Deploy Change" to apply the configuration.
Using of Azure Sentinel alerts in QRadar
Once the alerts are ingested, you can query Azure Sentinel alerts in QRadar.
A sample RAW alert from Azure Sentinel collected from Microsoft Security Graph API looks as shown below.
{"eventDateTime": "2020-06-08T10:39:58.3572933Z", "category": "xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx_xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx", "azureSubscriptionId": "xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx", "description": "Identifies when an RDP connection is new or rare related to any logon type by a given account today based on comparison with the previous 14 days.\nRDP connections are indicated by the EventID 4624 with LogonType = 10", "status": "newAlert", "severity": "medium", "title": "Rare RDP Connections", "hostStates": [{"netBiosName": "CLIENT", "fqdn": "CLIENT.DOMAIN.LOCAL"}], "vendorInformation": {"vendor": "Microsoft", "provider": "Azure Sentinel"}, "createdDateTime": "2020-06-22T10:45:00.0929766Z", "lastModifiedDateTime": "2020-06-22T10:45:00.1940637Z", "userStates": [{"userPrincipalName": "user", "emailRole": "unknown", "accountName": "account", "domainName": "domain"}], "id": "xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx", "azureTenantId": "xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx"}
Summary
We just walked through the process of standing up Azure Sentinel Side-by-Side with QRadar. Stay tuned for more Side-by-Side scenarios in our blog channel.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.