- Home
- Security, Compliance, and Identity
- Microsoft Sentinel Blog
- Azure Sentinel and Azure Arc
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Azure Arc was announced very recently https://azure.microsoft.com/en-gb/updates/azure-arc-for-servers-in-public-preview/ and https://azure.microsoft.com/en-gb/updates/azure-arc-for-servers-in-public-preview/
What is Azure Arc - this is the high-level summary:
Azure Arc extends Azure Resource Manager capabilities to Linux and Windows servers, as well as Kubernetes clusters on any infrastructure across on-premises, multi-cloud, and edge. With Azure Arc, customers can also run Azure data services anywhere, realizing the benefits of cloud innovation, including always up-to-date data capabilities, deployment in seconds (rather than hours), and dynamic scalability on any infrastructure. Azure Arc for servers is currently in public preview.
“Azure Arc for servers allows you to manage machines which are outside of Azure. When a non-Azure machine is connected to Azure, it becomes a Connected Machine and is treated as a resource in Azure. Each Connected Machine has a Resource ID, is managed as part of a Resource Group inside a subscription, and benefits from standard Azure constructs such as Azure Policy and tagging.”
This means you see servers in your Azure portal (thanks to Julius Davies for adding these two for me!). These are two on-premises machines, in the Microsoft reading Campus (UK).
You can see the same info in tools like Azure Resource Graph and the Sentinel Logs. Azure Arc machines can be identified as they have a unique ResourceProvider value of
“Microsoft.HybridCompute”. This can help us detect these types of machines in the future. As this is a platform level feature we can use this in workbooks as I will show soon, but also in Incident or Hunting scenarios, you have access to the api or Logs (you do need the MMA for Logs). Let me show you two ways of seeing these servers, outside of the Azure Arc portal:
Azure Resource Graph - example query:
resources
| where type == "microsoft.hybridcompute/machines"
Azure Sentinel Logs - example query:
Heartbeat
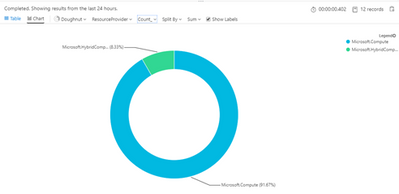
| where ResourceProvider in ("Microsoft.Compute","Microsoft.HybridCompute")
| distinct Computer, ResourceProvider
| summarize count() by ResourceProvider, Computer
You might like to show this as a Pie Chart, and see how your usage of Arc grows over time?
The workbook explained:
1. Download the workbook from here: https://github.com/Azure/Azure-Sentinel/blob/master/Workbooks/SecurityStatus.json
2. See here for import instructions: https://techcommunity.microsoft.com/t5/Azure-Sentinel/How-to-use-Azure-Sentinel-to-follow-a-Users-tr...
I have created some options for you to select; Subscriptions, Workspaces, Time and a Computer. This will also work with Azure Lighthouse so works for an MSSP or if you have multiple Azure Directories in your organisation.
So let’s now choose a Computer:
We see this report.
For this I’m using a Azure Resource Graph Query, looking at the “securityresources” information - see lines 1 & 2 below. More resources can be found here: https://docs.microsoft.com/en-us/azure/governance/resource-graph/concepts/explore-resources
securityresources
| where type == "microsoft.security/securitystatuses"
| where name =~ '{Computer}'
| extend p=array_length(properties.resourceDetails)
| mvexpand prop=properties.resourceDetails
| parse id with *"/providers/" res "/machines/" *
| extend type = iif (res == "microsoft.hybridcompute", "HybridCompute-Arc","AzureCompute")
| project ComputerName = name, Resource= prop.name, Status = prop.value, type
This works by looking at securityresources, then getting the computer name from our drop down (line #3), I then get some of the property fields (you may need more/less). I also parse the ResourceID column to get the Resource Provider Name, if its “microsoft.hybridcompute” then I display that its Azure Arc in the type column, else it must be AzureCompute
If we swap the drop-down to a computer that is managed by Azure Arc we see
Now, you will see the “type” column detects it, but there isn’t yet a lot of other information about this Azure Arc machine, hopefully this will improve in time. However in my case, this machine is also in Azure Security Center so in my 1st Chart of the workbook you see, its ASC Security Event status:
Note: there are a 2nd and 3rd Chart area for CEF and Syslog (not shown, but you can open the workbook to see them). I also check and provide a map if the computer chosen has any MaliciousIP data (see previous posts for that).
Azure Arc area:
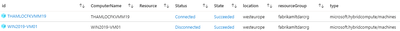
I also created a dedicated area in the workbook for Azure Arc. This is a display area where I show any Azure Arc machines (using ARG); using the basic query of:
resources
| where type == "microsoft.hybridcompute/machines"
You can update this query a bit yourself (edit the workbook), maybe to this:
resources
| where type == "microsoft.hybridcompute/machines"
| extend p=array_length(properties.provisioningState)
| mvexpand prop=properties.provisioningState
| project id, ComputerName = name, Resource= prop.name, Status = properties.status, State=prop, location, resourceGroup, type
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.