- Home
- Security, Compliance, and Identity
- Microsoft Defender for IoT Blog
- Azure Defender for IoT Raw-Data and ICS MITRE ATT&CK Matrix Mapping via Azure Sentinel
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Overview
Happy New Year everyone!
Thanks to @amitsheps (Azure Defender for IoT Senior Program Manager) and @paulrob (Azure Defender for IoT Global Black Belt) for the brainstorming, contributing, reviewing and proof reading!
To enable rapid detection and response for attacks that cross IT/OT boundaries, Azure Defender is deeply integrated with Azure Sentinel—
- Deep integration with Azure Defender for IoT: Azure Sentinel provides rich contextual information about specialized OT devices and behaviors detected by Azure Defender—enabling your SOC teams to correlate and detect modern kill-chains that move laterally across IT/OT boundaries.
- IoT/OT-specific SOAR playbooks: Sample playbooks enable automated actions to swiftly remediate IoT/OT threats.
- IoT/OT-specific threat intelligence: In addition to the trillions of signals collected daily, Azure Sentinel now incorporates IoT/OT-specific threat intelligence provided by Section 52, our specialized security research team focused on IoT/OT malware, campaigns, and adversaries.
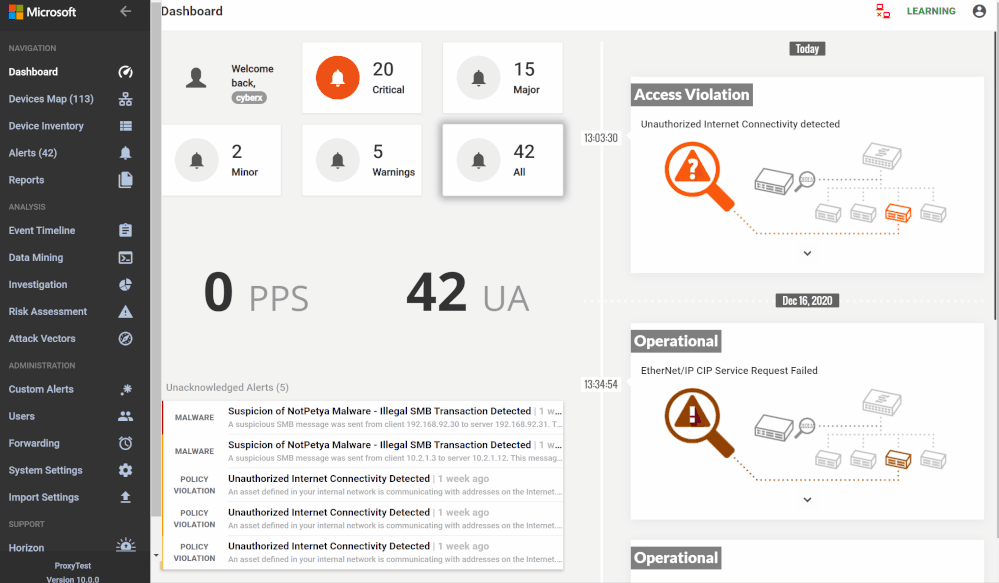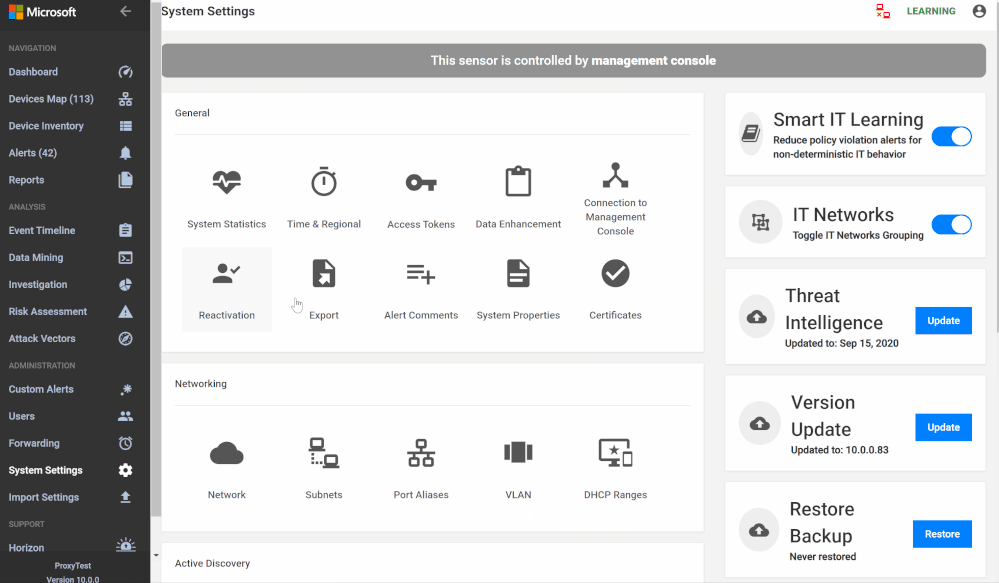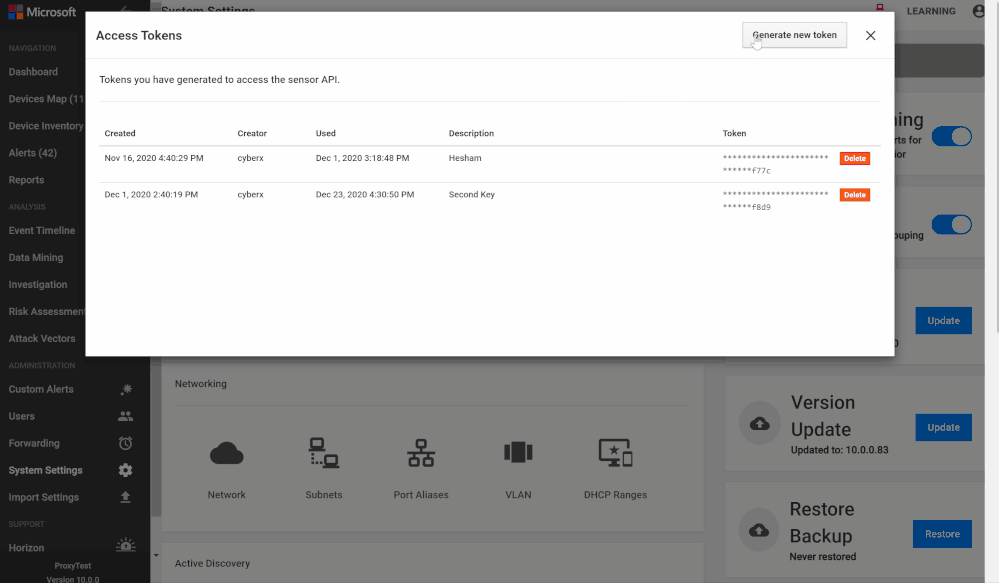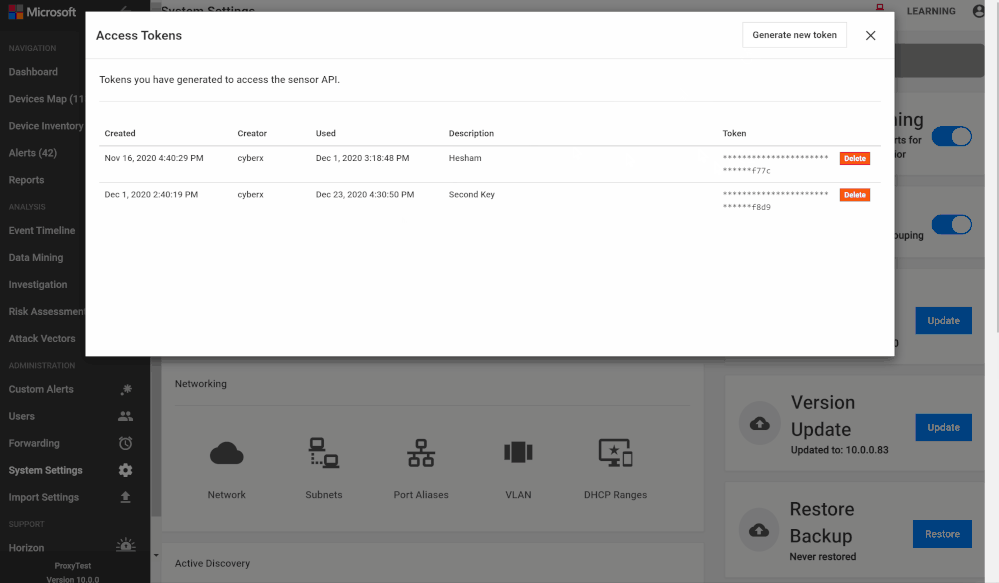
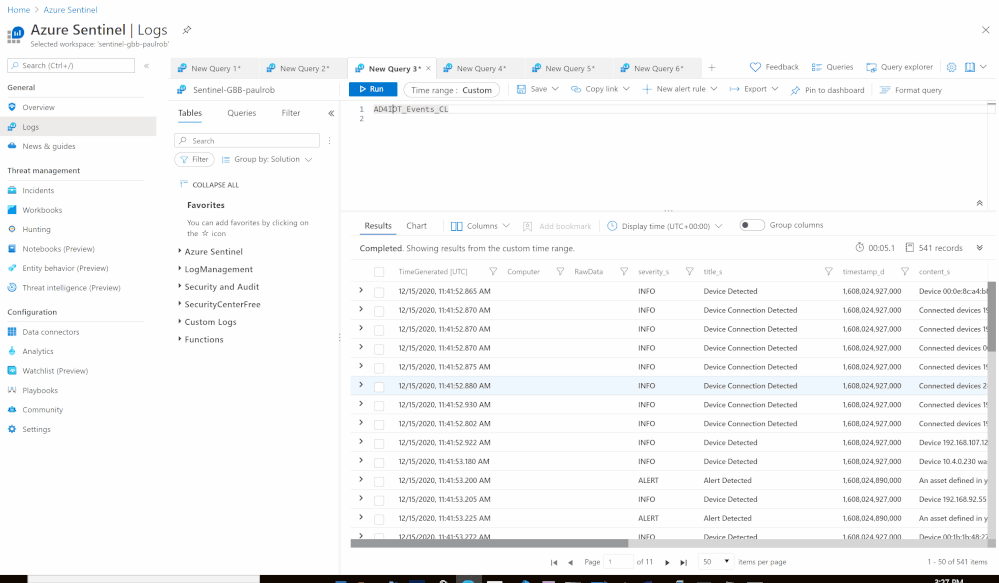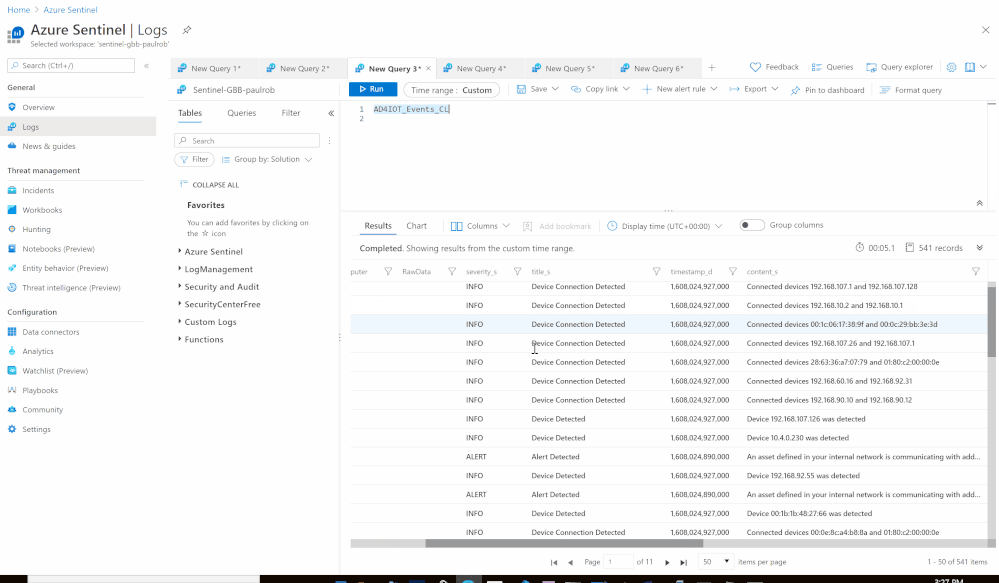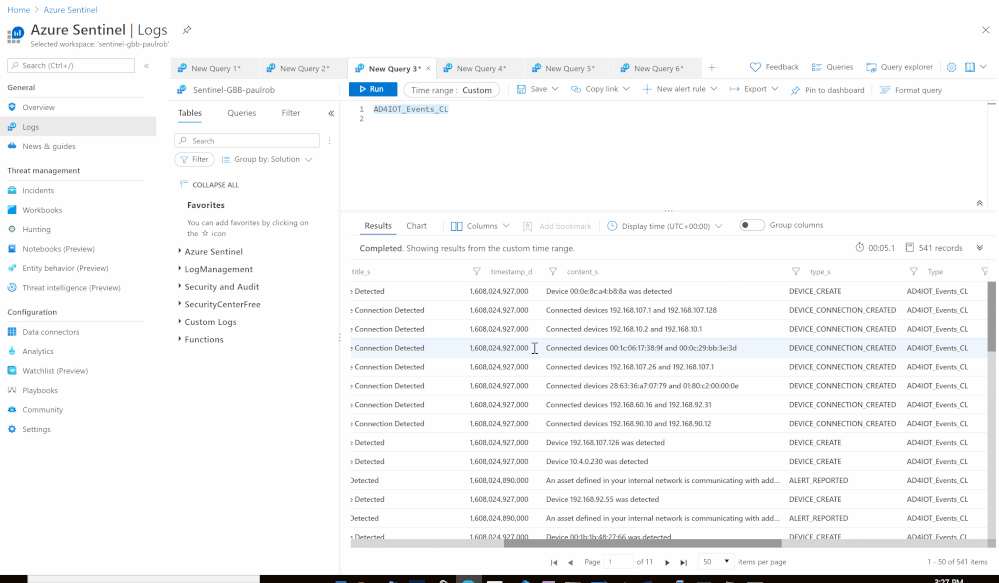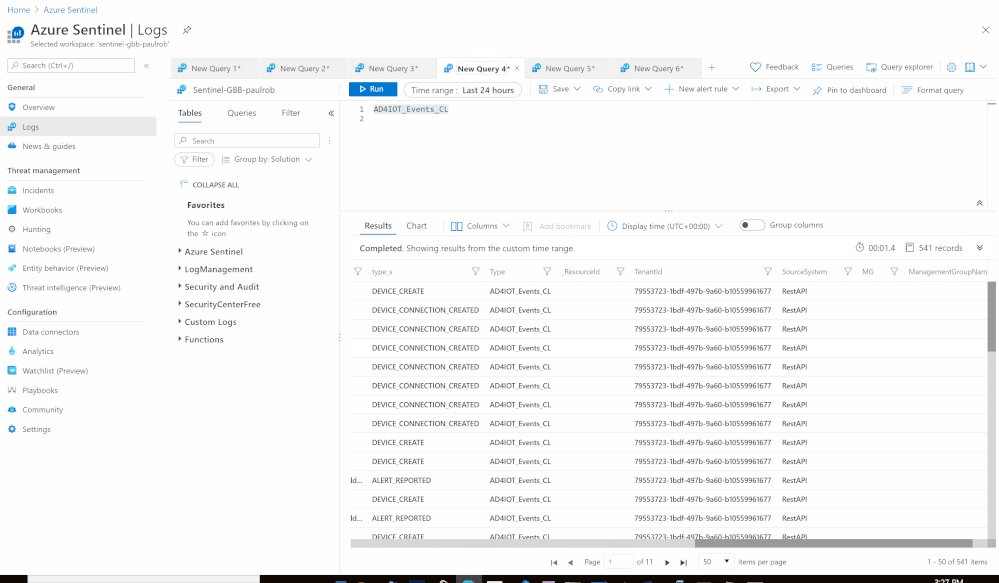
Using the Azure Sentinel Out-of-the box Azure Defender for IoT data connector (tagged as: "Azure Security Center for IoT (Preview)"), you will be able to easily pull Defender for IoT alerts to Azure Sentinel for further correlation, aggregation, investigations & detections. For more details please visit Connect your data from Defender for IoT to Azure Sentinel (preview)
Here's an example of correlating OT alerts in Azure Sentinel:
Use Case
SOC requirements is to ingest Azure Defender for IoT "Raw-Data" to Azure Sentinel and build set of analytics rules for further correlation activities & detections covering the entire MITRE ATT&CK ICS matrix and further use cases, Achieving full coverage of the IoT and ICS threats described in the ATT&CK for ICS framework not only positions you to protect your networks against the threats that exist today, it also prepares you for the new ones that will, inevitably, appear in the future.
Crafting an IoT/ICS security approach capable of this requires a combination of capabilities: you need full visibility into your assets, proactive risk management to address vulnerabilities that could be exploited by adversaries, and M2M analytics to provide continuous network security monitoring.
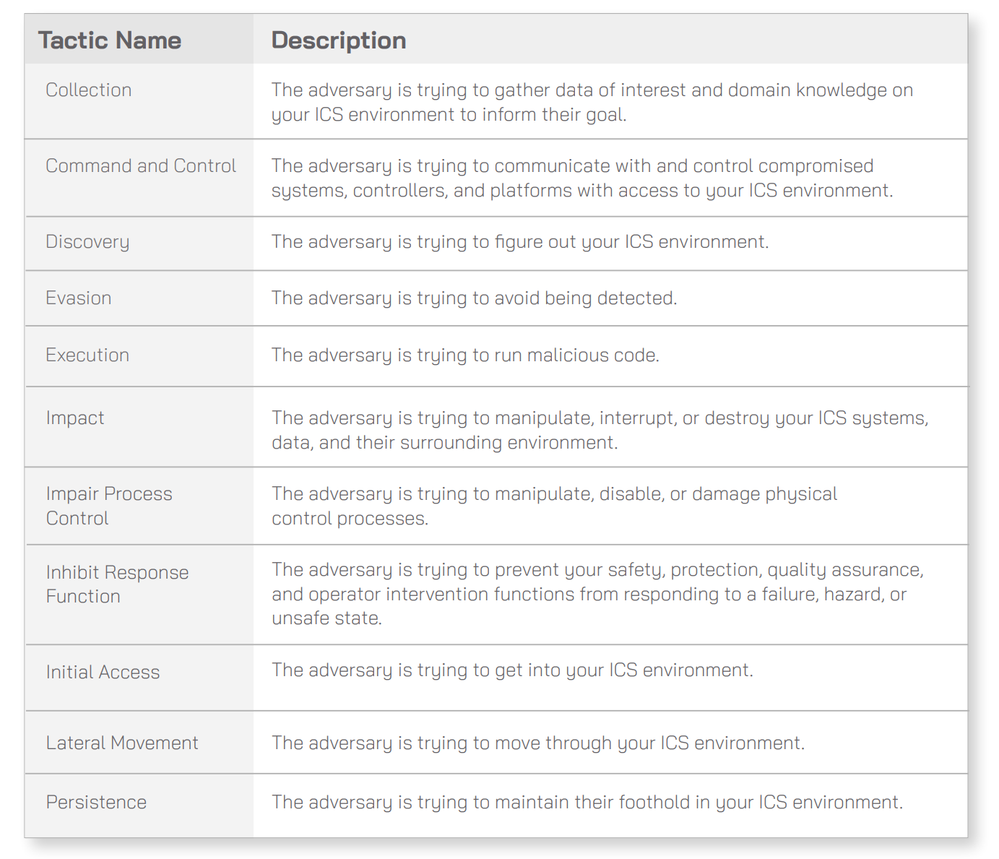
In January 2020 MITRE has addressed the gap with the ATT&CK for ICS Framework. Cataloging the unique adversary tactics adversary use against facing IoT/ICS environments. The framework consists of eleven tactics that threat actors use to attack an ICS environment, which are then broken down into specific techniques. Ultimately, this database describes every stage of an ICS attack from initial compromise to ultimate impacts.
The 11 tactics described above are listed across the top column in the table on. Beneath each column header are techniques used by attackers to perform the respective tactic. The techniques listed are not necessarily unique to any one specific tactic:
The techniques that Azure Defender for IoT detects immediately are in green boxes. The
techniques that Azure Defender for IoT can detect after the initial compromise or where Azure Defender for IoT can detect via integration and correlation with other security technologies, such as Azure Sentinel, are in tan boxes, for more details please click here:
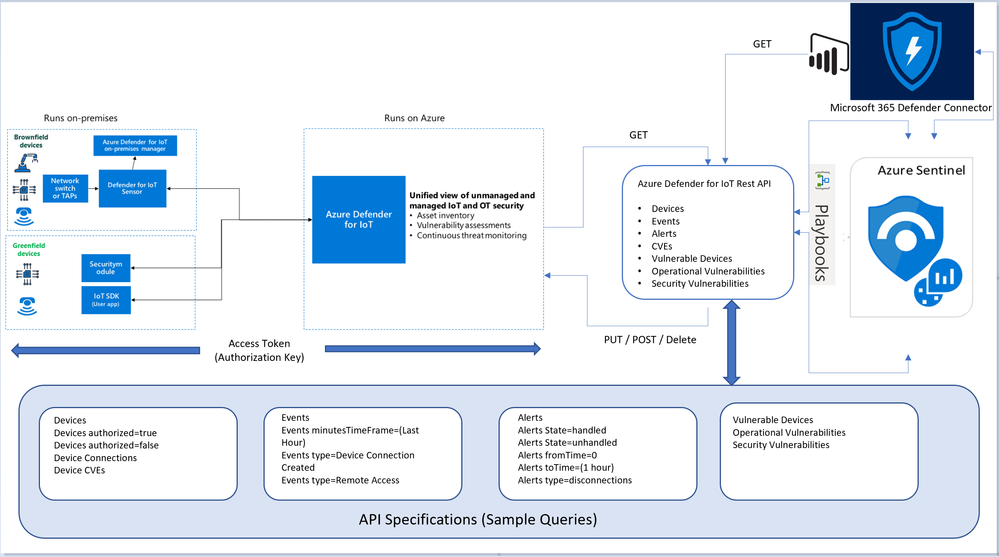
Architecture
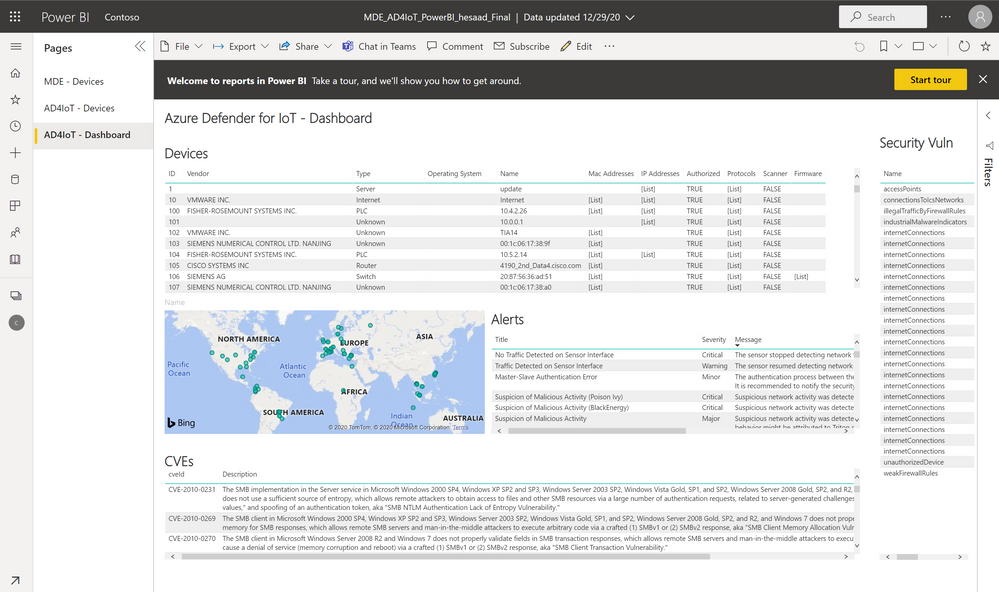
Looking for Microsoft Defender for Endpoint PowerBI connected application that pull both Azure Defender for IoT Raw-Data & Microsoft Defender for Endpoint via APIs here's the architecture and guidance, also a sample MDE_AD4IoT_PowerBI_Sample.pbit template uploaded to github (ensure amending the Sensor URL and Authorization key values):
Implementation
- Log in to the Azure Defender for IoT central manager console, System Settings > Access Tokens
- Select Generate new token, describe the purpose of the new token and select
- Copy the token, save it and select finish
- Go to Azure Sentinel > Playbooks
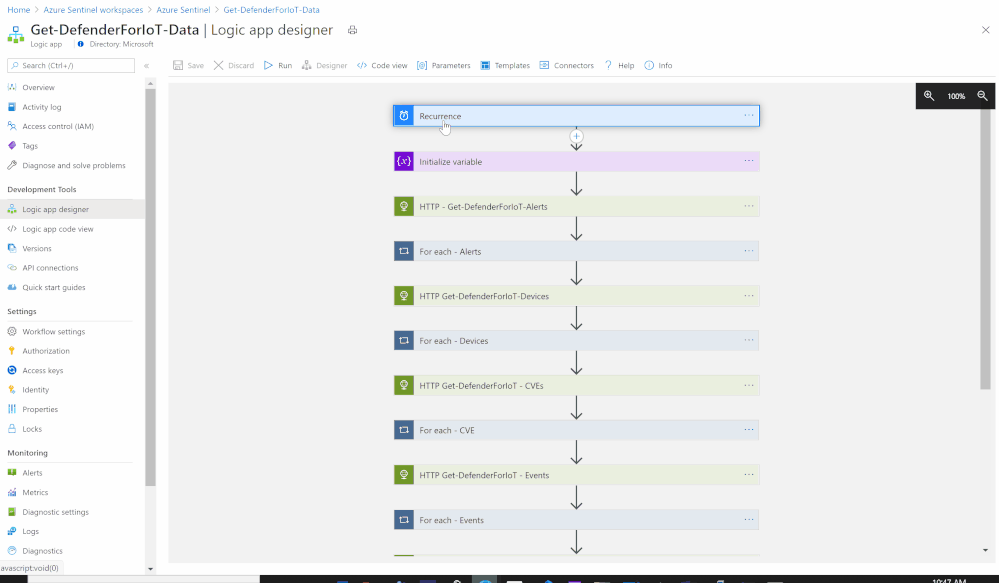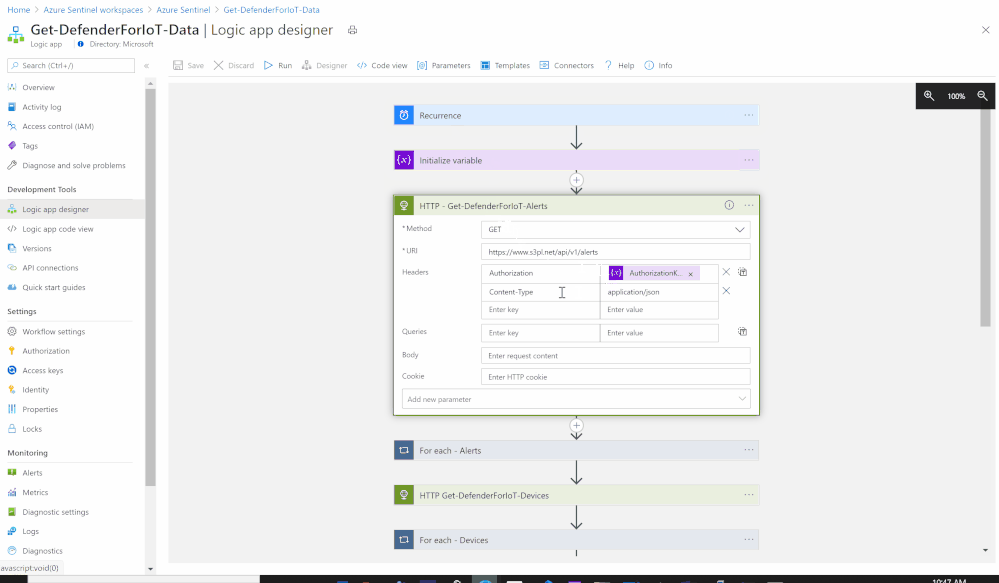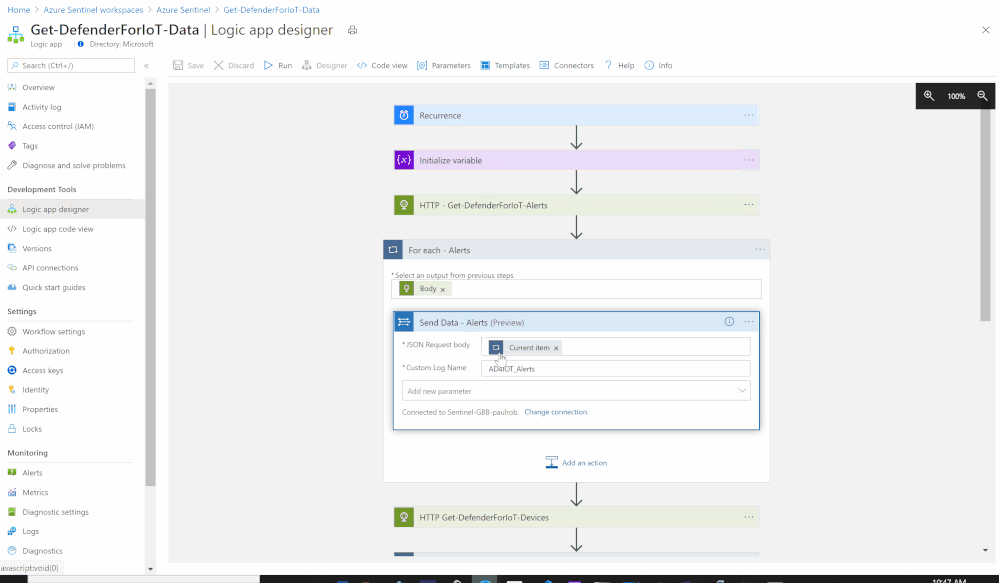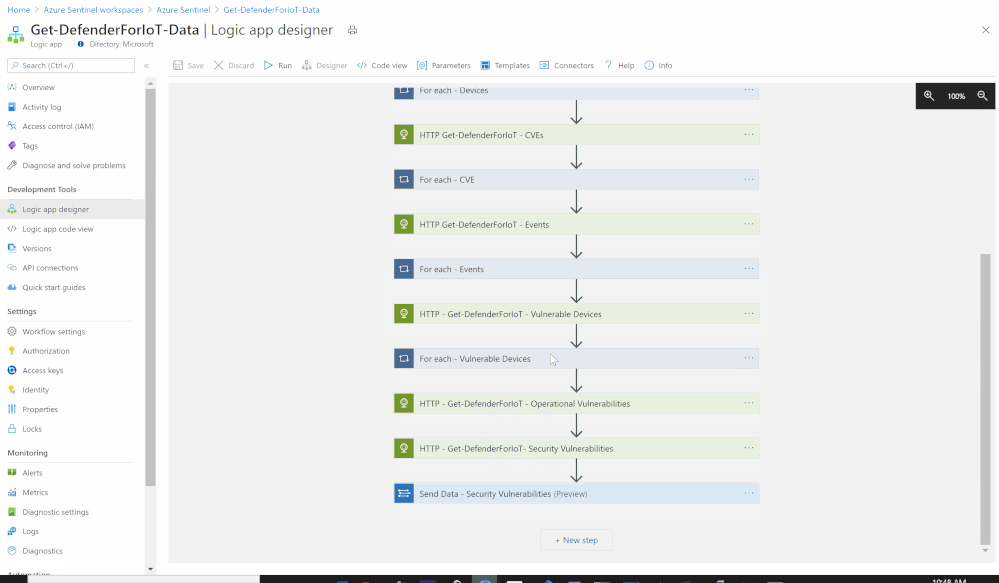
- Create a new Playbook and follow the below gif / step-by-step guide, the code being uploaded to github repo as well:
- Add a “Recurrence” step and set the following field, below is an example to trigger the Playbook once a daily basis:
- Interval: 1
- Frequency: Day
- Initialize a variable for the Azure Defender for IoT Sensor Access Token (Authorization Key):
- Name: AuthorizationKey
- Type: String
- Value: X1X0XXX5XXXXXbXXX0XXX
- Set an HTTP endpoints to Get Azure Defender for IoT Alerts data:
- HTTP - Get-DefenderForIoT-Alerts:
- Method: GET
- URI: https://<Defender_for_IoT_Sensor>/api/v1/alerts
- Headers:
- Key: Authorization, Value: @variables('AuthorizationKey')
- Key: Content-Type, Value: application/json
- HTTP - Get-DefenderForIoT-Alerts:
- Add For each control to iterate Azure Defender for IoT Alerts items:
- Select an output from previous steps: @body('HTTP_-_Get-DefenderForIoT-Alerts')
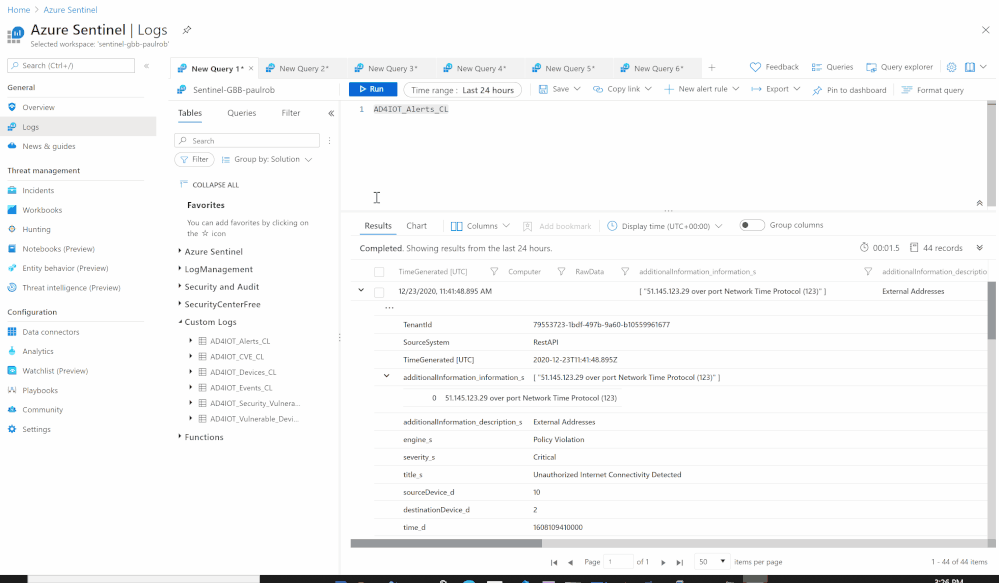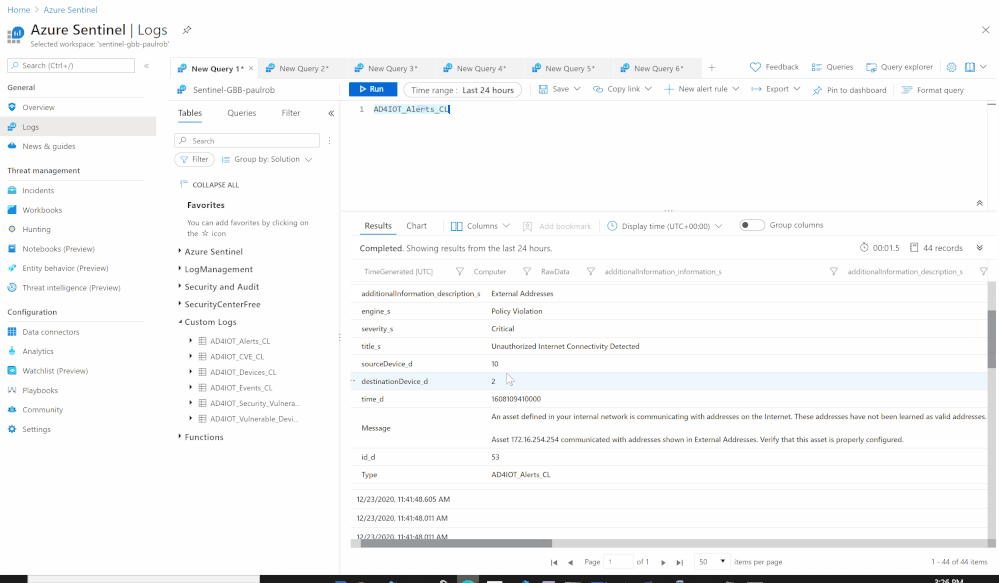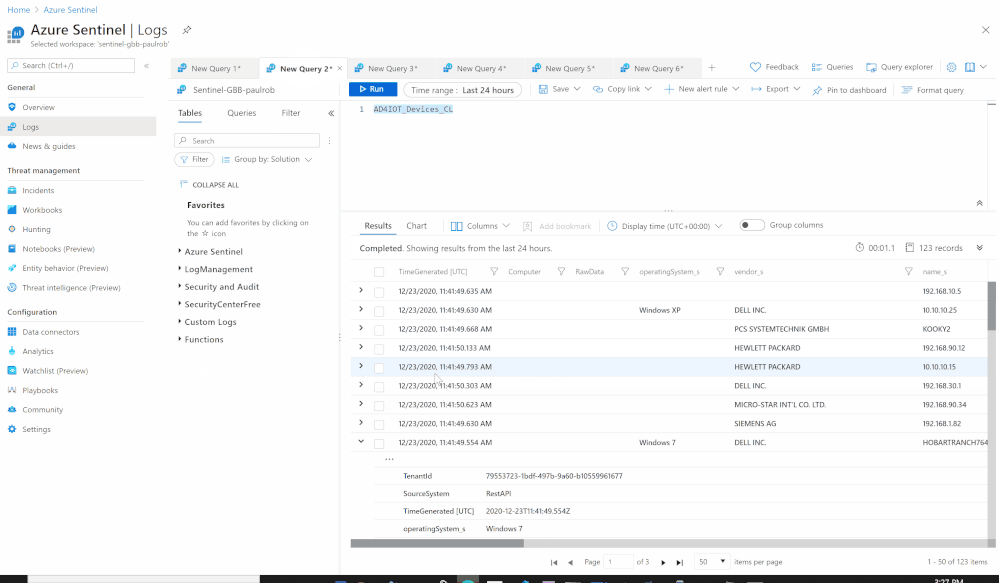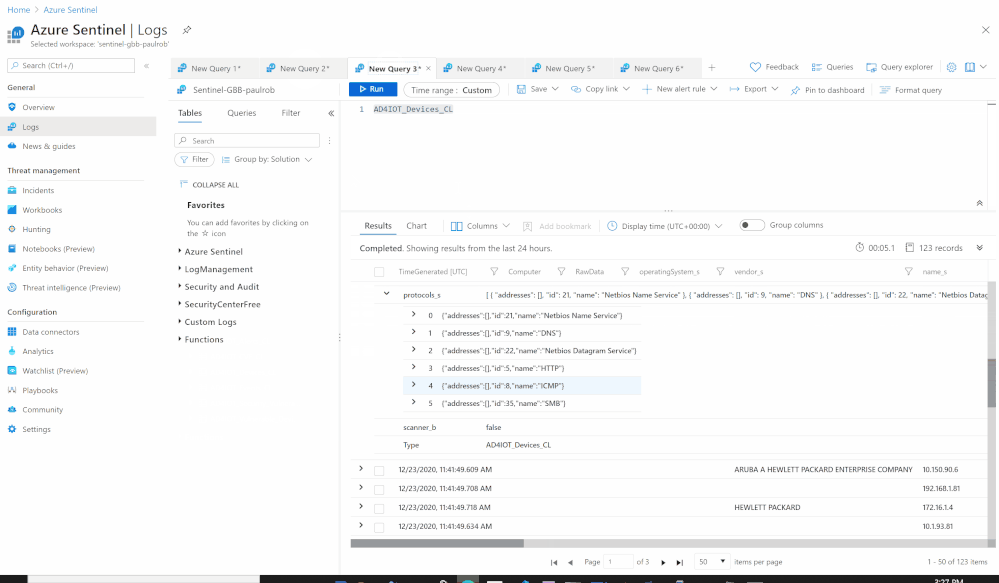
- Send the data (Alerts) to Azure Sentinel Log analytics workspace via a custom log tables:
- JSON Request body: @{items('For_each_-_Alerts')}
- Custom Log Name: AD4IOT_Alerts
- Set an HTTP endpoints to Get Azure Defender for IoT Devices data:
- HTTP - Get-DefenderForIoT-Devices:
- Method: GET
- URI: https://<Defender_for_IoT_Sensor>/api/v1/devices
- Headers:
- Key: Authorization, Value: @variables('AuthorizationKey')
- Key: Content-Type, Value: application/json
- HTTP - Get-DefenderForIoT-Devices:
- Add For each control to iterate Azure Defender for IoT Devices items:
- Select an output from previous steps: @body('HTTP_Get-DefenderForIoT-Devices')
- Send the data (Devices) to Azure Sentinel Log analytics workspace via a custom log tables:
- JSON Request body: @{items('For_each_-_Devices')}
- Custom Log Name: AD4IOT_Devices
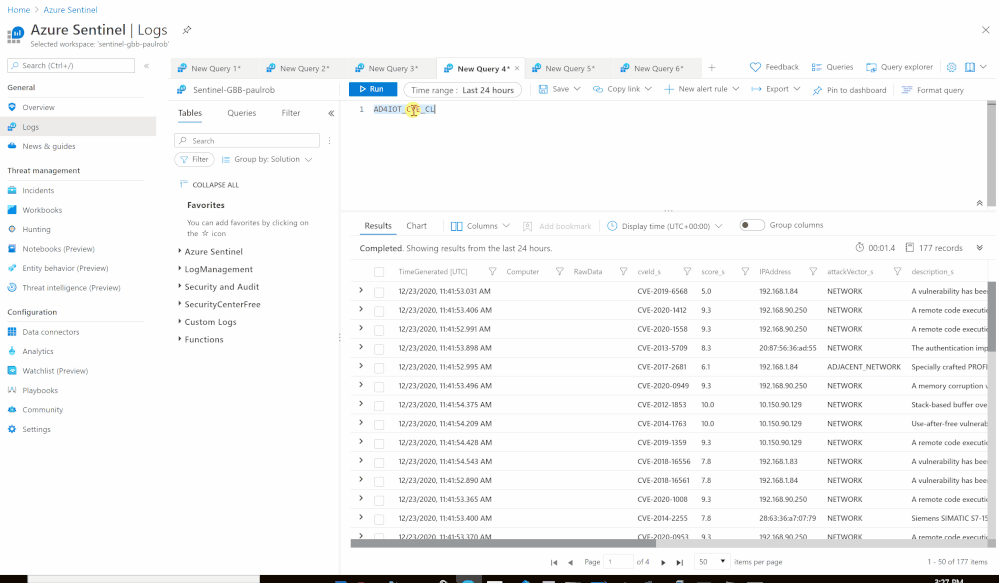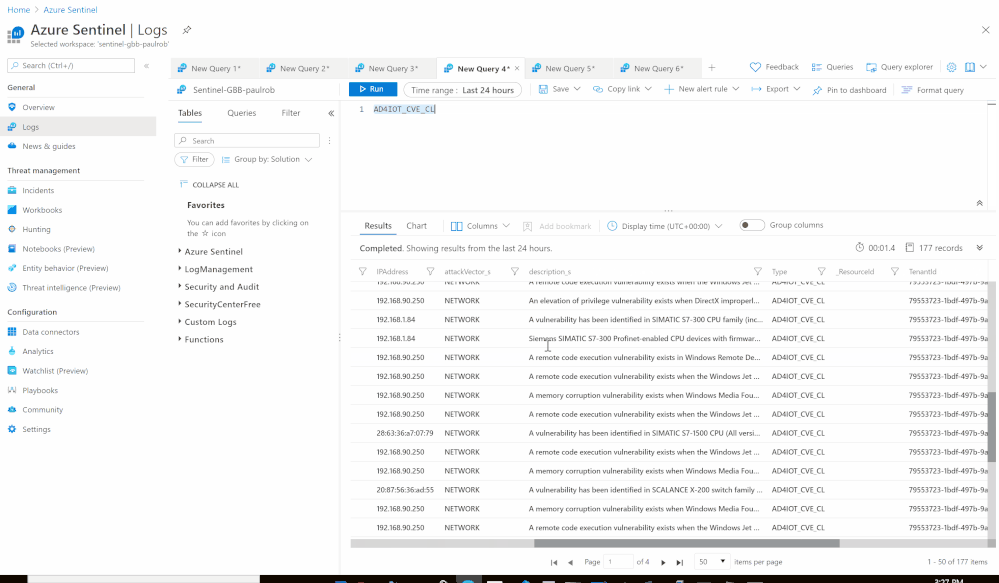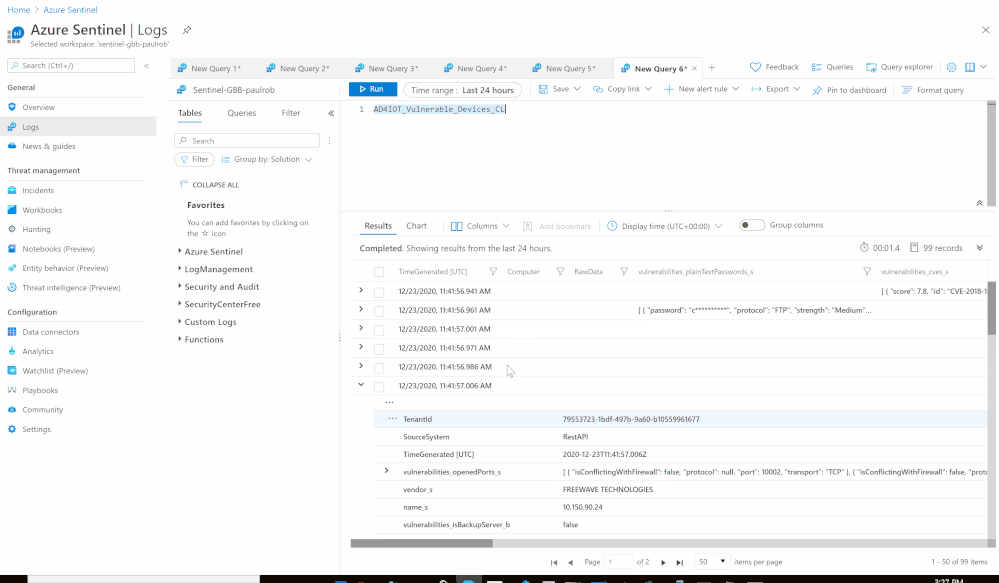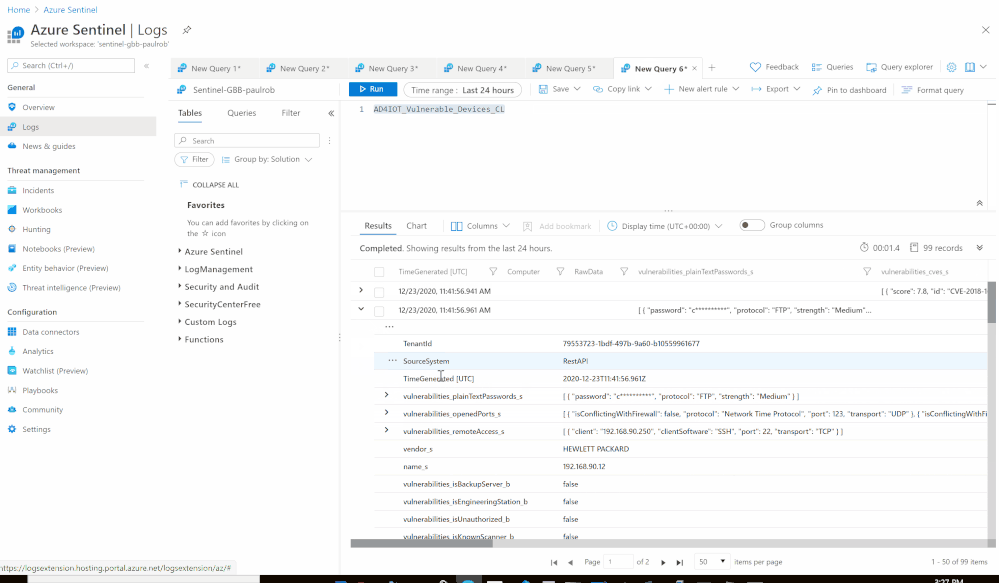
- Set an HTTP endpoints to Get Azure Defender for IoT CVEs data:
- HTTP - Get-DefenderForIoT-CVEs:
- Method: GET
- URI: https://<Defender_for_IoT_Sensor>/api/v1/devices/cves
- Headers:
- Key: Authorization, Value: @variables('AuthorizationKey')
- Key: Content-Type, Value: application/json
- HTTP - Get-DefenderForIoT-CVEs:
- Add For each control to iterate Azure Defender for IoT CVEs items:
- Select an output from previous steps: @body('HTTP_Get-DefenderForIoT_-_CVEs')
- Send the data (CVEs) to Azure Sentinel Log analytics workspace via a custom log tables:
- JSON Request body: @{items('For_each_-_CVE')}
- Custom Log Name: AD4IOT_CVE
- Set an HTTP endpoints to Get Azure Defender for IoT Events data:
- HTTP - Get-DefenderForIoT-Events:
- Method: GET
- URI: https://w<Defender_for_IoT_Sensor>/api/v1/events
- Headers:
- Key: Authorization, Value: @variables('AuthorizationKey')
- Key: Content-Type, Value: application/json
- HTTP - Get-DefenderForIoT-Events:
- Add For each control to iterate Azure Defender for IoT Events items:
- Select an output from previous steps: @body('HTTP_Get-DefenderForIoT_-_Events')
- Send the data (Events) to Azure Sentinel Log analytics workspace via a custom log tables:
- JSON Request body: @{items('For_each_-_Events')}
- Custom Log Name: AD4IOT_Events
- Set an HTTP endpoints to Get Azure Defender for IoT Vulnerable Devices data:
- HTTP - Get-DefenderForIoT-Vulnerable Devices:
- Method: GET
- URI: https://<Defender_for_IoT_Sensor>/api/v1/reports/vulnerabilities/devices
- Headers:
- Key: Authorization, Value: @variables('AuthorizationKey')
- Key: Content-Type, Value: application/json
- HTTP - Get-DefenderForIoT-Vulnerable Devices:
- Add For each control to iterate Azure Defender for IoT Vulnerable Devices items:
- Select an output from previous steps: @body('HTTP_-_Get-DefenderForIoT_-_Vulnerable_Devices')
- Send the data (Vulnerable Devices) to Azure Sentinel Log analytics workspace via a custom log tables:
- JSON Request body: @{items('For_each_-_Vulnerable_Devices')}
- Custom Log Name: AD4IOT_Vulnerable_Devices
- Set an HTTP endpoints to Get Azure Defender for IoT Operational Vulnerabilities data:
- HTTP - Get-DefenderForIoT-Operational Vulnerabilities:
- Method: GET
- URI: https://<Defender_for_IoT_Sensor>/api/v1/reports/vulnerabilities/operational
- Headers:
- Key: Authorization, Value: @variables('AuthorizationKey')
- Key: Content-Type, Value: application/json
- HTTP - Get-DefenderForIoT-Operational Vulnerabilities:
- Set an HTTP endpoints to Get Azure Defender for IoT Security Vulnerabilities data:
- HTTP - Get-DefenderForIoT-Security Vulnerabilities:
- Method: GET
- URI: https://<Defender_for_IoT_Sensor>/api/v1/reports/vulnerabilities/security
- Headers:
- Key: Authorization, Value: @variables('AuthorizationKey')
- Key: Content-Type, Value: application/json
- HTTP - Get-DefenderForIoT-Security Vulnerabilities:
- Add For each control to iterate Azure Defender for IoT Vulnerable Security Vulnerabilities items:
- Select an output from previous steps: @body('HTTP_-_Get-DefenderForIoT_-_Vulnerable_Devices')
- Send the data (Security Vulnerabilities) to Azure Sentinel Log analytics workspace via a custom log tables:
- JSON Request body: @{body('HTTP_-_Get-DefenderForIoT-_Security_Vulnerabilities')}
- Custom Log Name: AD4IOT_Security_Vulnerabilities
- Add a “Recurrence” step and set the following field, below is an example to trigger the Playbook once a daily basis:
Notes & Consideration
- In case if there is any technical requirement of not allowing using Azure Defender for IoT in the cloud and require to run On-premises, you can rely on local Logic App gateway for API calls for outbound traffic instead of inbound, for more details Install on-premises data gateway for Azure Logic Apps
- You can easily build a parser at the connector's flow with the required and needed attributed / fields based on your schema / payload before the ingestion process, also you can create custom Azure Functions once the data being ingested to Azure Sentinel
- You can build your own detection and analytics rules / use cases leveraging the raw data and mapping to ICS MITRE ATT&CK, a couple of custom analytics rules will be ready to use at github, stay tuned
- For more details about Microsoft Defender for Endpoint (MDE) PowerBI connected application integration, check out MDE - Create custom reports using Power BI and also Migrate the old Power BI App to Microsoft Defender ATP Power BI templates blog post by @Thorsten Henking as we referenced it in creating the custom PowerBI template
- Couple of points to be considered while using Logic Apps:
- Cost (standard / enterprise connectors)
- Considerations & Configurations
- Non standard schema
- Rewriting rules
Get started today!
We encourage you to try it now!
You can also contribute new connectors, workbooks, analytics and more in Azure Sentinel. Get started now by joining the Azure Sentinel Threat Hunters GitHub community.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.