- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- Validating Microsoft Defender for Storage Detections
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Microsoft Defender for Storage provides an additional layer of security intelligence that can be used to detect unusual and potentially harmful attempts to access or exploit storage accounts. This feature can be enabled via Microsoft Defender for Storage or on each individual Azure Storage account. The main difference is that if you enable on Microsoft Defender for Storage, it will apply to all storage accounts in the subscription that Microsoft Defender for Cloud is enabled.
The goal of this post is to explain how to validate the Microsoft Defender for Storage account detection, by uploading a testing malware file (EICAR) to the storage account using Storage Explorer. To follow the steps in this lab, make sure to enable the Microsoft Defender for Storage under Settings – Pricing Tier blade in Microsoft Defender for Cloud:
After enabling Microsoft Defender for Storage in Microsoft Defender for Cloud, follow the steps below:
1. Create a new Storage Account
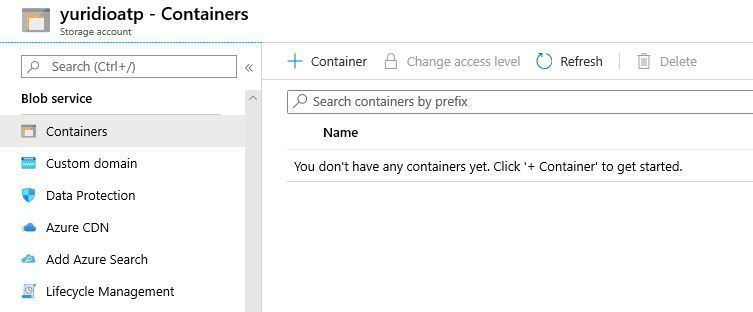
2. Open the Storage Account that you created, and under Blob Service, click Containers:
3. Click the + Container button to create a new container
4. Under name, type storageatpvalidation and leave the public access to private.
5. Click OK to create.
6. Download Storage Explorer on the computer that you will use to upload the test file (EICAR).
7. On this computer, create a text file using Notepad and copy the following string into it:
X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*
8. Save the text file as “EICAR.com” (or any other name if you want)
9. Open Storage Explorer and add your Azure account to it.
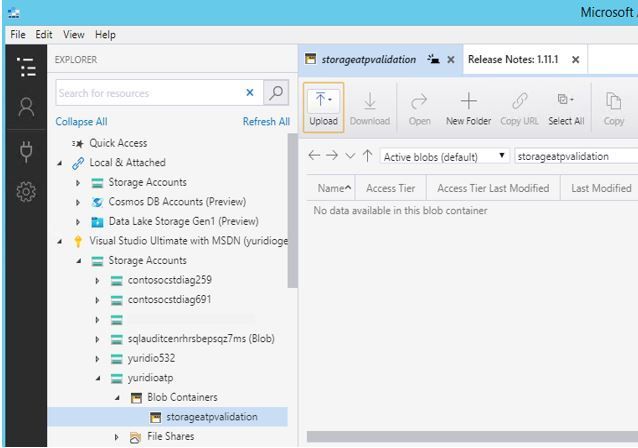
10. Open the storage account that you just created and under Blob Containers, click on the container that you created as shown below:
11. Click Upload button on the right pane and select Upload files.
12. Under Selected files, click the three dots to open the dialog window and select the EICAR file.
13. Click upload and wait until you see that the file was uploaded.
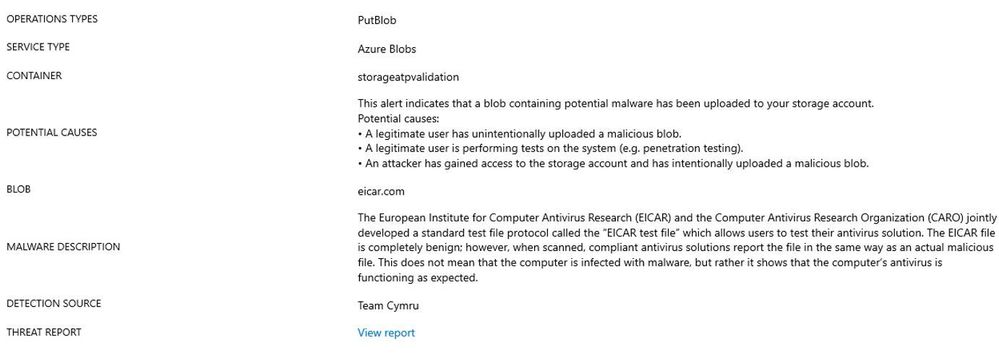
At this point you just need to wait until the detection takes place (which can take a little while). Once the detection takes place, a new alert will be generated in Microsoft Defender for Cloud, similar to the one below:
This alert also contains some useful information about potential cause, and threat report towards the end of the blade:
You will also receive an email similar to the one below (read this blog post for more info about email notification):
The email contains the entire information available in the alert, but for the purpose of this blog, only partial part of the email content was used.
Get started today
It is incredibly easy to enable Microsoft Defender for your storage accounts using Azure Portal, Azure Policy , Rest API or PowerShell
We encourage you to try it out for Free for the first 30 days . You can learn more about Microsoft Defender for Storage alerts and how to enable it on the getting started page.
Special thanks to:
Hasan Abo-Shally, Guy Waldman, Yoav Frandzel and Ron Matchoro for contributing and reviewing this post.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.