- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- Security Control: Remediate Vulnerabilities
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
We are bringing this blog post to continue our series for the re-vamped Azure Security Center (ASC) Secure Score, and to educate the masses on the importance of ASC and what it can offer our customers…aka YOU. Ultimately the end result is to enhance everyone’s security footprint as much as possible leveraging one of the most (if not THE most) powerful forces of compute power on the planet.
Why is this important you might ask? Well, how would you like to be driving along in your car…and suddenly, your wheel falls off? Or the engine catches on fire? Or…<insert dramatic auto event here>. Something bad could happen to your vehicle if you didn’t check things out first and remediate any potential problems. Like making sure your lug nuts are all tightened up before a long drive…
Point being: What if your resources in your Azure tenant (or even your Azure tenant itself) are vulnerable for a cyber-attack…wouldn’t you like to know about it BEFORE being impacted by a compromise? I know I certainly would. And being one who’s witnessed first-hand some bad stuff customers have faced in the past…trust me, you’ll want to take all the precautionary measures you can.
Always follow the “assume breach” mentality and think to yourself “How do I detect bad actors and respond quickly to help keep from hurting us?” One thing to do is start to protect your Azure investments by taking care of any potential vulnerabilities.
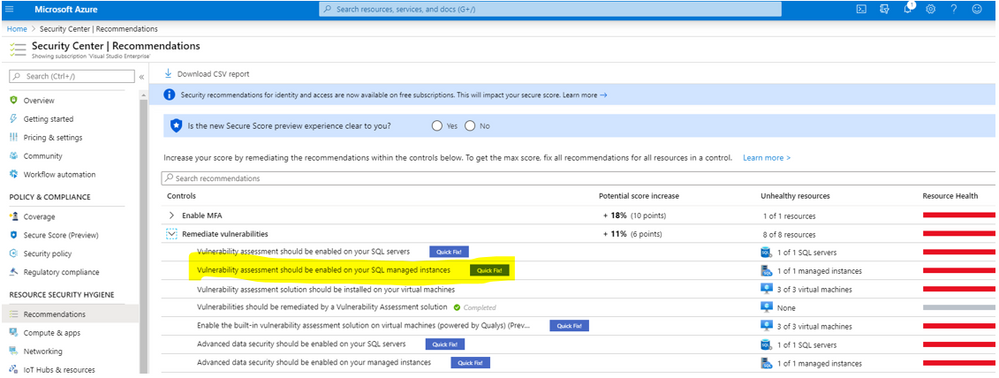
As you learned in this blog post (blog series), recommendations are grouped in Security Controls. The Remediate Vulnerabilities security control has the aggregation of multiple capabilities related to vulnerability assessment and remediation checks! When all is done you can elevate your Secure Score up by whopping 6 full points! I know it doesn’t sound like a lot, but with the new version of Secure Score it’s quite a positive impact. It’s a decent overall percentage increase if done completely and correctly. For example, in my test tenant that equates to 11%!!
Note: For more information on Secure Score info, read this article here, and pay particular attention on how to ensure you’re getting the maximum points you can.
Without further delay (and in no particular order), here are some various items you might see ASC recommend you take action on:
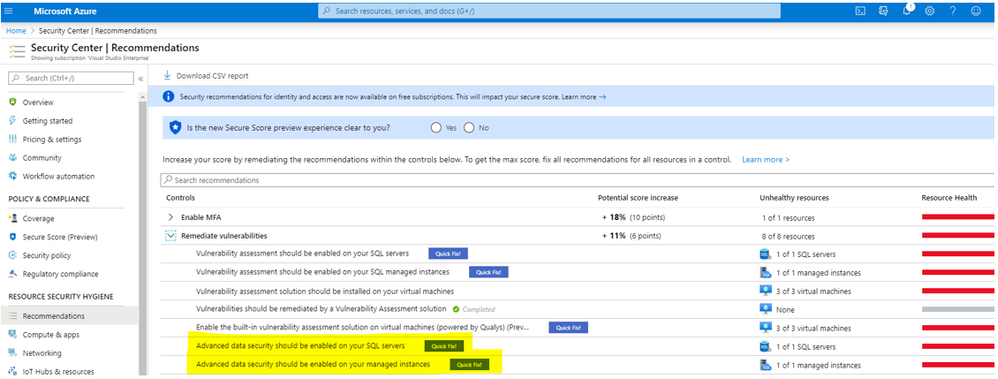
- Advanced Data Security should be enabled on your SQL servers (there’s also one for SQL instances)
- Vulnerabilities in Azure Container Registry images should be remediated
- Vulnerabilities on your SQL databases should be remediated
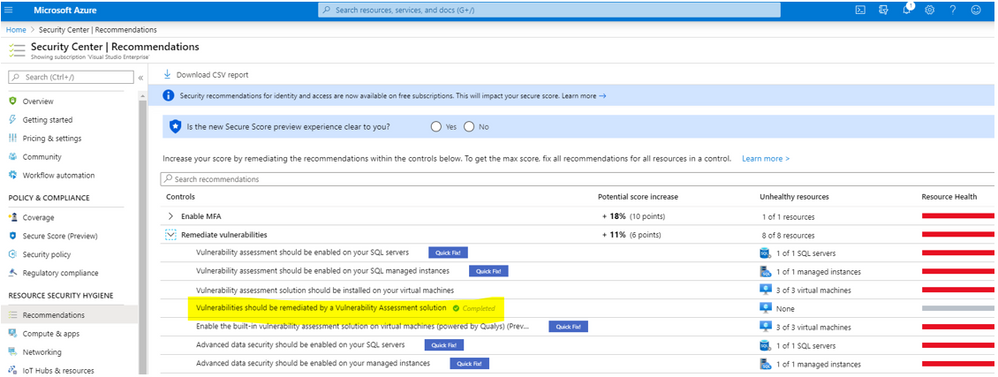
- Vulnerabilities should be remediated by a Vulnerability Assessment solution
- Vulnerability assessment should be enabled on your SQL managed instances
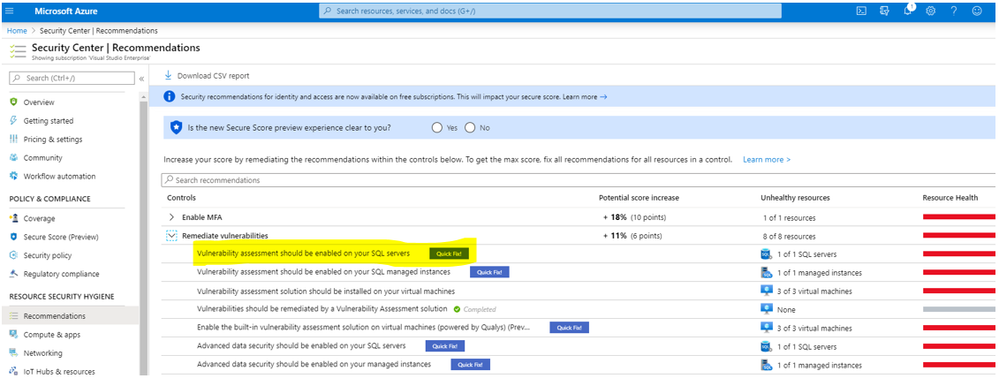
- Vulnerability assessment should be enabled on your SQL servers
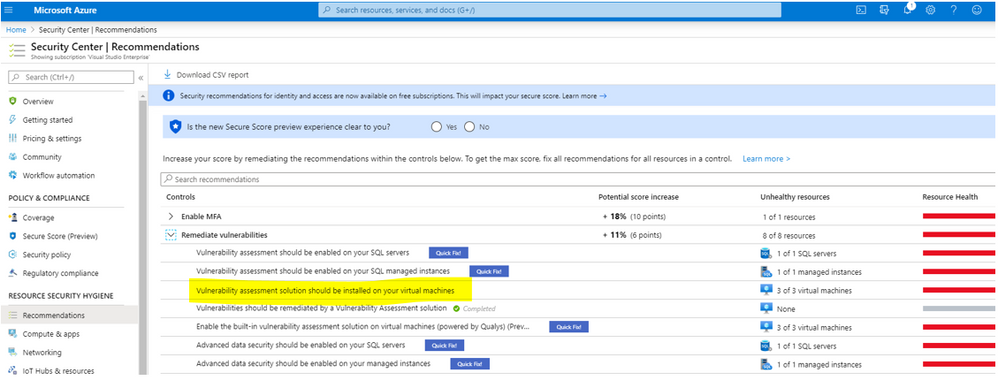
- Vulnerability assessment solution should be installed on your virtual machines
Also, some might have a “Quick Fix!” button as well! No excuses not to enable those, just click the button and you’re done. (Note: screenshots below are from my test tenant, and may vary a bit from yours)
Recommendation: Vulnerability assessment solution should be installed on your virtual machines
Let’s get started with the “Vulnerability assessment solution should be installed on your virtual machines.”
I’d like to begin with this one, as I’ve already written another article on how to enable a partner scanning tool on your tenant found here. Ergo, I’m not going to go into significant detail as you can read up on it further from my previous article. (Shameless plug I know.) But I will emphasize that this one is crucial to your tenant’s security footprint.
In a nutshell, this recommendation gives you the ability to install a 3rd party partner vulnerability scanning tool consisting of either Qualys or Rapid7. It does require you to have a license from the one you choose, so keep that in mind. This will also appear for “free” tenants as well as standard.
This recommendation appears for both standard and free tiers. Use this recommendation to install any of the supported partner solutions. You'll need to purchase a license for your chosen solution separately. Supported solutions report vulnerability data to the partner's management platform. In turn, that platform provides vulnerability and health monitoring data back to Security Center. You can identify vulnerable VMs on the Security Center dashboard. Switch to the partner management console directly from Security Center for additional reports and information. (source: this article)
As a side note, those of you with Azure tenants in the standard tier will also be able to receive the Enable the built-in vulnerability assessment solution on virtual machines (powered by Qualys) recommendation. Again, it only appears in standard tiers. It's an invitation to install an Azure Security Center Vulnerability Assessment extension (powered by Qualys) for you at no additional cost. This extension reports its findings directly back to Security Center and fully integrated so there’s no need to purchase additional 3rd party licenses. (source: this article)
Recommendation: Vulnerabilities should be remediated by a Vulnerability Assessment solution
Next, let’s discuss “Vulnerabilities should be remediated by a Vulnerability Assessment solution.”
You might be thinking, “well duh!” And I would agree with you! Once you deploy a 3rd party vulnerability assessment solution to your VMs in Azure, then they are continually monitored by referenced solution. Let’s take the 3rd party Qualys agent for example (not the integrated one with standard tier, and only if you have a proper license). Whenever such vulnerabilities are found by the 3rd party agent, these are available for more information as part of the recommendation. So of course, you’ll want to act and remediate anything that is found!
Or you know, don’t act on the suggestions…and maybe you’ll get lucky. Or maybe you’ll wind up in the news… Do you want to take that chance?
Depending on what’s discovered will naturally impact your game plan for remediation. I will say this though, as someone who’s been around cyber-attacks and their aftermath, please do me a favor and implement the suggested actions if any are found as fast as possible. You’ll thank me later!
As a side note, the integrated version (built-in Qualys offering) available in standard tiering will add additional ones that say “Powered by Qualys”, but not necessarily the verbiage you’ll get with a 3rd party agent.
Recommendation: Vulnerabilities in Azure Container Registry images should be remediated
Onward to “Vulnerabilities in Azure Container Registry images should be remediated.”
This one is for all customers leveraging containers up in Azure. We know all our customers haven’t made the “container” transition yet, but you all should at least know about them and also when to remediate any potential vulnerabilities.
One of the techniques you can use to secure containers is helping to protect the registry all your container images are stored in. If you're on Security Center's standard pricing tier, you can scan your ARM-based Azure Container Registry every time a new image is pushed. https://docs.microsoft.com/en-us/azure/security-center/azure-container-registry-integration
The scanner (Powered by Qualys) presents findings as Security Center recommendations that you can then take action on. As an example, you might see things related to .Net, or even Linux-based vulnerabilities discovered.
As an added bonus, here’s a link to additional hardening you can use to help secure your container environment.
Next up, here’s where we get into some recommendations involving SQL. Almost every customer I’ve had the pleasure of working with has SQL in their environment in some form or fashion. That said, I’m fairly certain these next recommendations from ASC will also apply to you and your environment.
Recommendation: Advanced data security should be enabled on your SQL servers
Let’s target the “Advanced data security should be enabled on your SQL servers” recommendation. (“Quick Fix!” available); This also includes “Advanced data security should be enabled on your managed instances” – for those who are running an instance vs. a server.
This is one I’d like to start with regarding SQL. It’s basically a pre-requisite in order to take advantage of the next recommendations coming up in this post. “ADS for SQL servers” is a unified package for advanced SQL security capabilities. This feature includes functionality for identifying and mitigating potential database vulnerabilities and detecting anomalous activities that could indicate threats to your database(s).
These advanced security features have evolved and benefited from continuous improvement over the past few years, and have already been running on more than 1 million databases in the corresponding Azure SQL Database service – Advanced data security for Azure SQL databases.
It includes some awesomeness like the ability to run a vulnerability assessment directly against your SQL server or instance, and even Advanced Threat Protection (ATP) which detects anomalous activities indicating unusual and potentially harmful attempts to access or exploit your SQL server. It continuously monitors your database for suspicious activities and provides action-oriented security alerts on anomalous database access patterns. These alerts provide the suspicious activity details and recommended actions to investigate and mitigate the threat.
Do yourself a BIG favor and enable ADS on all your SQL servers. No really…go do it.
See more info and how to implement – Link
Note:
- ADS is charged at $15 per SQL server or instance per month.
Recommendation: Vulnerability assessment should be enabled on your SQL servers
The “Vulnerability assessment should be enabled on your SQL servers” recommendation is one that everyone should do if they run SQL server in Azure. (“Quick Fix!” available).
This is basically a database scanning service that can discover, track, and help you remediate potential database vulnerabilities. It will detect vulnerabilities across all connected SQL Servers will appear in one unified dashboard. It provides visibility into your security state. And it includes the steps to resolve security issues and enhance your database fortifications.
Going through the motions and enabling it will turn it on for selected servers and databases.
It can help you:
- Meet compliance requirements that require database scan reports.
- Meet data privacy standards.
- Monitor a dynamic database environment where changes are difficult to track.
The rules used are based on Microsoft's best practices and focus on the security issues that present the biggest risks to your database and its valuable data. They cover database-level issues and server-level security issues, like server firewall settings and server-level permissions. These rules also represent many of the requirements from various regulatory bodies to meet their compliance standards.
Results of the scan include actionable steps to resolve each issue and provide customized remediation scripts where applicable. You can customize an assessment report for your environment by setting an acceptable baseline for:
- Permission configurations.
- Feature configurations.
- Database settings.
Things to note:
- SQL Vulnerability Assessment is part of the SQL Advanced Data Security (ADS) package. If ADS isn't enabled already, it will automatically be enabled on the SQL server you selected.
- For each region and resource group of the selected SQL servers, a storage account for storing scan results will be created and shared by all the instances in that region.
See more info and how to implement – Link
Recommendation: Vulnerability assessment should be enabled on your SQL managed instances
Like the one above, “Vulnerability assessment should be enabled on your SQL managed instances” pertains specifically to SQL instances running in Azure (SQL-as-a-Service), not necessarily SQL servers. (“Quick Fix!” available)
It includes all the same functionality as the previous recommendation, so I don’t need to re-iterate the exact same information. Just remember that ADS will be enabled automatically, and there’s a $15 charge per instance.
Same as above recommendation – Link
Recommendation: Vulnerabilities on your SQL databases should be remediated
“Vulnerabilities on your SQL databases should be remediated” - Another “Well duh!” recommendation don’t you think? Seriously though, it makes no sense to go discover potential problems and not take the steps to remediate. Make it a priority and get it done as quickly and as efficiently as possible.
Each one discovered should be listed out, and suggestions made on how to remediate. Of course, you should evaluate them first unless you’re certain it won’t break any applications. But implement the fixes ASAP.
Next Steps
To wrap up this blog post, I’d like you all to keep in mind this is just a small fraction of what ASC and the Secure Score can offer our customers to drive their security posture through the roof. We’re just getting started and this basically translates into some robust steps you can leverage to increase your own comfort level in protecting your environments / assets.
I, Tim Beasley, hope you enjoyed this article and learned something that will assist you in the continued fight of cyber-security. Please continue to enjoy our ASC Secure Score blog series and I look forward virtually seeing you all in the next one. Until then…
GET STARTED ON REMEDIATING YOUR VULNERABILITIES IN AZURE! ![]()
- The main blog post to this series (found here)
- The DOCs article about Secure Score (this one)
Reviewer:
Yuri Diogenes, Senior PM CxE ASC Team
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.