- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- Resource exemption in Microsoft Defender for Cloud
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Edited on 1/26/2021 to reflect the latest changes within the resource exemption capability of Microsoft Defender for Cloud.
Resource exemption will allow increased granularity for you to fine-tune recommendations by providing the ability to exempt certain resources from evaluation. With Microsoft Defender for Cloud’s Cloud Security Posture Management (CSPM) capabilities, we are offering a broad set of recommendations and security controls, that might be relevant for most, but not all customers. In the past, the only way to remove recommendations from the Defender for Cloud dashboard and prevent them from influencing your Secure Score was to disable the whole related policy in the Microsoft Defender for Cloud Policy Initiative. That way, all resources were affected, meaning that once you switched off a policy, the particular recommendation that was derived from it, was never shown again for any resource. Now, with the new resource exemption capability, you can select which resource or scope should no longer be evaluated against a particular recommendation, whereas others still are. It allows you to exempt resources in case they are already healthy because the recommendation's intent was resolved by other means that Defender for Cloud does not identify, or because you’ve decided to accept the risk of not mitigating a particular recommendation for a resource. Maybe, you have research and development environments for which you want to apply a not-so-strict baseline, whereas the rest of resources in the same subscriptions need to be fully protected. These are great examples for exempting these resources from evaluation with waiver as justification, whereas your production environments are still protected. Maybe you have a mix of Vulnerability Assessment solutions in your environment, some of which are not tracked by Defender for Cloud. In this scenario, the respective recommendation has already been remediated, and you can now create an exemption for these resources and select mitigated as justification.

Our goal is to reduce alert-fatigue so that security analysts can focus on the highest priority recommendations. As a result, your secure score will not be impacted by exempted resources.
How does it work?
The process for exempting a resource from a recommendation is straightforward and explained in our official documentation. Basically, when working with a recommendation, you just have to click the Exempt button on top of the recommendation's blade.

From a technical perspective, when you create a resource exemption, the status of the particular assessment (the evaluation of a particular resource against a given recommendation) is changed. The properties of the assessment will contain the status code “NotApplicable”, the cause “Exempt” and a description, as shown in the screenshot below.
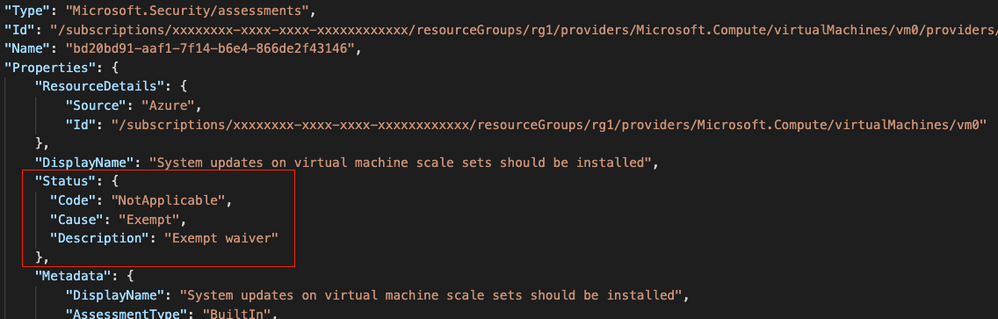
At the same time, creating a resource exemption in Defender for Cloud will create an Azure Policy exemption, a new capability the resource exemption feature relies on. With that being said, there are several ways to programmatically work with resource exemptions.
Resource exemption and automation
Knowing that an assessment is changed, and a new policy exemption is created every time you create a resource exemption in Defender for Cloud, you have several ways of programmatically interacting with the resource exemption feature.
Azure Resource Graph
Assessments in Defender for Cloud are continuously exported to Azure Resource Graph, giving you a great starting point for automation. ARG is a database that keeps a set of information which is gathered from different resources, giving you a very fast option to query information instead of separately pulling it from our REST APIs. Eli Koreh showed in his article how easy it is to create custom dashboards for Defender for Cloud powered by ARG. You can find a list of starter query samples for Azure Resource Graph in the documentation.
To give you an idea of how to work with resource exemption in an ARG query, I’ve created the following sample, that will return a list of all resource exemptions that have been created in your environment:
SecurityResources
| where type == 'microsoft.security/assessments' and properties.status.cause == 'Exempt'
| extend assessmentKey = name, resourceId = tolower(trim(' ',tostring(properties.resourceDetails.Id))), healthStatus = properties.status.code, cause = properties.status.cause, reason = properties.status.description, displayName = properties.displayName
| project assessmentKey, id, name, displayName, resourceId, healthStatus, cause, reason
You can tune that query according to your needs, but it’s great as is for a quick overview on all exemptions you have created in your environment.
Resource Exemption and REST API
When a resource exemption in Defender for Cloud is created, an exemption in the Azure Security Benchmark assignment is created. This is why you can leverage the Microsoft.Authorization/policyExemptions API to query for existing exemptions. This API is available as of version 2020-07-01-preview.
A GET call against the REST URI https://management.azure.com/subscriptions/<your sub ID>/providers/Microsoft.Authorization/policyExemptions?api-version=2020-07-01-preview will return all exemptions that have been created for a particular subscription, similar to the output shown below:
{
"value": [
{
"properties": {
"policyAssignmentId": "/subscriptions/<yourSubID>/providers/Microsoft.Authorization/policyAssignments/SecurityCenterBuiltIn",
"policyDefinitionReferenceIds": [
"diskEncryptionMonitoring"
],
"exemptionCategory": "waiver",
"displayName": "ASC-vmName-diskEncryptionMonitoring-BuiltIn",
"description": "demo justification",
"expiresOn": "2020-09-22T22:00:00Z"
},
"systemData": {
"createdBy": "someone@company.com",
"createdByType": "User",
"createdAt": "2020-09-22T09:27:23.7962656Z",
"lastModifiedBy": "someone@company.com",
"lastModifiedByType": "User",
"lastModifiedAt": "2020-09-22T09:27:23.7962656Z"
},
"id": "/subscriptions/<yourSubID>/resourceGroups/<yourRG>/providers/Microsoft.Compute/virtualMachines/<vmName>/providers/Microsoft.Authorization/policyExemptions/ASC-vmName-diskEncryptionMonitoring-BuiltIn",
"type": "Microsoft.Authorization/policyExemptions",
"name": "ASC-vmName-diskEncryptionMonitoring-BuiltIn"
}
]
}
You can find further information about Policy Exemptions in the Azure Policy documentation.
(Workflow) automation with Logic Apps
Microsoft Defender for Cloud's workflow automation feature is great for both, automatically reacting on alerts and recommendations, as well as manually triggering an automation in case you need it. I have created a sample playbook to request a resource exemption, that I want to explain a bit further below:
Request a resource exemption
In order to be able to create a resource exemption in Defender for Cloud, your user account needs to be granted elevated access rights, such as Security Admin. In enterprise environments that we are working with, we often see that Azure subscriptions are given to people who are responsible for their own set of resources, but security is still owned by a central team. In this scenario, you don’t want to necessarily give every resource owner the right to create a resource exemption, but still, for justified reasons, someone should be allowed to request an exemption. To make this process easier and to fit it into your approval process, I’ve created a Logic App that can manually be triggered from the recommendation blade and allows you to request an exemption. Once a resource owner is checking recommendations and wants to exempt a resource, they can do it by clicking the Trigger Logic App button. The screenshot below shows the easy process:
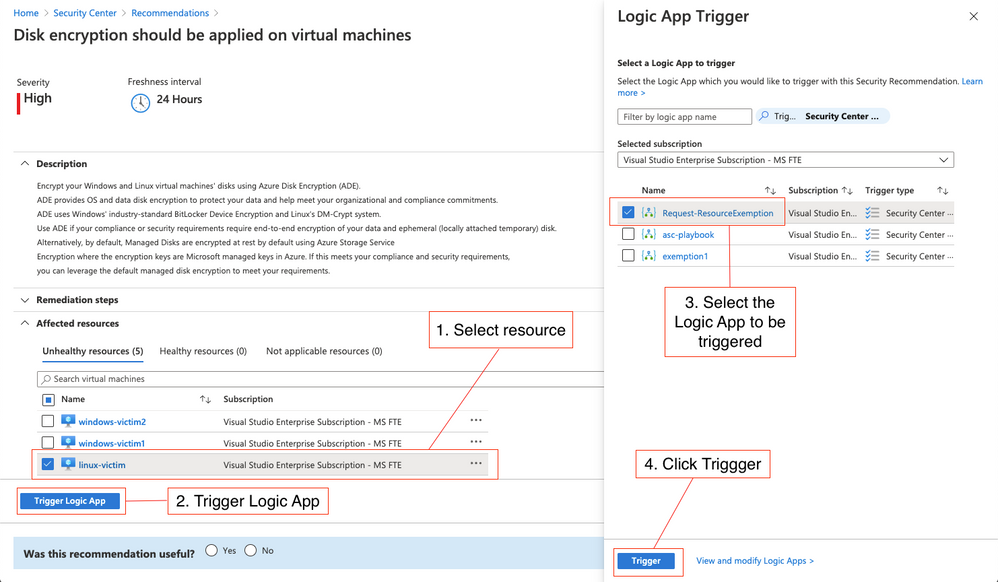
- Select one or several resources to be exempted from the recommendation you are currently investigating.
- Click the Trigger Logic App button
- Select the Request-ResourceExemption Logic App (or whatever name you give it when deploying it)
- Click the Trigger button
The Logic App leverages the When a Microsoft Defender for Cloud recommendation is created or triggered trigger and will then send an email and a Teams message to the subscription’s security contact(s). This email and message will contain information about the resource, the recommendation, and a link that, once clicked, will lead you directly to a portal view that enables you to immediately create the requested resource exemption. You can find this playbook in our Defender for Cloud GitHub repository, from where you can one-click deploy it to your environment.

You can also use this sample playbook as a starting point for customizations according to your needs. For example, if you want to create a ServiceNow or JIRA ticket with that workflow, you can simply add a new parallel branch with the Create a new JIRA issue or the Create ServiceNow Record actions:

Next Steps
Resource Exemption in Defender for Cloud now give you a way to exempt resources from a recommendation in case it has already been remediated by a process not monitored by Defender for Cloud, or in case your organization has decided to accept the risk related to that recommendation. You can easily build your own automations around that feature or leverage the sample artifact we have published in the Defender for Cloud GitHub community. You can also publish your own automation templates in the community, so others can benefits from your efforts, as well. We have started a GitHub Wiki so you can easily learn how to publish your automations.
Now, go try it out and let us know what you think! We have published a short survey so you can easily share your thoughts around this new capability and the automation artifact with us.
Special thanks to Miri Landau, Senior Program Manager for reviewing this article.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.