- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud
- New Blog Post | Azure Defender PoC Series – Azure Defender for SQL
New Blog Post | Azure Defender PoC Series – Azure Defender for SQL
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 19 2021 12:20 PM
Azure Defender PoC Series – Azure Defender for SQL - Microsoft Tech Community
This article is a continuation of Azure Defender PoC Series which provides you guidelines on how to perform a proof of concept for a specific Azure Defender plan. For a more holistic approach where you need to validate Azure Security Center and Azure Defender, please read How to Effectively Perform an Azure Security Center PoC article.
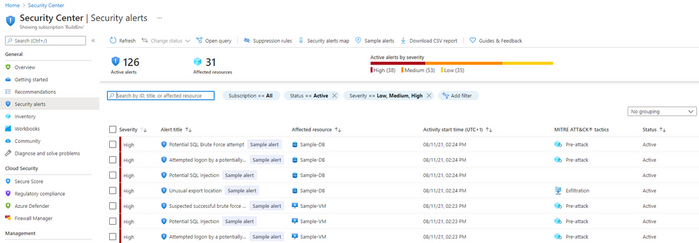
There can be many security vulnerabilities in databases that are sometimes taken advantage of by malicious actors. According to the Github 2020 report, a vulnerability typically goes undetected for 218 weeks (just over four years) before being disclosed and fixed. Injection attacks, such as those on SQL and NoSQL, are among the most popular types of cyberattacks for web applications (as per OWASP Top 10).
SQL Injection attacks, brute-force attacks, SQL shell OS attacks leading to crypto-mining and ransomware, can be detected and remediated by the Azure Defender for SQL plan.
Original Post: New Blog Post | Azure Defender PoC Series – Azure Defender for SQL - Microsoft Tech Community