- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- Identify Azure VMs which are not monitored by Security Center
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
And use an input file to onboard them to Security Center automatically
The link for the scripts used in this blog can be found at the end of the blog.
Looking to increase your Secure Score? Look here.
Security Center offers a couple of options to have your Virtual Machines (VMs) in Azure automatically protected. This provides great benefits by protecting your resources against threats and helps you get more secure in a fast and efficient way.
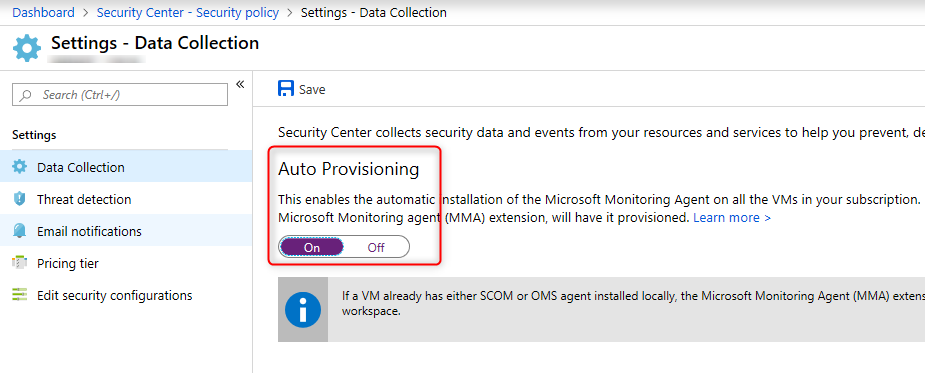
To safeguard your VMs, Security Center requires the installation of the Microsoft Monitoring Agent (MMA). The easiest way to have that automatically done for you, is to enable Auto Provisioning:
This installs the (MMA) automatically to all your VMs in your subscription.
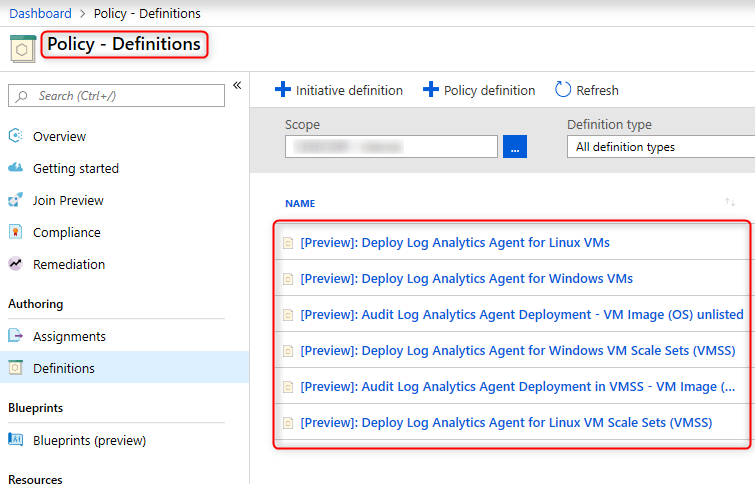
Another great option is to assign a built-in Azure Policy, which will also install the MMA upon creation of a VM and can also take care of remediations, in case someone has removed the MMA:
VMs which don’t have the MMA installed, are flagged by Azure Policy as non-compliant.
Are you not using the automatic MMA installation options?
There might be exceptions for which you don’t want the MMA automatically installed in your subscription. Although you can define a scope and exceptions in Azure Policy, it is not meant to change frequently, since you must update the Azure Policy assignment to reflect the change.
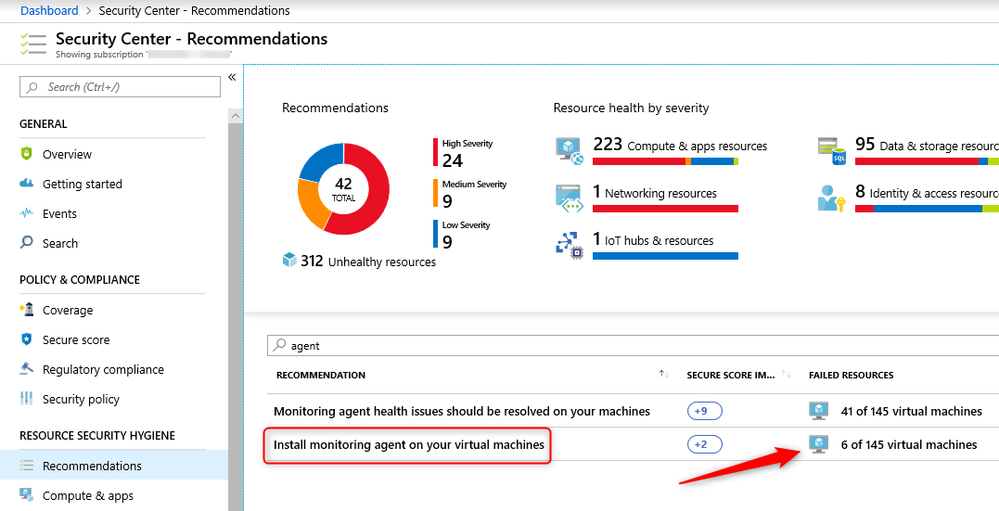
If for whatever reason you have chosen not to use automatic installations of the MMA, then you obviously have a concern if your resources are properly protected (and you should!) The challenge is how to get insights into the VMs that are not protected. Security Center offers your recommendations and one of those is to install the MMA:
Clicking on the recommendation reveals which VMs are not protected.
Using PowerShell to retrieve a list of all unprotected VMs
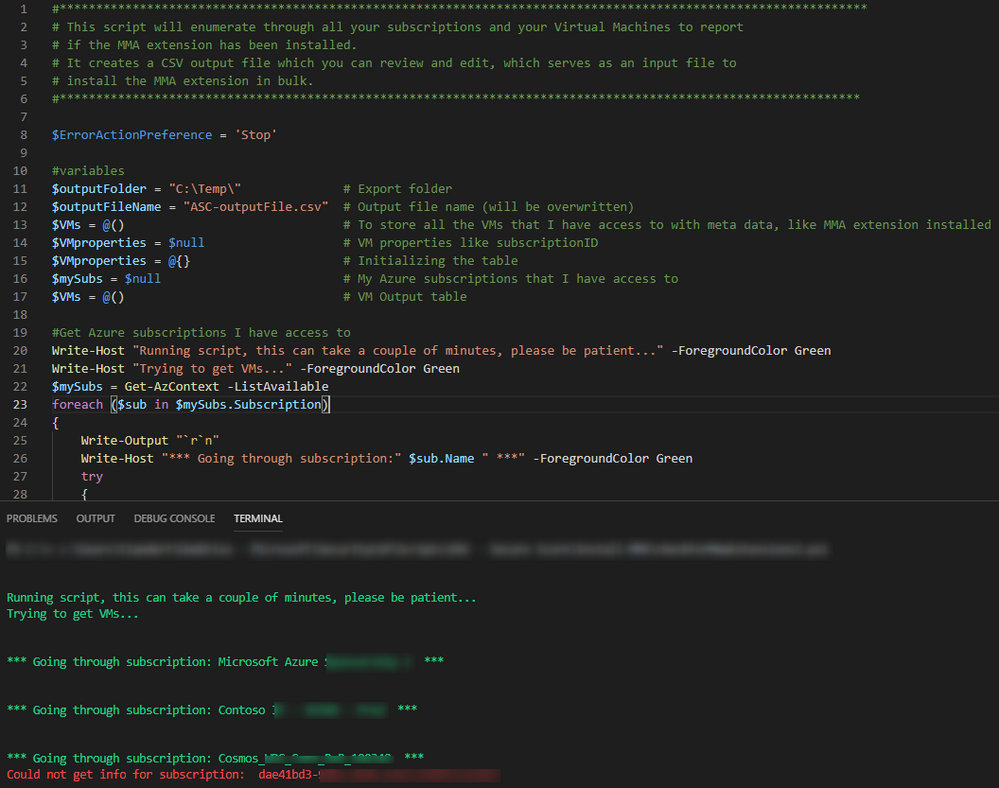
Another option to get insights into which VMs are not protected by Security Center, is to use PowerShell.
This offers a great way to enable automation for not only creating such a list, but also to bulk install the MMA on VMs that you identify.
First, let’s get a list of VMs which are not protected by Security Center:
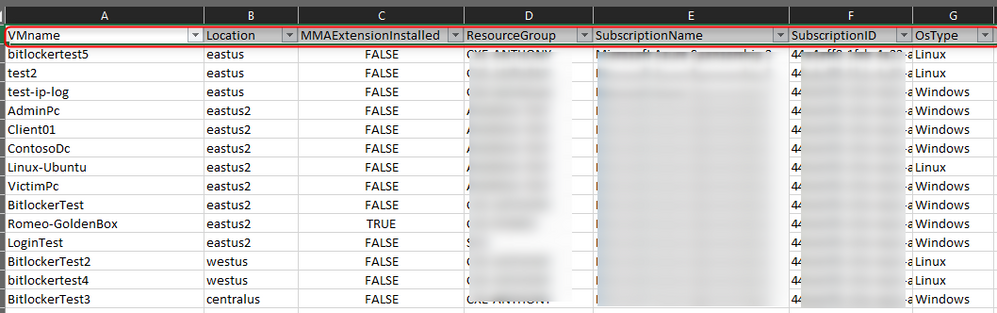
Automatically install the MMA VM Extension based on an input file
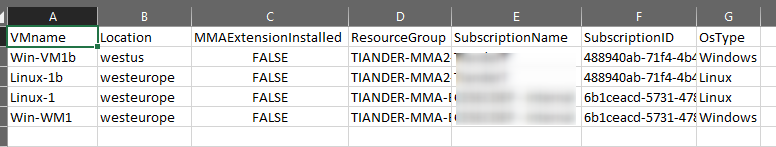
Now that you have insights into which VMs are not protected by Security Center, you can create an input file which only contains the VMs that you want the MMA to be installed on. Keep the headers as they are and just copy your filtered view in a new CSV file, like this:
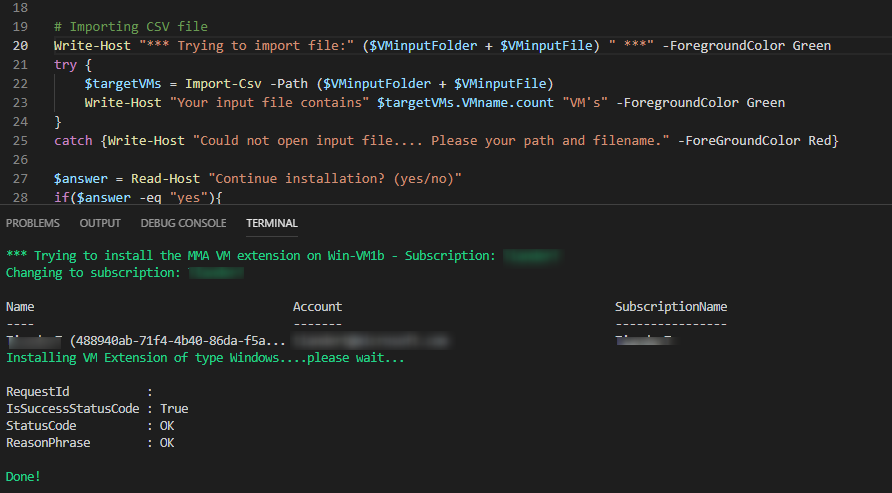
Now run the second script which will take your input CSV file:
The sample scripts used in this blog can be found here:
Looking to increase your Secure Score? Look here.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.