- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- How to respond to potential Malware uploaded to Azure Storage Blob
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
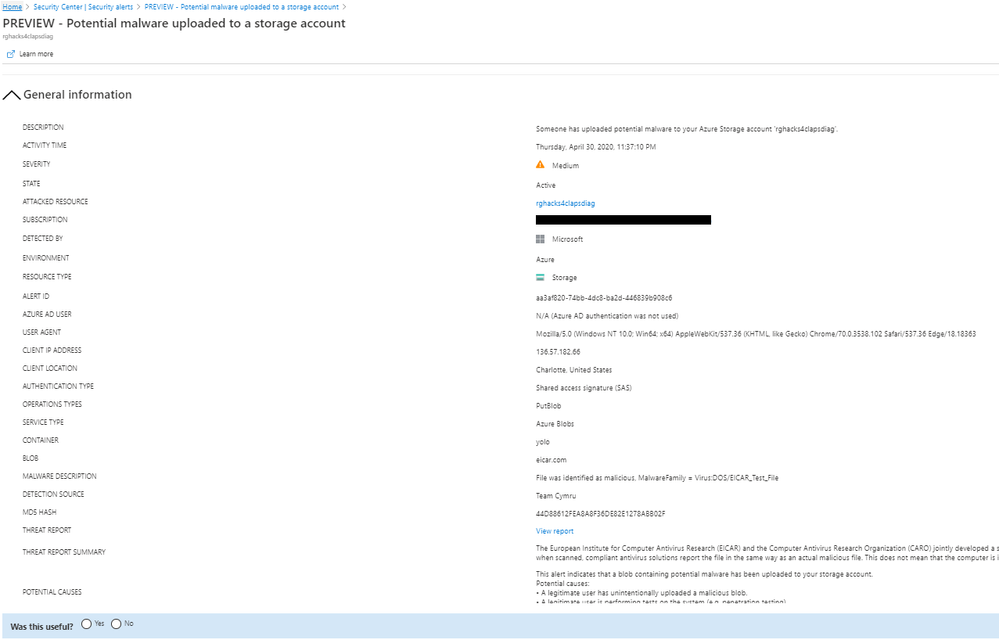
Microsoft Defender for Cloud covers a wide capability on Cloud Workload Platform Protection (CWPP) when it comes protecting Platform as a Service. One of those capabilities is alerting to potential malware uploaded as a Blob to an Azure Storage Account.
The potential malware upload alerting works as follows. When Microsoft Defender for Cloud is protecting Azure Storage, blob files uploaded to Azure Storage produce telemetry streaming logs. In many cases the stream operation logs contain hashes related to the blob. These hashes are compared using Microsoft's Threat Intelligence to do hash reputation analysis looking for viruses, trojans, spyware and ransomware. When a match is found an alert is raised in Microsoft Defender for Cloud.
This alerting can help detect intentional activity by an attacker looking to leverage storage for lateral movement or unintentional upload of a malware file from a cloud user or application.
Alerting on the potential malware uploaded is very helpful, but you can take it one step further by leveraging Workflow Automation feature to trigger a series of actions upon receiving this alert, including sending an email and notify your security team when a potential malware is uploaded to your storage account. After your security investigation a decision can be made as the email that notified your team also contains a link to approve or reject the deletion of the potential malware blob in the alert.
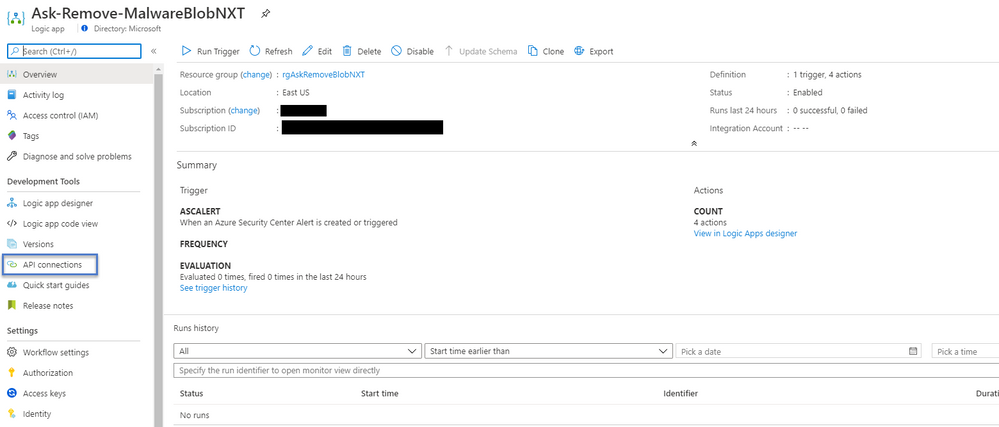
To deploy the Security Logic App, you can leverage our Microsoft Defender for Cloud Community GitHub Repository, specifically this one
Be sure to set the Logic App’s Managed Service Identity on a Management Group or Subscription with the Storage Blob Data Contributor and Security Admin role assignment. In addition setup Workflow automation documented here to trigger on alerts that contain ‘’ Potential malware uploaded to a storage account”
Once the Logic App and Workflow Automation are setup you can test the Logic App and Workflow Automation by using the following documented testing trigger scenario.
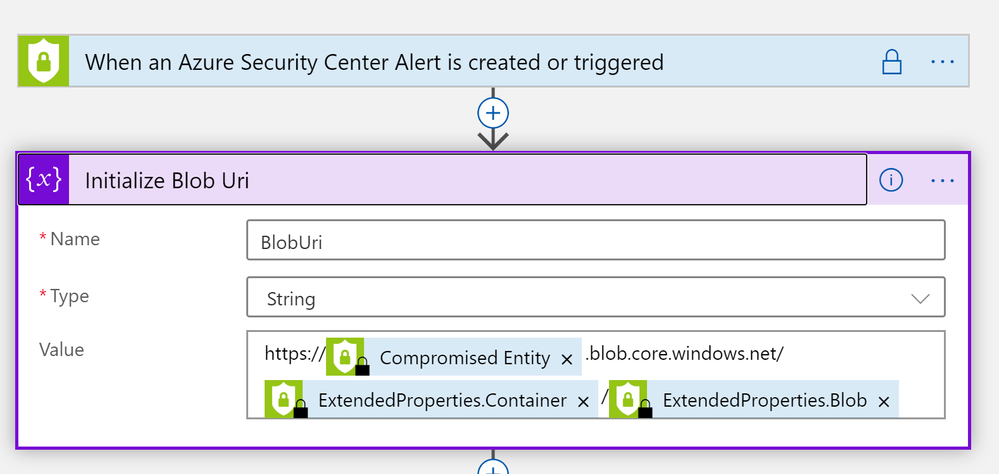
The Logic App upon detection starts by taking the unique properties of the alert and crafting the Blob Uri as a variable.
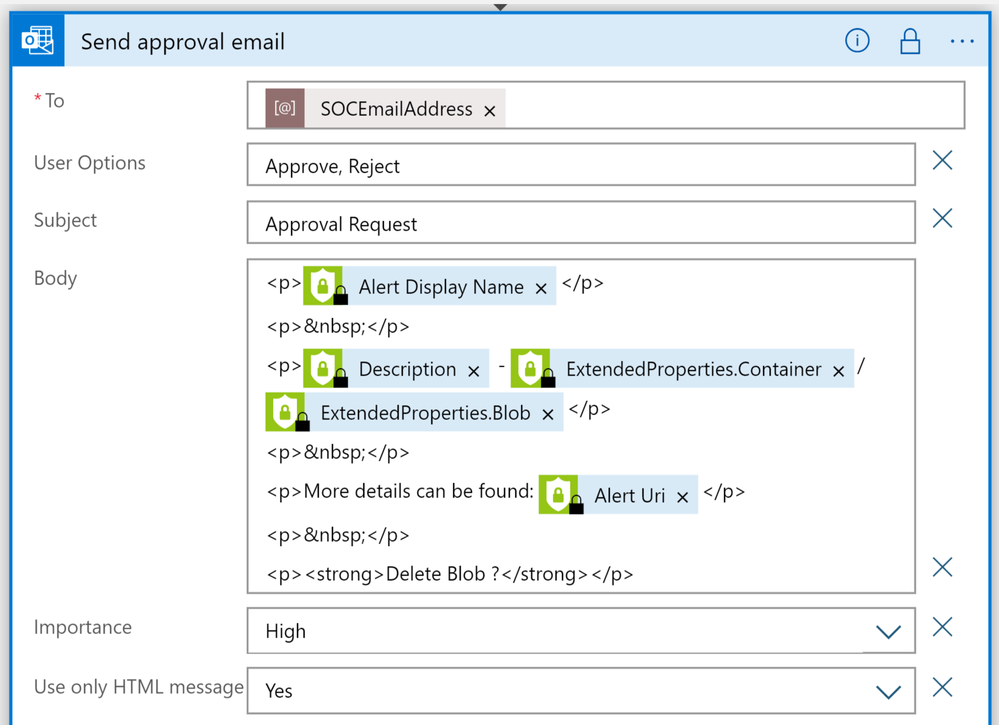
It will then send a email notification of the alert to the designated security team.
Within the email a security analyst can click on the Microsoft Defender for Cloud link to investigate the potential malware blob further. Once analysis is finished the security analyst can approve or reject deletion of the blob on Azure Storage account even though they may not have access to it. This is because the Logic App will execute using it’s Storage Blob Data Contributor role assignment and specific to that blob only.
Once Approved
The Logic App makes a Storage Data layer API call to DELETE the blob uri you captured in the variable above
It works best to Enable Storage Soft Delete on all Storage Accounts as well in the advent a blob was deleted but needs to be restored.
The Logic App will then send a confirmation email ensuring confirmation of successful deletion of the Blob
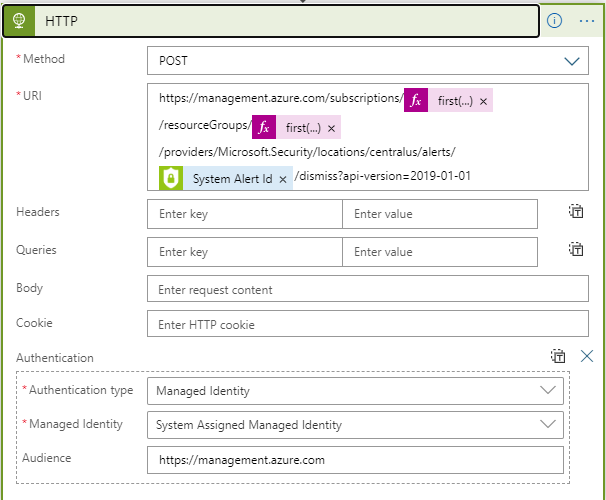
As a final step the Logic App will dismiss the Azure Security Alert using it’s Security Admin role assignment since remediation has taken place.
The URI path is also informed by using Logic App expressions to split on the AzureResourceID of the affected storage account. It can now properly pass the Subscription ID and Resource Group name when dismissing this security alert in Microsoft Defender for Cloud.
Here is an example of the expression that will take the AzureResourceID and split on '/' values in the string and starting first at the beginning choosing the 2nd position of that split.
Finally you will need to take some post installations steps with the Logic App and Microsoft Defender for Cloud Workflow Automation to ensure this will execute properly after deployment.
You will need to first go to the Logic App and go to a specific blade called API connection send below to Authorize and Save your Office 365 API Connection. This ensures the Logic App can send an email on behalf of the mailbox.
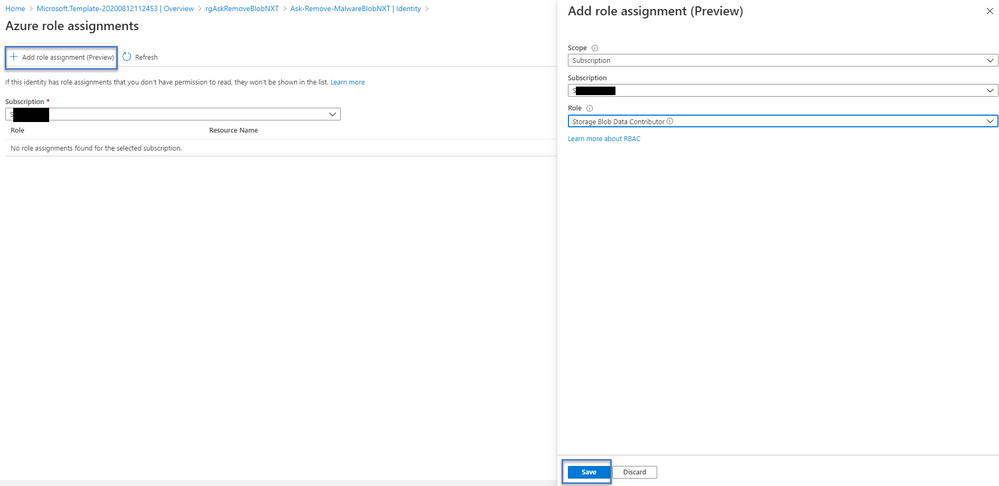
As another step you need to assign the Logic App which will deploy as a Managed Service Identity access to your subscription or Management Group with Role Assignments. This allows the Logic App to execute it's steps with proper authorization against storage account and Microsoft Defender for Cloud.
Please assign Storage Blob Data Contributor and Security Admin roles
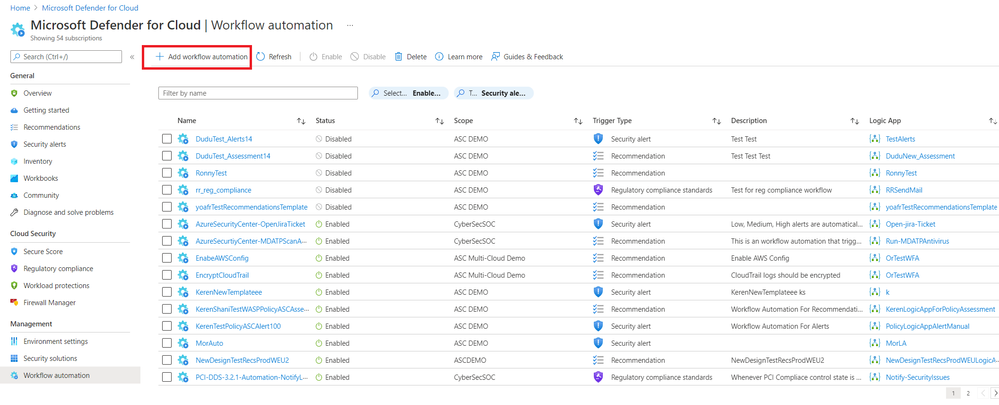
The final step will be to go to Microsoft Defender for Cloud and Workflow Automation blade and wire up so that when a specific alert comes in it will trigger this deployed Logic App.
Please pay attention to the field Alert name contains
You need to ensure this will trigger on a specific alert called:
Potential malware uploaded to a storage blob container
Once saved you now have the alert firing the logic app.
In this post you learned how the potential malware blob detection works by analyzing the streaming telemetry logs and comparing file hashes when present to Microsoft Threat Intelligence. You also learned how to leverage Workflow Automation to notify your security team and automate based on a decision to delete the potential malware blob.
Special thanks to:
@YuriDiogenes for reviewing this post
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.