- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- How to demonstrate the new containers features in Azure Security Center
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
At Ignite Azure Security Center team announced many new features and capabilities in the CSPM and the CWPP segments. The entire list can be found in this blog post.
One out of many areas that the product team invested a lot of resources and innovation is the containers workload and specifically AKS (Azure Kubernetes Service).
The new capabilities in this public preview release include:
- Discovery & Visibility - Continuous discovery of managed AKS instances within Security Center’s registered subscriptions.
- Secure Score recommendations - Actionable items to help customers comply to security best practices in AKS as part of the customer’s Secure Score, such as "Role-Based Access Control should be used to restrict access to a Kubernetes Service Cluster".
- Threat Detection - Host and cluster-based analytics, such as “A privileged container detected”.
- Scan container images in Azure Container Registry (ACR) for vulnerabilities.
You can learn more about these capabilities reading the following articles:
- Azure Kubernetes Services integration with Security Center (Preview)
- Azure Container Registry integration with Security Center (Preview)
On this blog post we will focus on how to simulate alerts that are part of the AKS threat Detection and the image scanning (ACR) recommendation.
Simulate AKS alert on Azure security center
To simulate AKS alert on a cluster that is protected under Azure Security center follow the following steps:
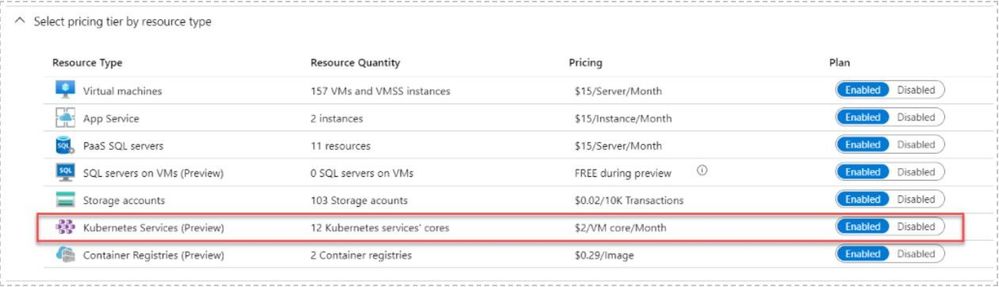
- Validate that your AKS threat protection pricing tier is enabled. If it is not, make sure to enabled it.
2. From Azure CLI logic to the AKS subscription by running the above commands:
az login
az account set --subscription "MyAzureSubName"
3. Download AKS tools for Azure CLI and add a local path:
az aks install-cli
$env:path += 'C:\Users\User\.azure-kubectl'
4. Run the alert simulation command below:
kubectl get pods -–namespace=asc-alerttest-662jfi039n
You may see an output similar to the one below:
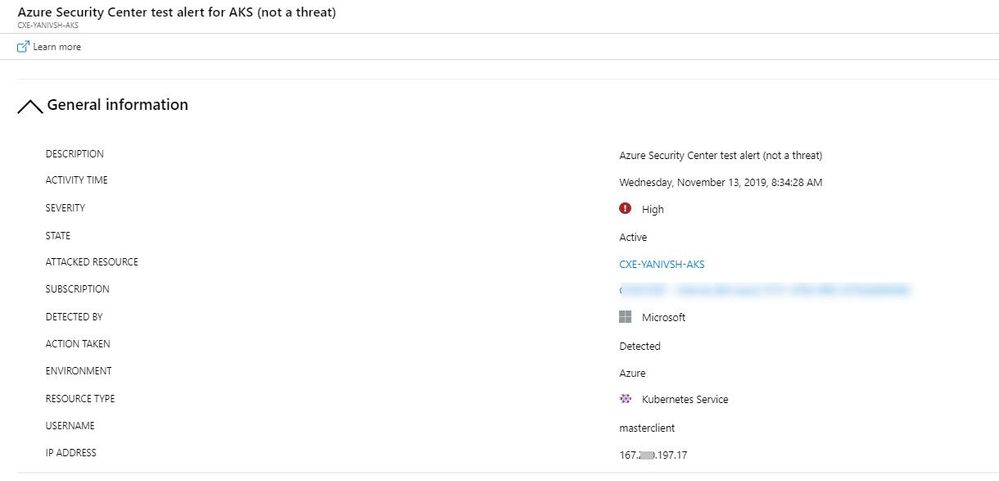
Wait approximately 40 minutes and open Azure security center alert blade:
Once you see it, click on it until you see the full details, as shown below:
Simulate a scanning for a vulnerable container image to an Azure Container Registry (ACR) and present its recommendation in Azure security Center.
One of the exciting features that introduced in Ignite was the ability to scan container image and share the vulnerability recommendation on Azure security center.
Key notes about this feature are:
- The underline scanning engine that we using is Qualys
- The scan action is only happening on push image activity.
To simulate this, the first step is to install Docker desktop desktop.
Follow the steps below to do that:
- Navigate to https://www.docker.com/products/docker-desktop
- Download and install Docker for Desktop
- As part of the installation you will need to enable Hyper-V on your local computer
- Open PowerShell
- Verify your docker version by executing in PowerShell:
docker version
Once you finish the installation, validate if you have the container registry pricing tier enabled on ASC, as shown below:
Next, you should create the Container Registry in Azure portal or via CLI.
Follow the steps below to do that and continue the validation:
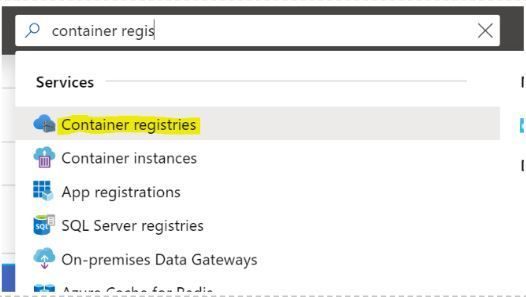
1. Select container registries and press new.
2. Enter a unique name, select, or create a new resource group and press create.
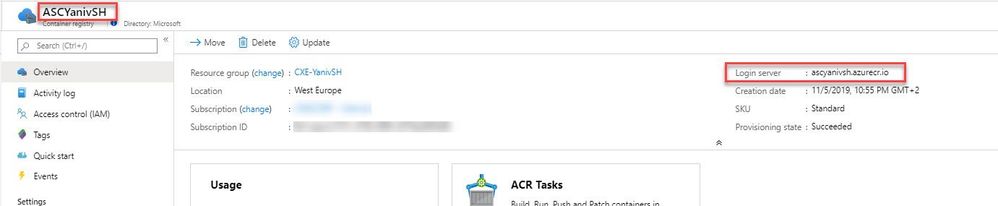
Once the ACR was created successfully, copy the Login server URL.
Open PowerShell and run (where the name is the ACR name that you created) the command below:
az acr login --name ASCYanivSH
4. Download vulnerable image from docker hub https://hub.docker.com/r/vulnerables/web-dvwa/,
By by running the command below:
docker pull vulnerables/web-dvwa
A sample of the output is shown below:
5. Check the image on your local repository by running the command below:
Docker image list
A sample of the output is shown below:
6. In this step we need to tag our image with the ACR Login URL that we copied in steps Execute the following command:
Docker tag vulnerables/web-dvwa:latest ascyanivsh.azurecr.io/vulnerables/web-dvwa:v5
A sample of the output is shown below:
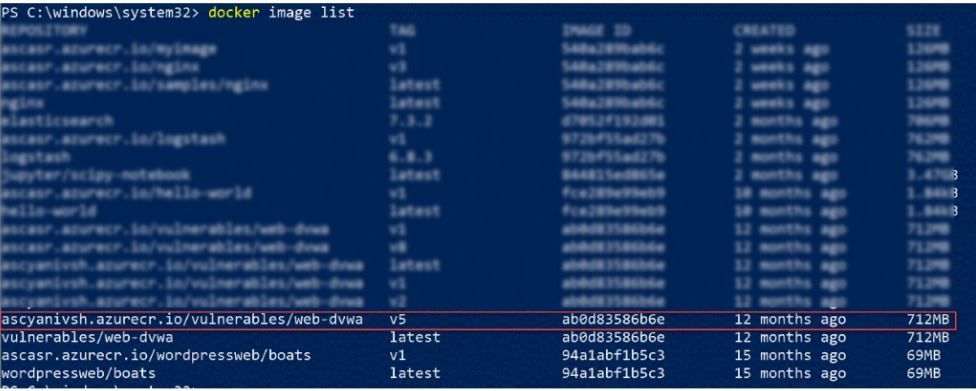
7. Run again the docker image list, and notify the new image with the new tag, as shown in the sample below:
8. Run docker push to upload the new image to the azure repository and generate the ASC image scan (it can take some time), using the command below:
Docker push ascyanivsh.azurecr.io/vulnerables/web-dvwa:v5
A sample of the output is shown below:
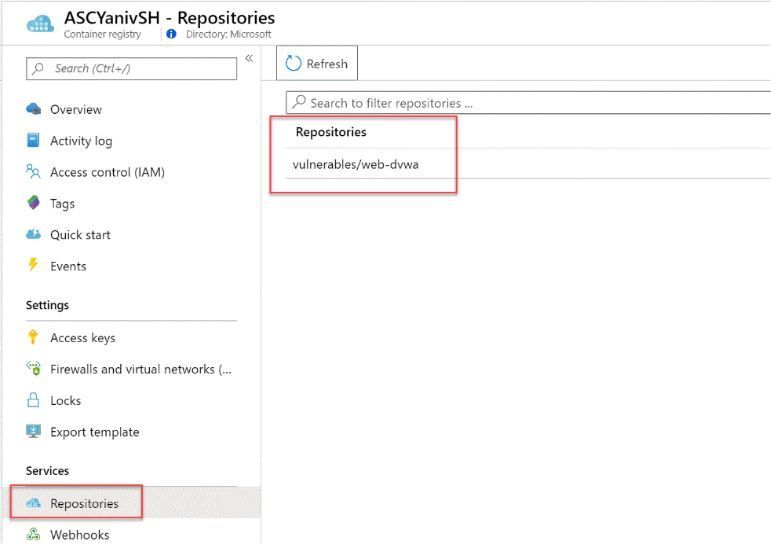
Once done check on your ACR repository and validate that you have a new repository with new image.
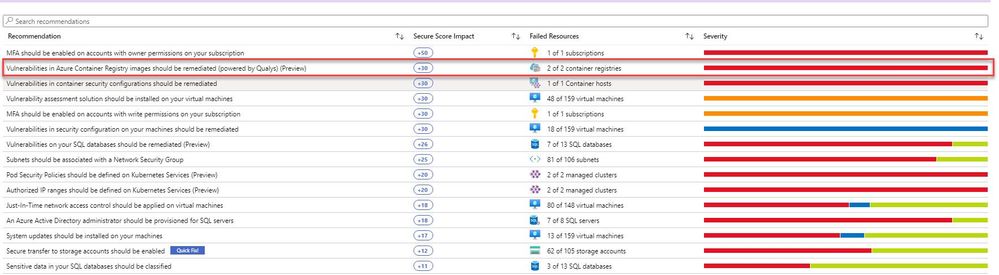
Open ASC and look for “Container registry images” recommendation.
“Vulnerabilities in Azure Container Registry images should be remediated (powered by Qualys)” recommendation.
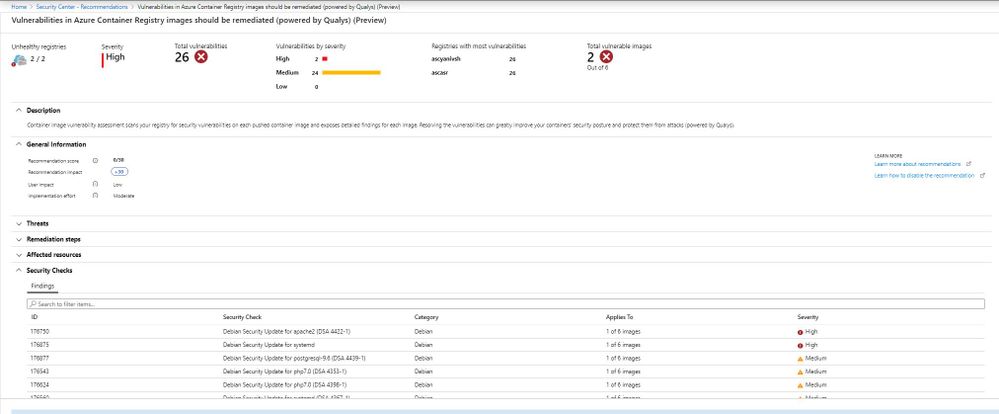
Drill down to the recommendation and review image and the set of vulnerabilities that Azure Security Center discovered.
In this blogpost, we provided details on the options to simulate
alerts that are part of the AKS threat Detection and the image scanning (ACR) recommendation.
For more information on how Azure Security Center provides co visit our documentation below:
Azure Security Center Documentation
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.