- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- Customizing Endpoint Protection Recommendation in Microsoft Defender for Cloud
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Microsoft Defender for Cloud assesses your environment and enables you to understand the status of your resources, to help you improve the Security Posture. The heart of the Defender for Cloud lies in its recommendations. Security recommendations help you to reduce the attack surface across your workloads. One important recommendation that Security Center has is to identify if your computers have an endpoint protection solution installed.
Microsoft Defender for Cloud monitors the status of antimalware protection and reports this under the ‘Enable Endpoint protection’ security control when it identifies the Antimalware solution is not installed or unhealthy. Security Center highlights issues, such as detected threats and insufficient protection, which can make your virtual machines vulnerable to antimalware threats. This is a very important recommendation because malware cannot only be downloaded or installed by threat actors, but also inadvertently by legitimate users who are supposed to access your machines.
Microsoft Defender for Cloud covers a variety of Antimalware vendors today. You can find the list of supported versions in this article. However, in a scenario where you’re using an antimalware protection that is not in the Microsoft Defender for Cloud supported list but you still want to have visibility over the status of this antimalware using Defender for Cloud dashboard, how would you tackle this scenario? In this blog, I would like to walk you through a Github artifact that will help you monitor any antimalware you may be using even if it is not in the Defender for Cloud supported list.
The Github artifact will deploy a Guest Configuration policy to monitor antimalware in your machines. For context, Azure Guest Configuration Policy can audit settings inside a machine, both for machines running in Azure and Arc Connected Machines, the validation is performed by the Guest Configuration extension and client. Before we deploy this artifact, let’s understand the resources that’s making it all possible.
Expected contents of this Custom Guest Configuration artifact
The completed package is used by Guest Configuration to create the Azure Policy definitions. The package consists of:
- Modules folder
- AzureGuestConfigurationPolicy module
- DscResources module
- (Windows) DSC resource modules required by the MOF
The DSC module in the artifact, is checking CIM Instance (Get-CimInstance) in the SecurityCenter namespace to check for any antivirus product installed in the Windows VM and the query returns the list of antimalware installed in the machine (an example is as shown in Image 1).

In my example here, the VM is running Windows Defender as well as Avast Antivirus. Microsoft Defender for Cloud can discover Windows Defender however, Avast Antivirus discovery is not supported.
The DSC is then trying to identify if there is a process running that executable on the VM, which evaluates the Antivirus is not just installed but it’s running and healthy in a given VM.
The DSC is using Get-Process that will find the process running in the machine (an example is as shown in Image 2). If there’s no instance of a process running the Antivirus executable found, the validation will stop and returns a status of Stopped providing you a clear description.

In summary, If the antimalware is not found in the CIMInstance list, then the DSC returns Absent. If it is found, but doesn’t identify the process running, it will return:
Ensure = “Present”
Status = “Stopped”
If the process is found, then:
Ensure = “Present”
Status = “Running”
For an overview of DSC concepts and terminology, see PowerShell DSC Overview.
Under AzureGuestConfigurationPolicy folder, you’ll find a module (AzureGuestPolicyHelper.psm1) that will help you create policy package, upload it directly to your Azure subscription and will configure everything for you. Let’s take a step back and review the resources in here.
When auditing Windows, Guest Configuration uses a Desired State Configuration (DSC) resource module to create the configuration file. The DSC configuration defines the condition that the machine should be in. If the evaluation of the configuration fails, the policy effect auditIfNotExists is triggered and the machine is considered non-compliant.
In our example, under the Configuration folder you’ll notice a bogus configuration which is needed for Azure Guest Configuration policy during execution. So here, the configuration that will be used for the policy. In our scenario, we want to monitor Antivirus making sure the antivirus is installed and the agent is running. Find the sample below for reference,
Configuration MonitorAntivirus
{
Import-DscResource -ModuleName EndPointProtectionDSC
Node MonitorAntivirus
{
EPAntivirusStatus AV
{
AntivirusName = "Windows Defender"
Status = "Running"
Ensure = "Present"
}
}
}
cd $env:Temp
MonitorAntivirus
NOTE: Though I’m specifying Windows Defender as the AntivirusName in the configuration file, it could really be anything. You could monitor for any Antivirus software you might be running, during the compile time, which takes me to my next section - Parameters file.
The script is using parameters file (sample below for reference) which basically tells the Azure Guest Configuration policy to monitor for that specific Antivirus software that you specify during the assignment.
Remember, you can use wildcard entry too. For eg., if you want to monitor for ‘Avast Antivirus’ and you’re not sure what is the complete name of the Antivirus Windows is referring it as, you can simply type in as Avast*
@(
@{
Name = 'AntivirusName'
DisplayName = 'Antivirus Name'
Description = "Name of the Antivirus Software to monitor."
ResourceType = "EPAntivirusStatus"
ResourceId = 'AV'
ResourcePropertyName = "AntivirusName"
DefaultValue = 'Windows Defender'
#AllowedValues = @('Avast','Windows Defender','CrowdStrike','Sentinel One')
}
)
This entire configuration is compiled into a .MOF file which will eventually be stored in the Azure blob storage account that you specify during the execution.
Make sure to read about how Azure Policy’s Guest Configuration works that will help you understand this script in detail.
Execution of this Custom Guest Configuration policy:
Pre-requisites:
- Modules that are needed by the configuration must be in available in
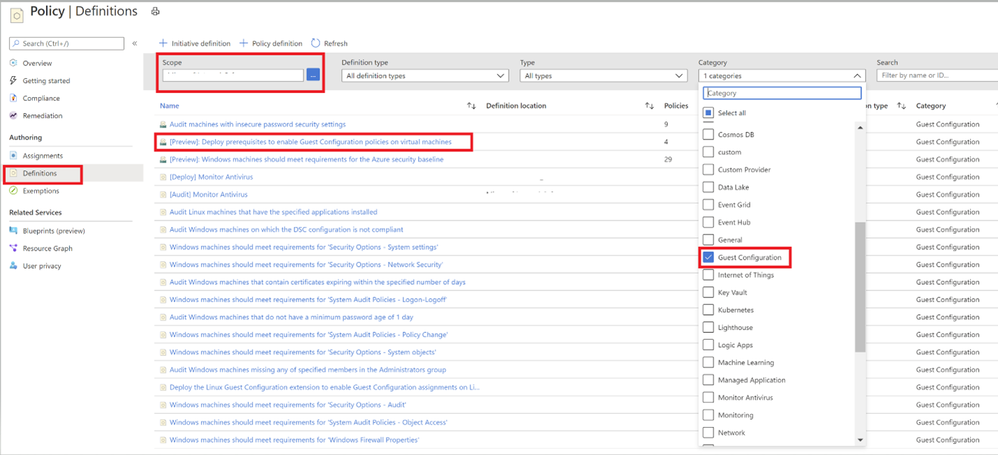
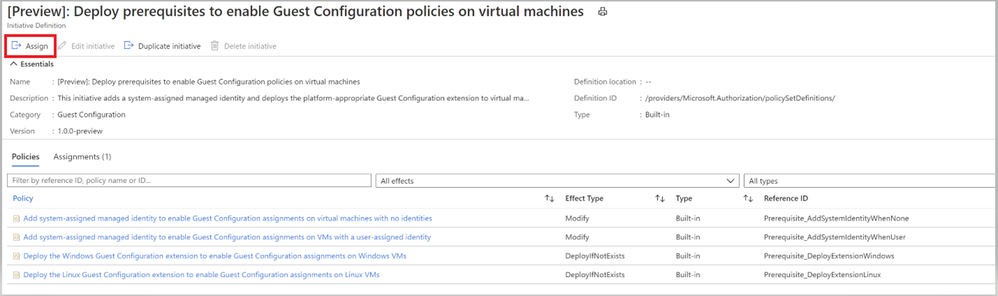
$Env:PSModulePath. So, make sure to download the entire artifact from the Github repository and save the unzipped folder to your local machine under ‘C:\Program Files\WindowsPowerShell\Modules’ before the execution. - To audit settings inside a machine, the Guest Configuration extension and a managed identity is required to audit Azure virtual machines. To deploy the extension at scale, make sure to choose appropriate scope and assign the policy initiative ‘Deploy prerequisites to enable Guest Configuration policies on virtual machines’ under Azure Policies as shown in the image (Image 3) below.
Refer to this article, to understand Scope in Azure Policy.
To understand the Effect Type of the policies, please refer to this article
Once you’ve assigned the Guest Configuration policy to a specific Scope, you can monitor the Compliance of the policy from the ‘Compliance’ section under ‘Azure Policy’. As shown in the below Image 5.

Once you have taken care of the pre-requisites, proceed with the execution of the policy.
Execution:
- Open the PowerShell as an administrator in your local machine and run the command ‘New-EPDSCAzureGuestConfigurationPolicyPackage’ which will create policy package for you in your Azure Subscription.
- You’ll first be prompted to enter a Resource Group Name, Resource Group Location, Storage Container Name, Storage account name and Storage SKU name
- You’ll then be prompted to login to your Azure Subscription
Refer to this article to learn about Storing Guest Configuration artifacts. - Once connected to your subscription, the script will compile the DSC configuration to a MOF file and will publish the Configuration package to the storage account (you defined in Step 2) in the blob storage (as shown in the below image 6)
- This eventually generates a Guest Configuration policy and publishes the Initiative under Definitions of the Azure Policies as a Guest configuration policy.
- Under the Policies tab, you’ll notice all the individual policy definitions in the initiative that contribute to this control, as shown in image 7 and Image 8.


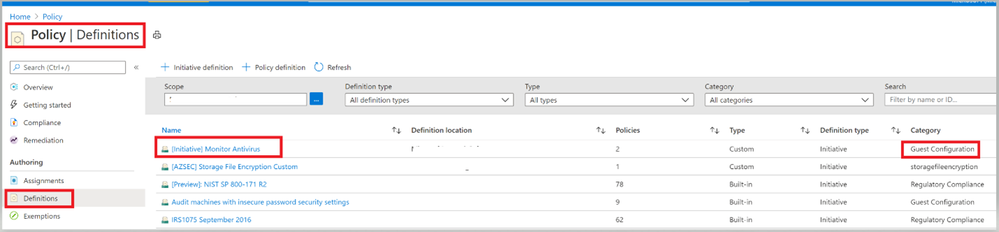
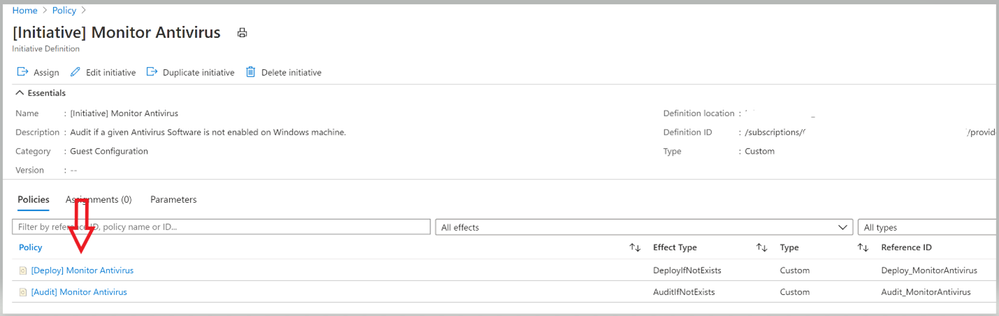
Now it’s time to assign this Initiative to the scope you desire to target. The term scope refers to all the resources, resource groups, subscriptions, or management groups that the definition is assigned to.
Please refer this article, to learn more about the assignment and for steps to assign it via PowerShell and Azure CLI.
While you’re assigning this Initiative to a Scope, you could modify the Assignment name if required as shown in the gif below.
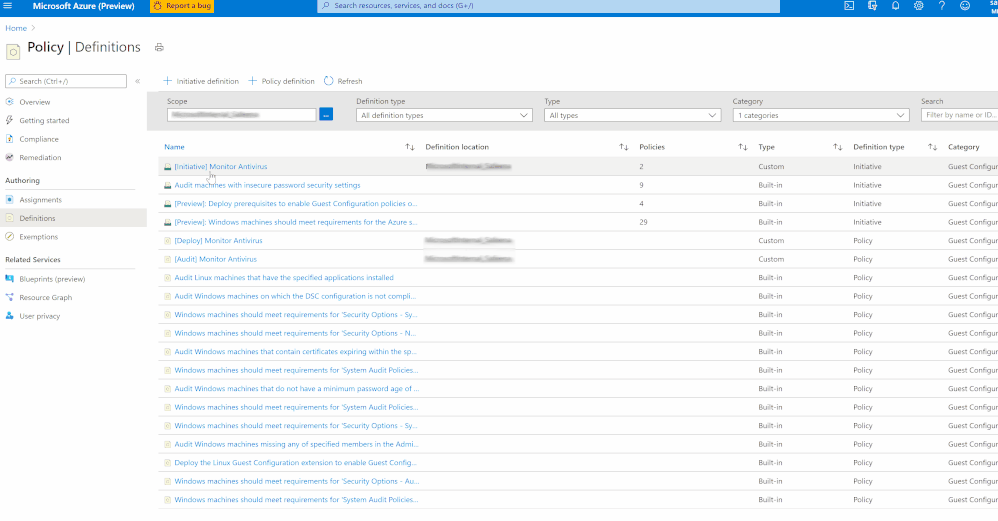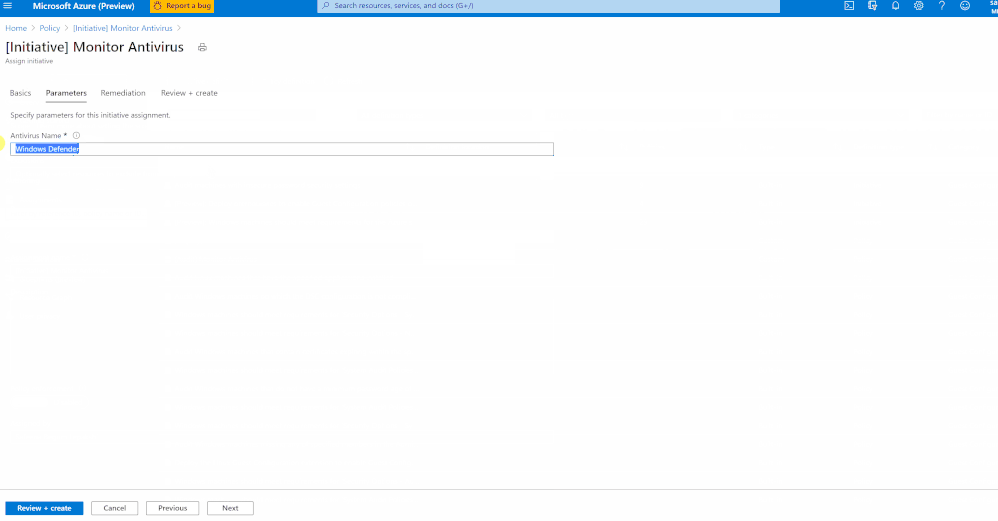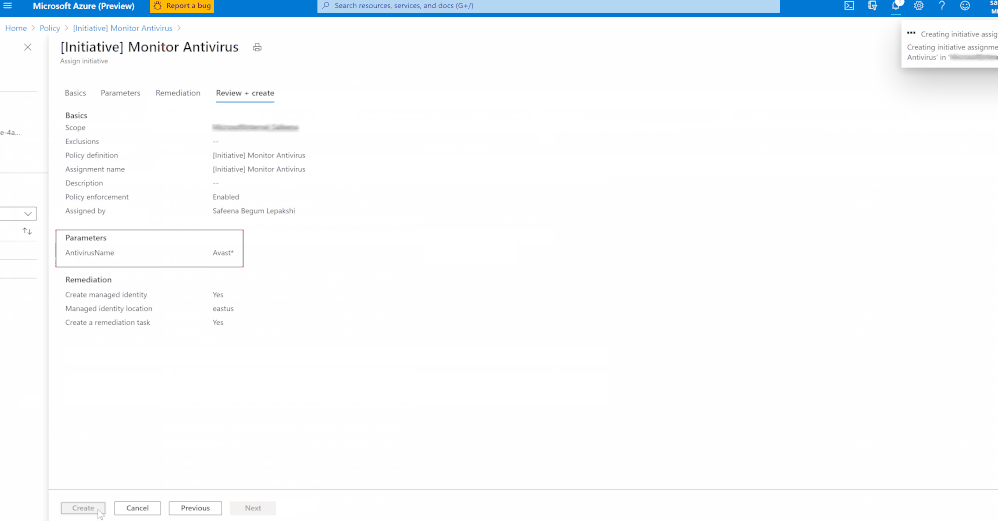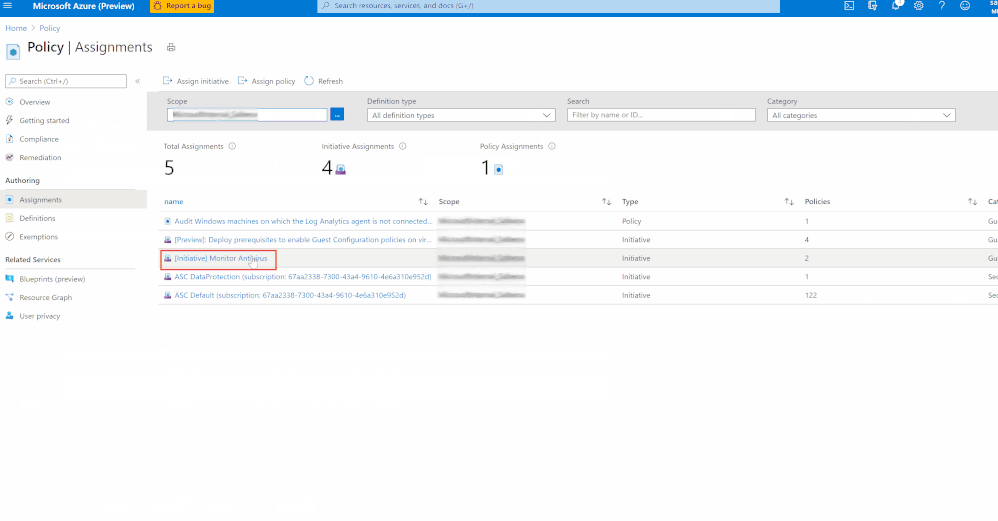
Once you’ve assigned the custom policy, review the Compliance state of the policies by navigating to ‘Compliance’ under Azure Policy and selecting the Initiative. The Resource compliance tab provides a granular view of each resource that's evaluated by a member policy of the currently viewed control.
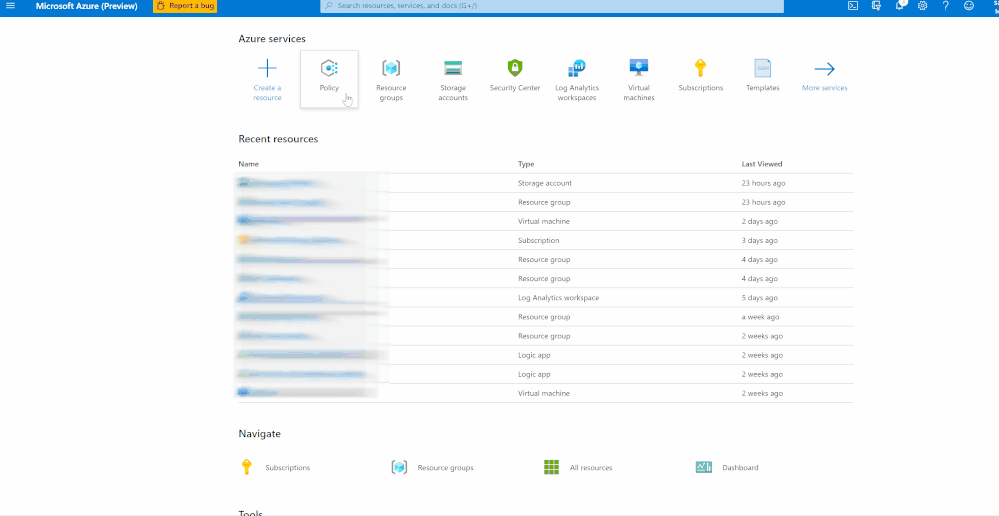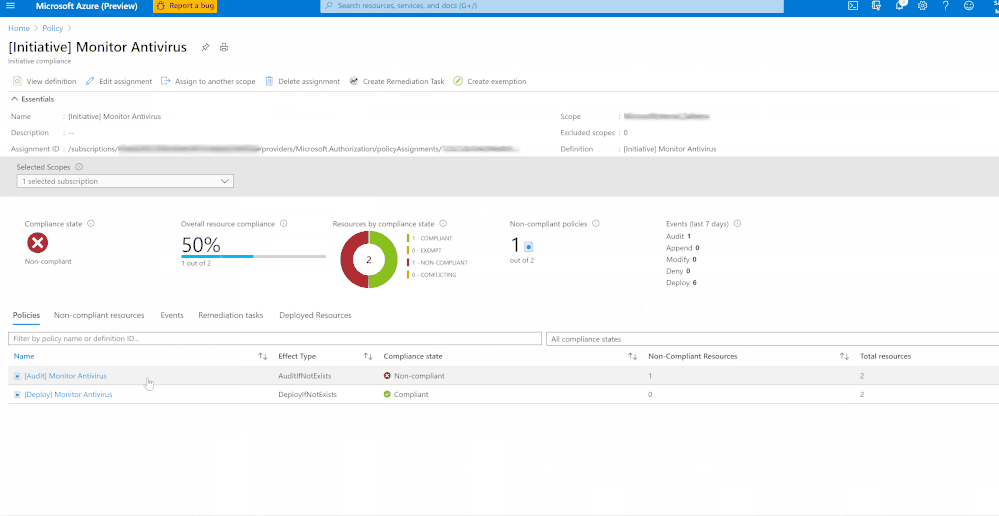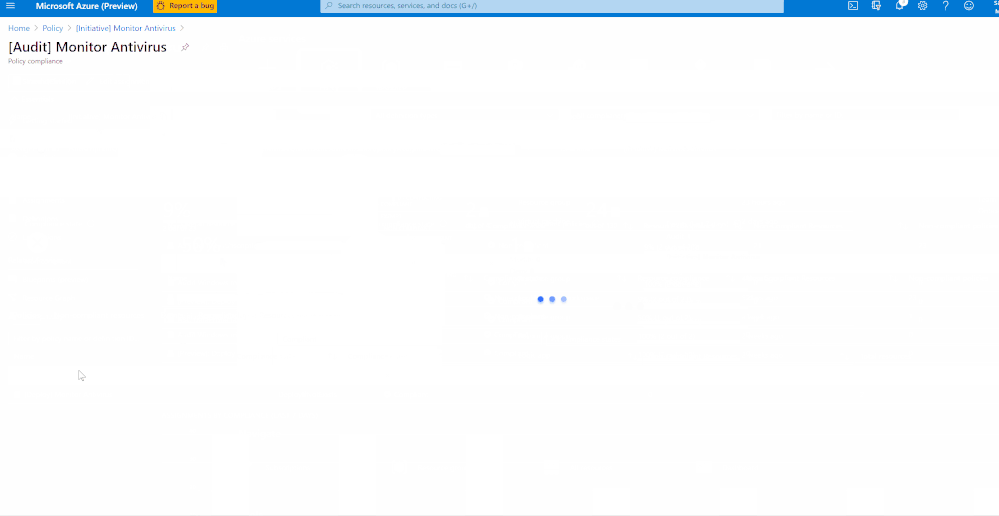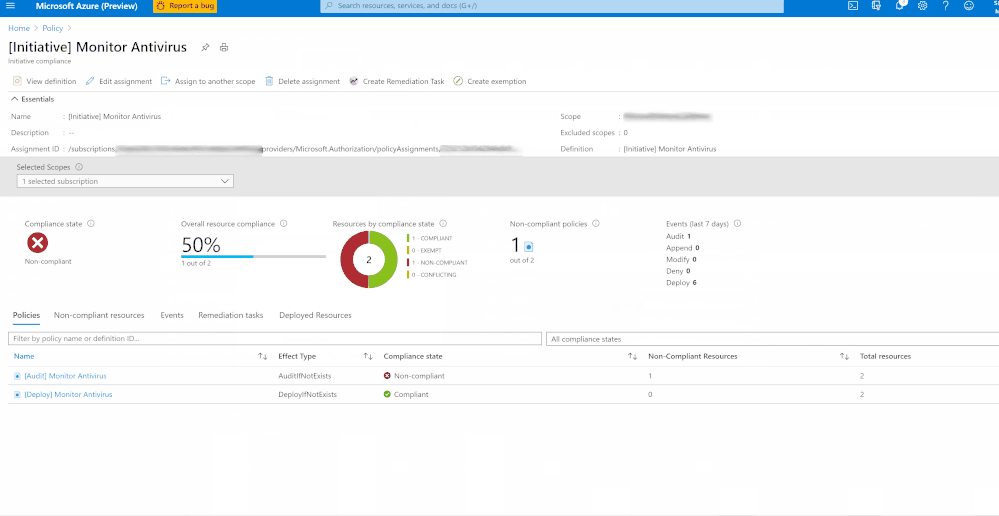
In my example, I’m monitoring to gather details of VMs which do not have installed and not running. I’ve two resources (epptest (VM without Avast Installed) and vmclient (VM with Avast Installed)) in the selected scope. The script is identifying the VM that do not have Avast installed and raising the non-compliance of the resource with the help of ‘Audit policy’.
Assign the Custom Initiative to Microsoft Defender for Cloud
You can add the custom Initiative to Microsoft Defender for Cloud to receive recommendations if your environment doesn’t follow the policy you created. As we learnt above, Defender for Cloud automatically runs continuous scans to analyze the security state of your Azure resources. When Defender for Cloud identifies potential security vulnerabilities, it creates recommendations that guide you through the process of configuring the needed security controls. Defender for Cloud updates the Endpoint Protection issue recommendations within 8 hours.
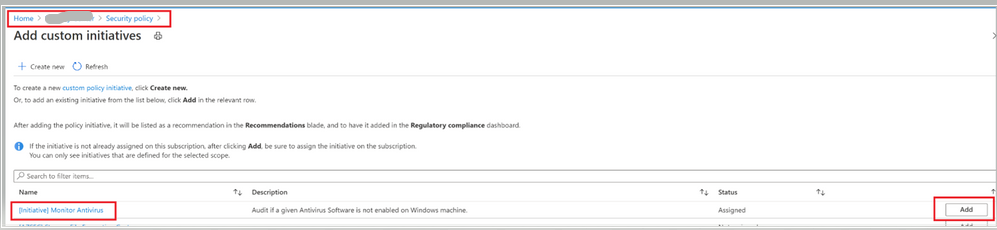
To assign this Custom Initiative, navigate to Security Policy under Defender for Cloud and choose the desired subscription or Management Group. Click on ‘Add a Custom Initiative’ under Your Custom Initiatives that should take you to a screen as below (Image 9), find the Initiative created above and click on ‘add’
Your new Initiative takes effect and you can see the impact in two ways:
- From the Defender for Cloud sidebar, under Policy & Compliance, select Regulatory compliance. The compliance dashboard opens to show your new custom initiative alongside the built-in initiatives.
- You'll begin to receive recommendations if your environment doesn't follow the policy you've defined.
To see the resulting recommendations for your policy, click Recommendations from the sidebar to open the recommendations page. The recommendations will appear with a "Custom recommendations" label as shown in Image 10
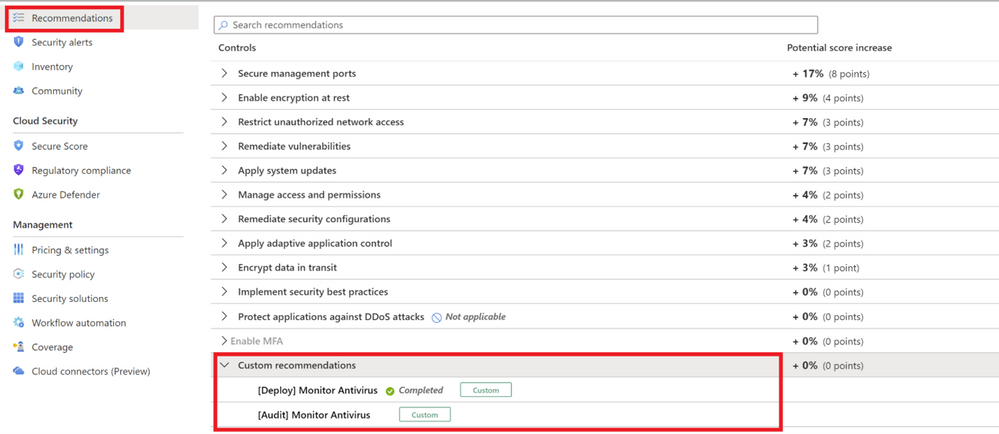
NOTE: Make sure to disable the Endpoint protection policy (in the built-in ASC initiative) that generates missing Endpoint protection recommendation inorder to prevent it appearing again and to avoid it to be counted to the overall Secure score.
The disable policy changes can take up to 12 hours to take effect.
Refer to this article to disable a recommendation to appear by disabling the specific policy that generates the recommendations.
Enhance custom Recommendations
You can further enhance your custom recommendations similar to the built-in recommendations. The built-in recommendations supplied with Microsoft Defender for Cloud includes details such as severity levels and remediation instructions. If you want to add this type of information to your custom recommendation, follow this article
This GitHub Artifact as well as many other can be found here:
Microsoft Defender for Cloud GitHub Repo
Additional Resource:
Shoutout to Microsoft365DSC which makes automation easy. Check it out on how it can help your business with this 2 minutes promotional video or reach out to @NikCharlebois if you're interested to learn more about it.
Are you an organization using Endpoint protection outside of what MDC supports? Don’t worry anymore, go ahead and deploy this policy to witness the magic.
Reviewer
Special Thanks to @Yuri Diogenes, Principal Program Manager, for envisioning this and for all the inputs to this article.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.