Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Azure PaaS Blog
URL
Copy
Options
Author
invalid author
Searching
# of articles
Labels
Clear
Clear selected
ADLS Gen2 storage rest API
API
APIM
API Management
APIs
arm template
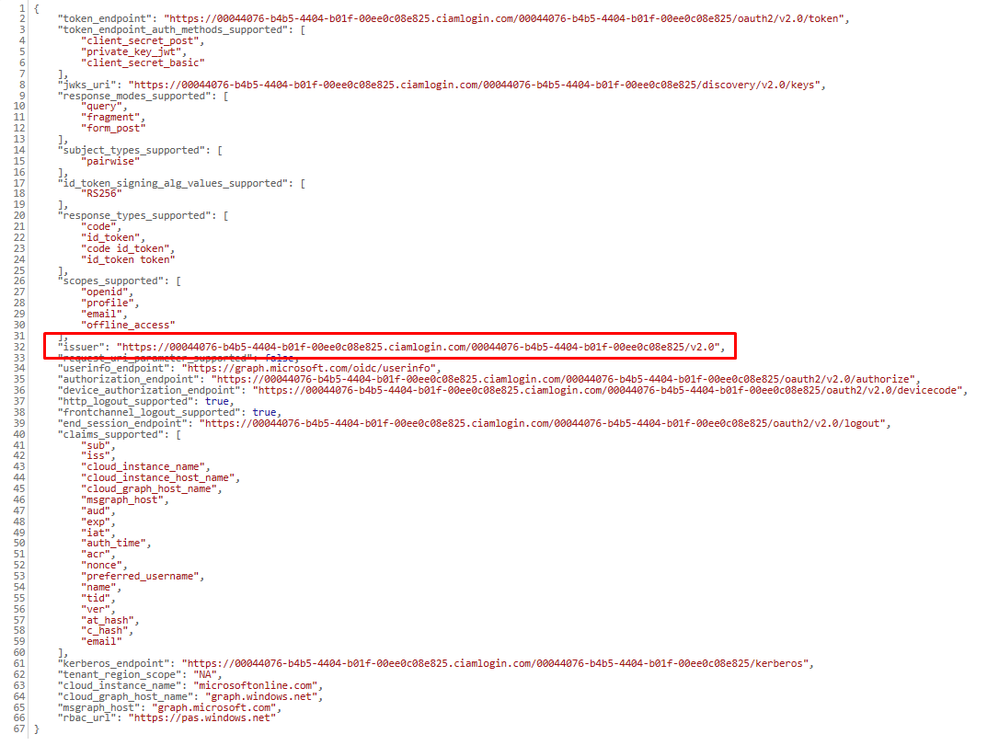
Authentication
Azure
Azure APIM
Azure API Management
Azure App Gateway
Azure Batch
Azure Blockchain
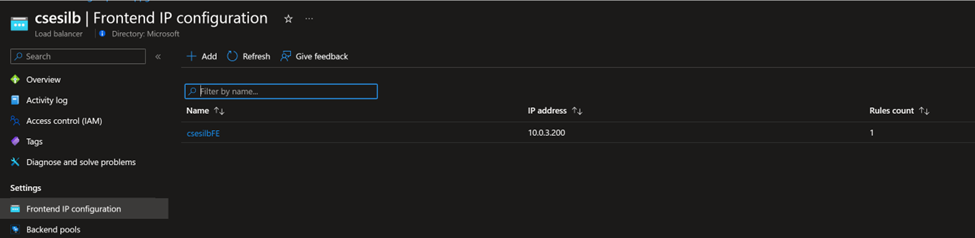
Azure Cache for Redis
Azure CDN
Azure Cloud Service
Azure Event Grid
Azure Event Hub
Azure function App
Azure Logic app with Azure Storage
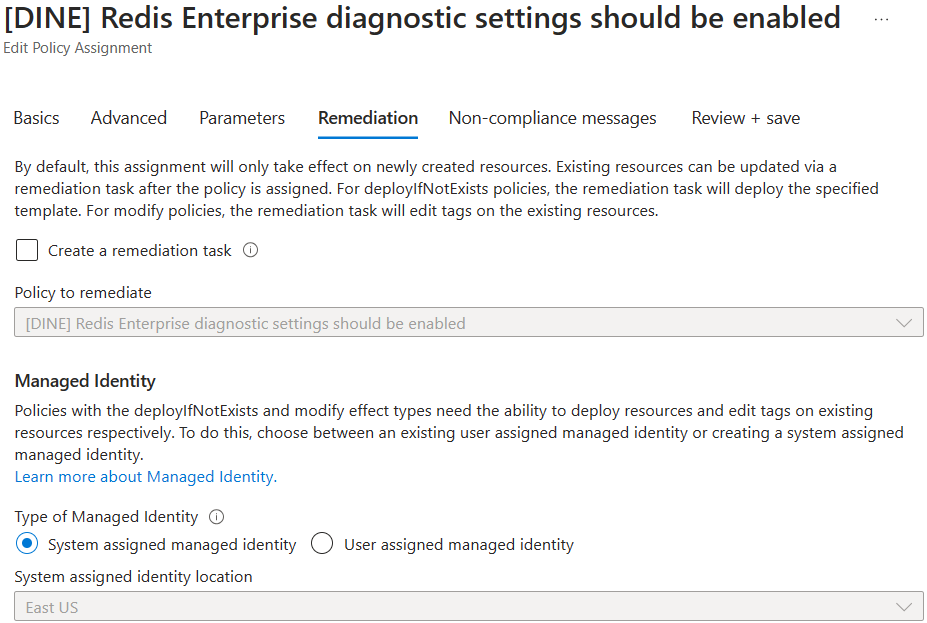
Azure Policy
Azure Portal
Azure Redis
Azure Resource Manager
Azure Service Bus
Azure Service Fabric
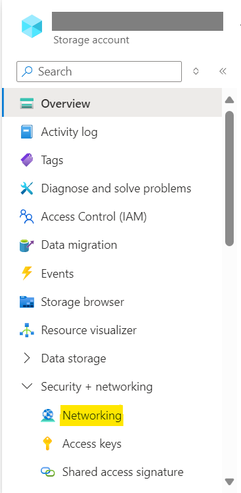
Azure Storage
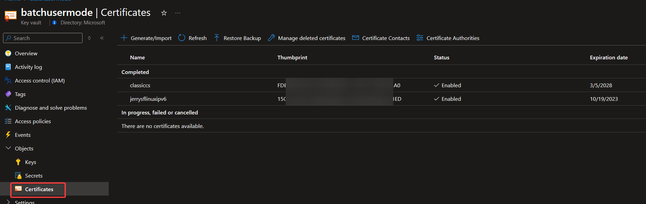
certificate
Changing Datapath in Service Fabric cluster
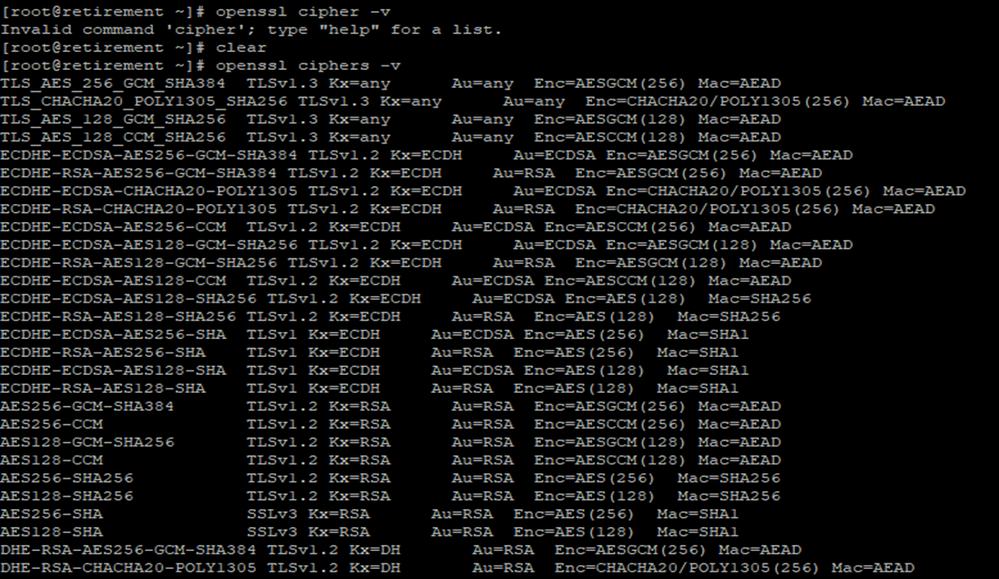
Connect to Azure Cache for Redis using SSL Port 6380 from Linux VM
C Sha
Custom RBAC role in Azure Storage to perform upload download operation & restrict delete operation
Custom Roles
FeatureVersionMismatch while performing a list blob operation
File Share
File Shares
HPC
http
JSON
Microsoft CDN
Notification Hub
Policy
postman
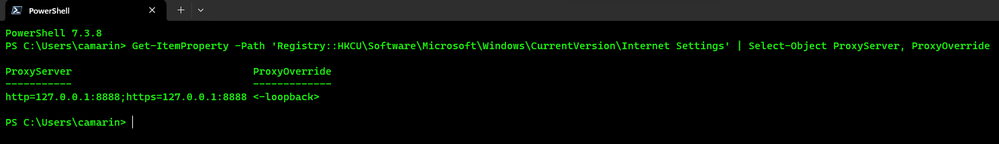
PowerShell
RBAC
RBAC Roles
REST API
Rest API using service principal
Role-based access control
roles
Service Fabric
Service Fabric node down due to self-signed Certificate issue
Terraform
The type of a blob in the container is unrecognized by this version
XmlException: Root element is missing while performing PUT operation
Options
- Mark all as New
- Mark all as Read
- Pin this item to the top
- Subscribe
- Bookmark
- Subscribe to RSS Feed















Latest Comments