- Home
- Azure
- Azure Networking
- Re: Private Endpoints - Disable Public Access
Private Endpoints - Disable Public Access
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 27 2023 03:14 AM
Hi,
We are developing our new software in Azure and we are using some CosmosDB, Key Vaults...
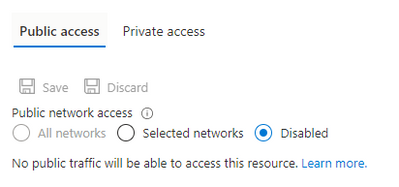
By default, all of them are published to internet. We use the default URI (https://testxxxxx.mongo.cosmos.azure.com:443/) and in Networking the Public Network Access is opened to "All networks".
For security reasons we want to change it. We don't want that our services are published to internet (now you can telnet to testdwh.mongo.cosmos.azure.com using 443 and 10255 ports.
So we disabled Public Access for one CosmosDB account:
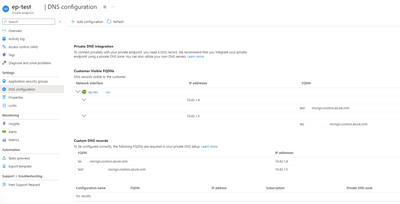
And then we enabled the Private Access adding a Private Endpoint:
But... after these changes, we don't know why but we still connect to testxxxxxx.mongo.cosmos.azure.com using 443 and 10255 from internet.
How can we block this connections from internet?
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 27 2023 10:43 AM
SolutionAlso, have you reviewed this article by chance?
https://learn.microsoft.com/en-us/azure/virtual-network/tutorial-restrict-network-access-to-resource...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 03 2023 06:49 PM
How about NSG? Please verify the rules under NSG
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 27 2023 10:43 AM
SolutionAlso, have you reviewed this article by chance?
https://learn.microsoft.com/en-us/azure/virtual-network/tutorial-restrict-network-access-to-resource...