- Home
- Azure
- Azure Networking
- Re: Only allow SSH/RDP traffic from Azure Bastion
Only allow SSH/RDP traffic from Azure Bastion
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 21 2020 04:57 AM
Hi all,
I'm trying to create NSG security rules that allow RDP/SSH traffic from Azure Bastion, but denies traffic on these ports for any other source. The only way people should be able to RDP/SSH into machines is by means of Bastion.
There doesn't seem to be a service tag for Azure Bastion. So I'm struggling to find a way to get the result we want.
Any ideas would be highly appreciated. Thanks in advance!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 21 2020 06:11 AM - edited Dec 21 2020 06:19 AM
SolutionI just found the solution to my own question. The solution was quite obvious by the way...
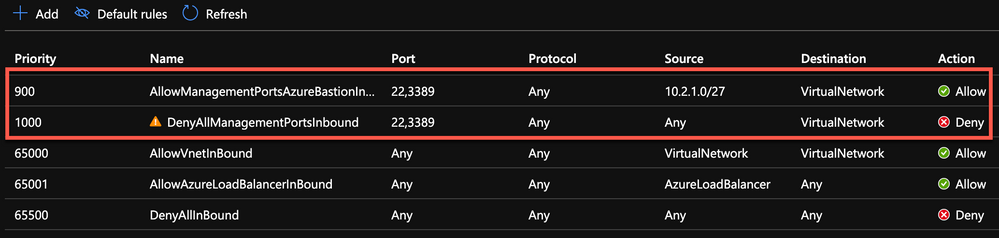
When deploying Azure Bastion, you create a subnet called "AzureBastionSubnet". The IP address range that's associated with this subnet can easily be configured in a security rule that allows incoming traffic on ports 22 and 3389.
In the example below I created a security rule with priority 900 called "AllowManagementPortsAzureBastionInbound". This rule ensures that incoming traffic on ports 22 and 3389 are allowed coming from the Azure Bastion subnet.
The second security rule, with priority 1000 called "DenyAllManagementPortsInbound", blocks all traffic on ports 22 and 3389. This rule will only be triggered if the source is from any other location, other than the Azure Bastion subnet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 09 2021 04:15 AM
Occured to me that you don't actually need that explicit deny.
By virtue of setting the allowed source IP address(s), any attempt to connect on port 22 or 3389 NOT from 10.20.10/27 will be dropped anyway.
On the other hand, if you want to drop anything else other than 22,3389, then you could a policy such as that.
Give it a try :)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 21 2020 06:11 AM - edited Dec 21 2020 06:19 AM
SolutionI just found the solution to my own question. The solution was quite obvious by the way...
When deploying Azure Bastion, you create a subnet called "AzureBastionSubnet". The IP address range that's associated with this subnet can easily be configured in a security rule that allows incoming traffic on ports 22 and 3389.
In the example below I created a security rule with priority 900 called "AllowManagementPortsAzureBastionInbound". This rule ensures that incoming traffic on ports 22 and 3389 are allowed coming from the Azure Bastion subnet.
The second security rule, with priority 1000 called "DenyAllManagementPortsInbound", blocks all traffic on ports 22 and 3389. This rule will only be triggered if the source is from any other location, other than the Azure Bastion subnet.