- Home
- Azure
- Azure Networking
- Re: DNS get private ip from private endpoint
DNS get private ip from private endpoint
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 27 2021 09:00 AM
Hello,
I have 2 pairing connected VLans. One 10.0.0.0/24 and one 10.0.1.0/24.
Azure AD Domain Service is located in VLan 10.0.0.0/24 and is the DNS service for both VLans.
In VLan 10.0.1.0/24, there is a Private Link End Point of a storage account zzz. .file.core.windows.net (10.0.1.5). When I call the storage account I always get the public IP of the storage account.
How can I resolve the internal IP of the storage account via both VLans?
Thanks for your supoort
Stefan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 17 2021 04:54 AM
Hi Stefan,
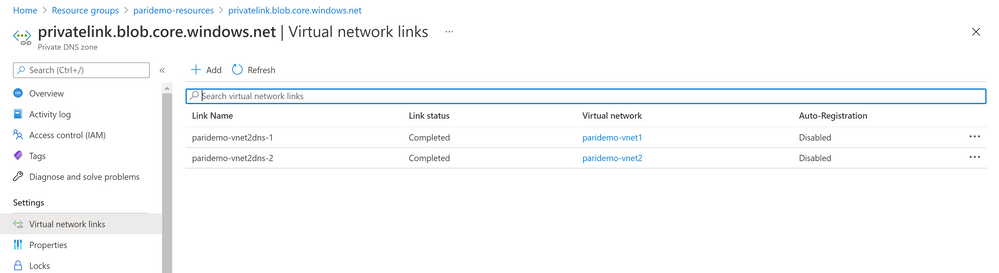
When you are using the Private Endpoint for your Storage Account, you would have a Private DNS Zone (if you want). It's name is like "privatelink.<resource-type>.core.windows.net". If you go the Private DNS Zone resource, you can add the both VNets to this Private DNS Zone.
As I had a same scenario in one of my projects, I can share the Terraform code, I developed.
resource "azurerm_resource_group" "example" {
name = "${var.projectname}-resources"
location = "West Europe"
}
# -----------------------------------
# VNET 1
# -----------------------------------
resource "azurerm_virtual_network" "example" {
name = "${var.projectname}-vnet1"
location = azurerm_resource_group.example.location
resource_group_name = azurerm_resource_group.example.name
address_space = ["10.3.0.0/16"]
dns_servers = ["168.63.129.16"]
}
resource "azurerm_subnet" "exampledefault" {
name = "${var.projectname}-default"
resource_group_name = azurerm_resource_group.example.name
virtual_network_name = azurerm_virtual_network.example.name
address_prefixes = ["10.3.1.0/24"]
}
resource "azurerm_subnet" "exampleprivate" {
name = "${var.projectname}-private"
resource_group_name = azurerm_resource_group.example.name
virtual_network_name = azurerm_virtual_network.example.name
address_prefixes = ["10.3.2.0/24"]
enforce_private_link_endpoint_network_policies = true
}
# -----------------------------------
# VNET 2
# -----------------------------------
resource "azurerm_virtual_network" "example2" {
name = "${var.projectname}-vnet2"
location = azurerm_resource_group.example.location
resource_group_name = azurerm_resource_group.example.name
address_space = ["10.4.0.0/16"]
dns_servers = ["168.63.129.16"]
}
resource "azurerm_subnet" "exampledefault2" {
name = "${var.projectname}-default"
resource_group_name = azurerm_resource_group.example.name
virtual_network_name = azurerm_virtual_network.example2.name
address_prefixes = ["10.4.1.0/24"]
}
# -----------------------------------
# Storage
# -----------------------------------
resource "azurerm_storage_account" "example" {
name ="${var.projectname}stg"
resource_group_name = azurerm_resource_group.example.name
location = azurerm_resource_group.example.location
account_tier = "Standard"
account_replication_type = "LRS"
}
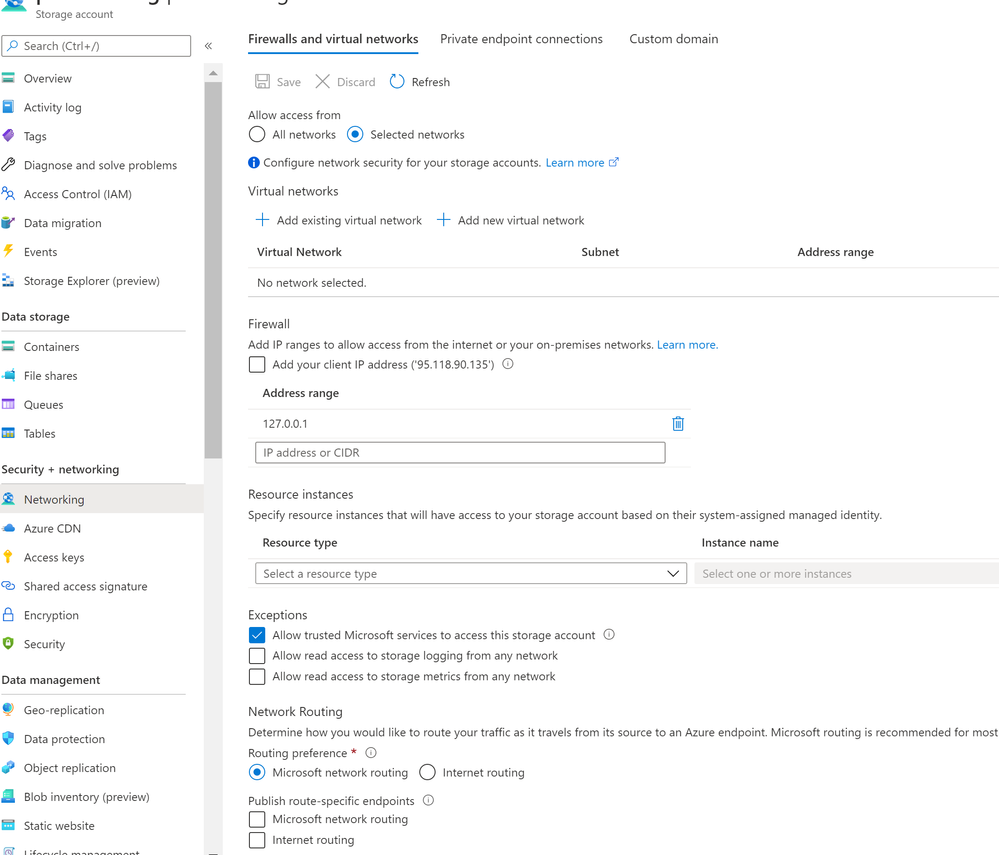
resource "azurerm_storage_account_network_rules" "network_rule_publisher" {
depends_on = [
azurerm_private_endpoint.example
]
resource_group_name = azurerm_resource_group.example.name
storage_account_name = azurerm_storage_account.example.name
default_action = "Deny"
ip_rules = ["127.0.0.1"]
bypass = []
}
// Azure services DNS zone
// https://docs.microsoft.com/en-us/azure/private-link/private-endpoint-dns#azure-services-dns-zone-configuration
resource "azurerm_private_dns_zone" "example" {
name = "privatelink.blob.core.windows.net"
resource_group_name = azurerm_resource_group.example.name
}
resource "azurerm_private_endpoint" "example" {
name = "${var.projectname}-privateendpoint"
location = azurerm_resource_group.example.location
resource_group_name = azurerm_resource_group.example.name
subnet_id = azurerm_subnet.exampleprivate.id
private_service_connection {
name = "${var.projectname}-stg-pe-connection"
is_manual_connection = false
private_connection_resource_id = azurerm_storage_account.example.id
subresource_names = ["blob"]
}
private_dns_zone_group {
name = azurerm_private_dns_zone.example.name
private_dns_zone_ids = [azurerm_private_dns_zone.example.id]
}
}
# connect the Private Zone to the VNet
resource "azurerm_private_dns_zone_virtual_network_link" "example" {
name = "${var.projectname}-vnet2dns-1"
resource_group_name = azurerm_resource_group.example.name
private_dns_zone_name = azurerm_private_dns_zone.example.name
virtual_network_id = azurerm_virtual_network.example.id
}
resource "azurerm_private_dns_zone_virtual_network_link" "example2" {
name = "${var.projectname}-vnet2dns-2"
resource_group_name = azurerm_resource_group.example.name
private_dns_zone_name = azurerm_private_dns_zone.example.name
virtual_network_id = azurerm_virtual_network.example2.id
}
# -----------------------------------
# VM in Vnet1
# -----------------------------------
resource "azurerm_network_interface" "example" {
name = "${var.projectname}-nic-1"
location = azurerm_resource_group.example.location
resource_group_name = azurerm_resource_group.example.name
ip_configuration {
name = "internal"
subnet_id = azurerm_subnet.exampleprivate.id
private_ip_address_allocation = "Dynamic"
}
}
resource "azurerm_windows_virtual_machine" "example" {
name = "${var.projectname}-vm-1"
resource_group_name = azurerm_resource_group.example.name
location = azurerm_resource_group.example.location
size = "Standard_F2"
admin_username = "adminuser"
admin_password = "P@$$w0rd1234!"
network_interface_ids = [
azurerm_network_interface.example.id,
]
os_disk {
caching = "ReadWrite"
storage_account_type = "Standard_LRS"
}
source_image_reference {
publisher = "MicrosoftWindowsServer"
offer = "WindowsServer"
sku = "2016-Datacenter"
version = "latest"
}
}
# -----------------------------------
# VM in Vnet2
# -----------------------------------
resource "azurerm_network_interface" "example2" {
name = "${var.projectname}-nic-2"
location = azurerm_resource_group.example.location
resource_group_name = azurerm_resource_group.example.name
ip_configuration {
name = "internal"
subnet_id = azurerm_subnet.exampledefault2.id
private_ip_address_allocation = "Dynamic"
}
}
resource "azurerm_windows_virtual_machine" "example2" {
name = "${var.projectname}-vm-2"
resource_group_name = azurerm_resource_group.example.name
location = azurerm_resource_group.example.location
size = "Standard_F2"
admin_username = "adminuser"
admin_password = "P@$$w0rd1234!"
network_interface_ids = [
azurerm_network_interface.example2.id,
]
os_disk {
caching = "ReadWrite"
storage_account_type = "Standard_LRS"
}
source_image_reference {
publisher = "MicrosoftWindowsServer"
offer = "WindowsServer"
sku = "2016-Datacenter"
version = "latest"
}
}
// output "myoutput" {
// value = azurerm_private_endpoint.example.private_service_connection[0].private_ip_address
// }
// output "dns_id" {
// value = azurerm_private_dns_zone.example.id
// }
// output "dns_name" {
// value = azurerm_private_dns_zone.example.name
// }
If you don't want the Storage Account be accessible from Internet/ Public Endpoint, you should configure the Storage Account Networking as follows. The code above does the same configuration for the Storage Account.
Regard
Parisa