- Home
- Azure
- Azure Networking
- Re: Azure VMware Solution - Design Networking
Azure VMware Solution - Design Networking
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 05 2021 03:40 PM
Hello the community
I would like your opinion and your help on the network implementation of the AVS solution
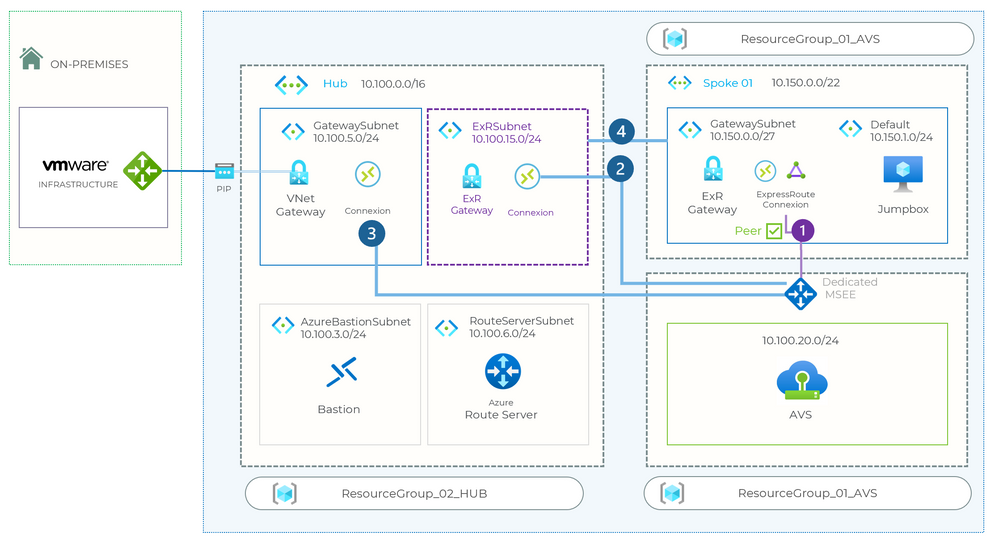
Design picture
I deployed a Vpn Gateway connection to interconnect the on-premise connection to Azure.
(VpnGw Routed-Based 2e generation)
I deployed Azure Route Server, Azure Bastion and Azure VMware Solution.
To connect AVS to my Hub, I wanted to deploy another ExpressRoute Gateway in my hub. (purple, connection 2)
Unfortunately, this doesn't seem possible.
The peering (connection 4) doesn’t work, but I’m not really surprised.
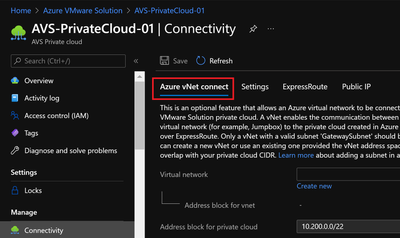
When I deployed AVS, an 'Azure vNet connect' option allowed me to create a new vNet, only in the same resource group (ResourceGroup_01_AVS).
In this vNet, the vNet Gateway (ExR Gateway) is connected.
I added a new subnet to connect the Jumpbox and manage AVS.
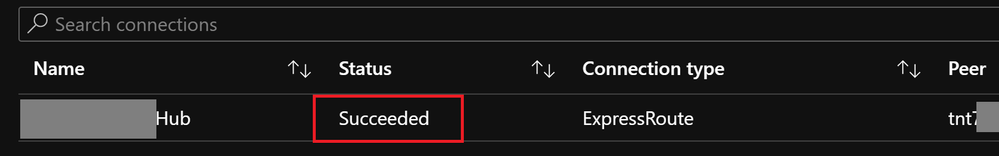
It's not possible for me to create a new connection (connection 3) to AVS with a new ExpressRoute key.
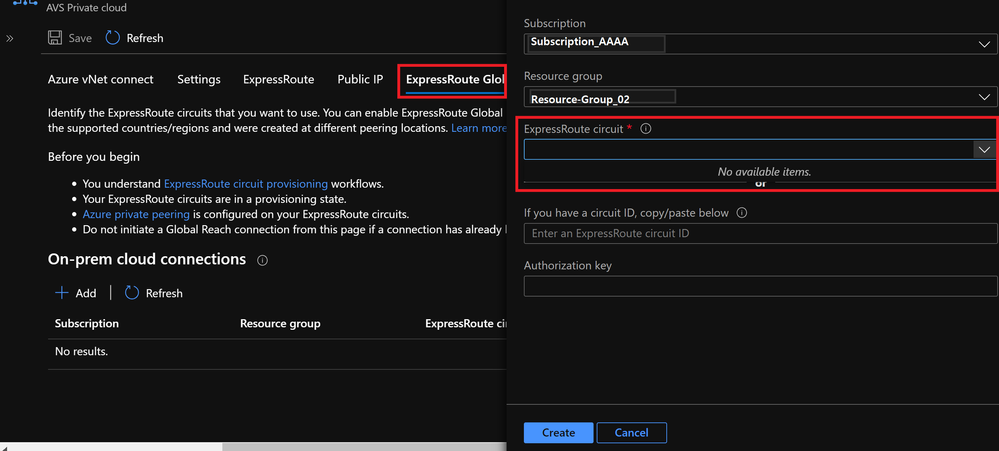
And to use ExpressRoute Global Reach, I need an existing ExpressRoute. (no available items)
And for now, I only have one vpn.
Since I’m at a dead end, I take any hypothesis of resolution.
To complete the discussion, two diagrams I could find in Microsoft sessions that can complement our
exchange.
Use case 01 - AVS and NVA, VPN over ExR 
Use case 02- AVS and NVA, 2 Vnet 
Thank you in advance for your time and help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 08 2021 10:33 AM
@Olivier-IT Best is to follow Configure a site-to-site VPN in vWAN for Azure VMware Solution - Azure VMware Solution | Microsoft D... This will guide you through the process of setting up VWAN which will get the necessary transitivity in place for you to be able to connect from on-premise across that IPSEC tunnel and ExR GW setup in the VWAN HUB into AVS. That way you don't need that spoke, the bastion and jumphost in place at all. As soon as the tunnel is there you will find yourself being able to connect straight to the AVS vcenter, NSX or HCX console. Hope this helps. Please feel free to reach out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 13 2021 01:17 AM
Thank you for your answer @MSDennis
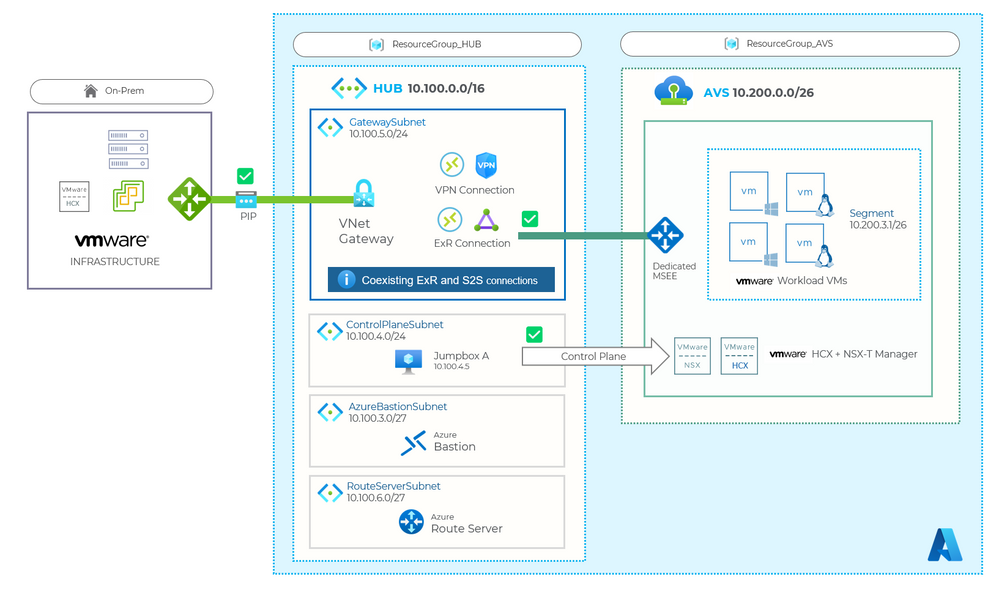
I solved my design problem. The result in the following diagram.
Although it is possible to use vWAN, it seemed possible to use Azure Route Server, by making coexist a VPN connection and ExpressRoute connection.
:blue_book:https://docs.microsoft.com/en-us/azure/expressroute/expressroute-howto-coexist-resource-manager#add
From Network Watcher
IP Flow verify
Work continues on NSX/HCX configuration for layer 2 extension and SRM configuration.
Thanks for your help Dennis !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 13 2021 02:28 AM
@Olivier-IT Azure Route Server is the core component also used in VWAN. VWAN, it being managed as a service all together provides redundancy for all of the GW services it provides (except for Azure Firewall) out of the box across AZs in the region. There is nothing you need to setup to get that redundancy therefore.
If you add everything up (VPN GW across AZ (specific type), Route server and High performance ExR GW) and compare that to VWAN you will find that the latter is also cheaper for the customer.
Pricing and redundancy out of the box therefore makes VWAN the preferred way forward. I have not even mentioned future expansion capabilities.
Hope this is useful.