- Home
- Azure
- Azure Networking
- Re: Avoid S2S VPN route propagation?
Avoid S2S VPN route propagation?
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 16 2023 03:37 AM - edited Jan 16 2023 03:38 AM
Hi
I'm curious if I can somehow avoid remote S2S subnets to be propagated as routes to all peered or VPN connected vnets in Azure, and even other S2S connections.
Is this where the "UsePolicyBasedTrafficSelectors" + "UseCustomTrafficSelectors" come into place with the connection? And are the above properties linked together?
I assume "UsePolicyBasedTrafficSelectors" VPN without any BGP setup, will require UDRs pointing to the GW for the subnets in need of connecting through VPN?
/Thomas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 17 2023 02:28 AM
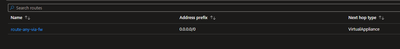
Hi - when you have an hub and spoke network in place then you might also have udr's in use at each of your spokes... with hin that udr you can disable route propagation:
with one route
With s2s to azure vpn gateway ist not possible I believe.. you couldt terminate you s2s at your nva for example fortigate. here you can have policies per S2S connection
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 17 2023 01:14 PM
@tommykneetz - thanks for the answer!
I've read about the disable option for route propagation on subnets. It doesn't seem to scale... I would have to do that in every subnet where I would filter out the routes, and worse - it would filter out all gateway routes, right?
So I guess it leaves me with either doing some NAT'ing on the VPN connection to avoid the overlap, or to use a NVA, as you also suggest, to have more control of the route injection/propagation.
/Thomas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 17 2023 11:15 PM