- Home
- Partner discussion topics
- Marketplace blog
- Get defense-in-depth email security, now available via Azure Marketplace
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
This guest post is by Arun Singh, VP of Marketing at Abnormal Security.
In the past decade, there have been two major shifts in the world of email. First, enterprises have moved from on-premises email servers to cloud email solutions like Microsoft 365 for better employee experience and productivity. According to the 2021 Gartner Market Guide for Email Security, more than 70% of global enterprises have made significant investments in transforming their email infrastructure to the cloud.
The second shift has been in the mindset and tactics of threat actors. Attackers have changed from traditional email attacks that were low- to mid-value, low- to mid-impact (spam, campaign phishing, ransomware based on malicious URL, and downloads) to modern email attacks that are high-value and high-impact (business email compromise, supply chain compromise, and advanced ransomware). The shift in the attacker’s mindset is motivated by the fact that the modern attacks yield higher return on investment (ROI).
This is unfortunately evidenced by the rise in cybercrime losses, as these attack types evade traditional email security solutions like secure email gateways (SEGs). In the 2021 IC3 Internet Crime Report, produced by the FBI, socially engineered attacks (including business email compromise, spoofing, and phishing) took the top spot in cybercrime financial losses. For instance, business email compromise (BEC) cost businesses and consumers over $2.4 billion of the $6.9 billion total, making up 35% of losses. The BEC challenge has only increased with time. Between July 2019 and December 2021, there was a 65% increase in identified global exposed losses from BEC.
A fundamentally different approach: known bad vs. known good
SEGs employ a rules-and-policies-based approach to block email attacks. The fundamental problem with that approach is that it only looks for known bad indicators of compromise (IOCs). Examples of IOCs include emails originating from bad IPs, emails with malicious links, and emails with malicious attachments. Modern attacks utilize social engineering tactics, arise from legitimate domains, contain only text or legitimate links and attachments, and do not have conventional attack signatures. Thus, a rules-and-policies-based approach that relies solely on threat intelligence is not effective and results in security teams staying two steps behind the attacker.
By contrast, a modern approach like that of Abnormal Security can baseline known good behavior of users and detect anomalies to block attacks. Abnormal Security is a cloud-based, native API architecture email security solution that leverages behavioral data science to detect and stop modern attacks with high efficacy. The API-based approach, unlike traditional journaling approaches taken by SEGs, integrates directly with Microsoft 365 through Microsoft Graph API and its ecosystem of security tools. Abnormal Security leverages more than 45,000 cloud signals to detect anomalies, block attacks, and identify compromised accounts quickly and precisely.
Complementing Microsoft for advanced protection
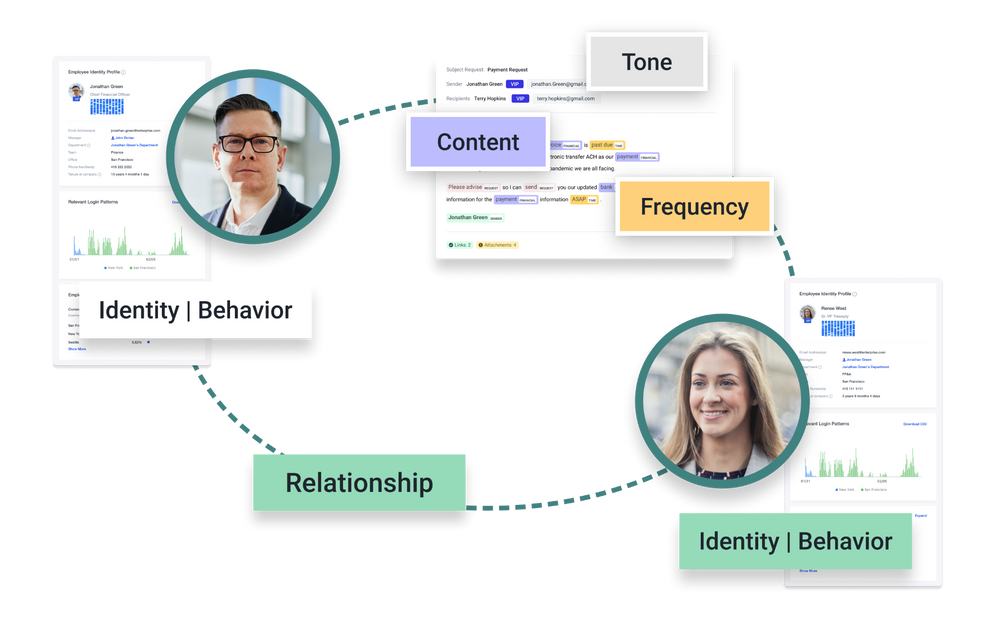
Let’s take a look at how Abnormal complements Microsoft in this unique approach. There are three pillars to Abnormal’s behavioral approach—identity, context, and content—which when combined result in high-detection efficacy against modern attacks.
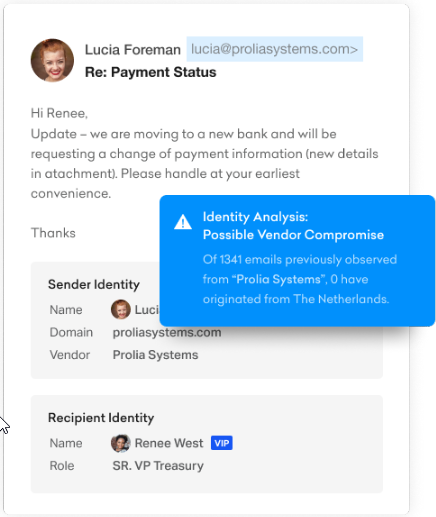
Identity: The native API integration with Microsoft 365 and Azure Active Directory allows Abnormal to automatically build an identity graph across all your employees, including highly targeted executives, to model identity information and determine “who is who” within an organization. The API approach provides a solid known good baseline, allowing Abnormal to analyze every incoming email, both in real time and retroactively. The identity graph also contains context gained from Microsoft cloud signals, such as typical devices and/or browsers used by employees to sign into their email accounts, usual sign-in locations, failed sign-in attempts, and more. The same applies to third-party supply chain partners and vendors. Any deviation from the known good behavior is a flag to be closely analyzed through correlation with thousands of other signals to thwart supply chain attacks, including vendor email compromise, invoice fraud, vendor impersonation, and more.
Context: The native API integration with Microsoft allows for enhanced context including signals and relationships across communication patterns. A unique advantage of the integration is that Abnormal’s visibility, unlike the SEG, is not limited to inbound and outbound email. It can obtain richer and enhanced context with visibility into the internal mail flow within an organization.
Let’s take the example in which an attacker sends an email from a compromised vendor account to an unsuspecting employee in accounts payable. Abnormal contextualizes which invoicing software the vendor generally uses, typical bank account information, previous communication patterns between these two people, and many other signals to create a known good baseline context, which can effectively detect anomalous behavior and block the malicious email, even when it is delivered from a legitimate account.
Content: The API integration also allows real-time content analysis through natural language processing (NLP) and natural language understanding (NLU) models, which enable Abnormal to analyze the tone and intent of the email in real time. Attackers often attempt to exploit human behavioral weaknesses by applying a sense of urgency, organizational pressure, and similar tactics in their communications. By understanding how people typically communicate with one another, Abnormal’s machine learning models can effectively detect when an attack is occurring. For example, when the CFO is impersonated and the attacker uses a sense of urgency to encourage the recipient to submit a wire transfer for a new purchase order, Abnormal understands that this is anomalous behavior for the CFO and blocks the attack, potentially saving hundreds of thousands of dollars for the organization.
True defense in depth for complete email security
Many SEG solutions require organizations to turn off, either fully or partially, the security features and capabilities native to Microsoft security solutions. On the surface, an architecture with a SEG and Microsoft 365 gives an illusion of defense in depth to organizations while it actually is a duplication of the same defenses. In essence, when organizations use a SEG, they pay for the same capabilities that they receive through strong Microsoft security solutions, particularly Exchange Online Protection and Microsoft Defender for Office 365, increasing their costs.
In contrast, Abnormal provides a different approach that leverages the protections already available in Microsoft. When Abnormal’s behavioral data science is layered with Microsoft threat intelligence, the two solutions provide organizations with a true defense-in-depth approach that stops the full spectrum of attacks. With this approach, organizations no longer have to turn off native Microsoft security features. Instead, they benefit from the full power of both Abnormal and Microsoft that are complementary to each other.
The two solutions combined stop common email threats such as spam, graymail, and malware, as well as advanced attacks, including business email compromise, credential phishing, account takeovers, supply chain compromise, and others. This added protection ensures that employees are protected not only from external emails, but also from those originating from compromised employee accounts within their own organization.
The combined solution is so powerful that we have observed an increasing trend where today, two out of three Abnormal customers do not use SEGs at all. Instead, they rely solely on the security controls in Abnormal and Microsoft to protect their organizations.
If you’re interested in ensuring that your employees are protected against modern email attacks, you can purchase Abnormal Integrated Cloud Email Security directly from the Microsoft Azure Marketplace. You can also learn more about how Abnormal integrates with Microsoft and see why an increasing number of Fortune 1000 companies have already chosen Abnormal.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.