- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- How to migrate to Azure Information Protection from other labeling solutions
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Classification and labeling solutions are important tools for organizations to get control over their data, understand where their data resides, the sensitivity of documents and apply actions based on the information’s sensitivity, such as applying encryption.
Some of organizations have already implemented classification and labeling solutions in the past for their unstructured documents (like Secure Islands IQP for example) and are now looking to migrate from another labeling solution to Azure Information Protection to enjoy the benefit of having a labeling solution that is highly integrated with their Office 365 environment and integrates with a growing ecosystem of 3rd-party solutions, such as Adobe Acrobat reader, among many others.
For such organizations it’s important to have the ability to leverage the existing labeled documents and have these labels automatically converted to the labeling used in Azure Information Protection.
Usually the document label is stored as metadata in the form of a Custom Property within the document itself.
The Azure Information Protection client can be configured to pick-up the Custom Property, and Azure Information Protection admins can create a mapping between the old labels and the new Azure Information Protection labels.
There are a few things you should be aware of when implementing this:
- This configuration uses an advanced client setting that you must configure in the Azure portal.
- This configuration is currently not compatible with the new default behavior that protects PDF files by using the ISO standard for PDF encryption. In this scenario, .ppdf files cannot be opened by File Explorer, PowerShell, or the Azure Information Protection scanner. To resolve this, use the advanced client setting to not use the ISO standard for PDF encryption.
- This feature is currently only available on Windows running the Azure Information Protection client and at a later stage will be supported with the unified labeling client for Windows. This functionality is not implemented in the native sensitivity labeling experience in the Office apps.
- If you have files other than PDF and Office documents that are protected by Secure Islands, these can be relabeled after you edit the registry as described in the preceding section.
When setting up the below configuration, the new Azure Information Protection label is applied by the Azure Information Protection client as follows:
- For Office documents: When the document is opened in the desktop app, the new Azure Information Protection label is shown as set and is applied when the document is saved.
- For File Explorer (Right Click -> Classify and Protect experience): In the Azure Information Protection dialog box, the new Azure Information Protection label is shown as set and is applied when the user selects Apply. If the user selects Cancel, the new label is not applied.
- For PowerShell: Set-AIPFileLabelapplies the new Azure Information Protection label. Get-AIPFileStatus doesn't display the new Azure Information Protection label until it is set by another method.
- For the Azure Information Protection scanner: Discovery reports when the new Azure Information Protection label would be set and this label can be applied with the enforce mode.
Mapping old labels to Azure Information Protection labels in documents
To be able to setup a mapping between the old labels and the new Azure Information Protection labels, the admin should follow these steps:
- Identify the Custom Properties added by the old labeling solution.
- Define the logical mapping between the old labels by the Custom Property and the new Azure Information Protection labels by the Azure Information Protection label ID.
- Configure the AIP Advanced Settings to identify the old labels and apply the new Azure Information Protection labels.
Identify the Custom Properties added by the old labeling solution
- Open a file labeled by the old solution and navigate to the Advanced Properties section
- Navigate to the Custom tab and identify the added property name and the value. In our example, the Custom Property added by the old solution is “Classification” and the value is “Internal”
- Identify the rest of the label names available from your previous solution (the possible values of the above “Classification” Custom Property).This can be done by opening different already labeled documents OR by getting this information from the management portal of the old solution if available.
- By now, you should have the knowledge about the old label custom property name and all the possible values (previously configured labels). For example:
- Custom Property name: “Classification”
- Custom Property values (old labels): “Public”, ”Internal” ,”Confidential”, ”Secret”
Define the logical mapping between the old labels by the Custom Property and the new Azure Information Protection labels by the Azure Information Protection label ID.
- Identify the Azure Information Protection label IDs that you would like to map from the Azure Information Protection portal
- In the Azure Information Protection admin console (https://aka.ms/AIPConsole), select Labels in the blade on the left, and then click the label you want to create the mapping for
- Copy the label ID located at the bottom of the page to a document for use later.
Repeat this for each label in the target and source tenant you wish to create a mapping for.
- By now you should have all the Azure Information Protection label names and ID. For example:
- “Pubic” Label ID 11ba5c36-b7cf-1234-bbc2-bd5b3a9f9511
- “General” Label ID 22ba5c36-b7cf-1234-bbc2-bd5b3a9f9522
- “Confidential” Label ID 33ba5c36-b7cf-1234-bbc2-bd5b3a9f9533
- “Secret” Label ID 44ba5c36-b7cf-1234-bbc2-bd5b3a9f9544
- Now you can create the logical mapping between the old labels and the new Azure Information Protection labels. For example:
|
Old label Custom Property Name |
Old label Custom Property Value (Old label name) |
Azure Information Protection equivalent label name |
Azure Information Protection equivalent label ID |
|
Classification |
Public |
Public |
11ba5c36-b7cf-1234-bbc2-bd5b3a9f9511 |
|
Classification |
Internal |
General |
22ba5c36-b7cf-1234-bbc2-bd5b3a9f9522 |
|
Classification |
Confidential |
Confidential |
33ba5c36-b7cf-1234-bbc2-bd5b3a9f9533 |
|
Classification |
Secret |
Highly Confidential |
44ba5c36-b7cf-1234-bbc2-bd5b3a9f9544 |
Configure the Azure Information Protection Advanced Settings to identify the old labels and apply the new Azure Information Protection labels.
This configuration requires you to specify an advanced client setting named LabelbyCustomProperty for each Azure Information Protection label that you want to map to the old label. Then for each entry, set the value by using the following syntax:
[Azure Information Protection label ID],[migration rule name],[Old custom property name],[Specific label name OR Regex value matching the old custom property values (label names)]
In our example we will create 4 new Advanced Setting entries – one for each of the labels.
Specify your choice of a migration rule name. Use a descriptive name that helps you to identify how one or more labels from your previous labeling solution should be mapped to an Azure Information Protection label. The name displays in the scanner reports and in Event Viewer.
To configure the Azure Information Protection Advanced setting:
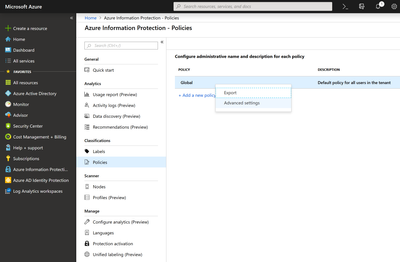
- Connect to the Azure Information Protection portal and navigate to the Policies tab
- Decide to which scope you would like to have this automatic mapping apply to. You can apply it to the global policy for everyone in your organization to have this feature enabled, or scope it for a specific audience (usually used for testing purposes)
- Right click on the relevant policy and click Advanced Settings
- In the Advanced Settings blead, you should create 4 new entries with the name LabelbyCustomProperty, and the value based on the syntax above.
in our 4-label taxonomy example, the 4 entries would look like the following
|
Advanced Setting Name |
Value |
|
LabelbyCustomProperty |
11ba5c36-b7cf-1234-bbc2-bd5b3a9f9511,"Old Public label mapping",Classification,Public |
|
LabelbyCustomProperty |
22ba5c36-b7cf-1234-bbc2-bd5b3a9f9522,"Old Internal label mapping",Classification,Internal |
|
LabelbyCustomProperty |
33ba5c36-b7cf-1234-bbc2-bd5b3a9f9533,"Old Confidential label mapping",Classification,Confidential |
|
LabelbyCustomProperty |
44ba5c36-b7cf-1234-bbc2-bd5b3a9f9544,"Old Secret label mapping",Classification,Secret |
- Click Save and Close to save the new configuration.
- Now, you can try and open an old labeled document and if the configuration was done properly, the Azure Information Protection client will be able to present you the relevant mapped Azure Information Protection label based on the old label.
- When testing, make sure to first close all Office applications and then reopen to make sure the new configuration is being used.
- Note that only users that have permissions to change the opened document will be able to use this feature. If the user does not have permissions to edit the document, the Azure Information Protection client will not be able to actually save the new Azure Information Protection
Advanced label mapping settings
In the above example we have presented the most common migration scenario we see configured (1-to-1 mapping between the old label taxonomy and the new Azure Information Protection label).
Although this is relevant for most organizations, sometimes there are cases in which an organization has more than 1 label from the old taxonomy that they would like to associate with a specific Azure Information Protection label.
Usually this situation is one of two scenarios:
- The old labeling system had multiple labels that contain the same label name, like:
- Confidential – HR
- Confidential – Finance
- …..
For such cases, the Azure Information Protection Advanced Settings supports a Regex value that can be configured to map all labels that start with “Confidential” to a specific Azure Information Protection label by using the “.*” wildcard at the end.
[Azure Information Protection label ID],[migration rule name],[Old custom property name],[Specific label name OR Regex value matching the old custom property values (label names)]
|
Advanced Setting Name |
Value |
|
LabelbyCustomProperty |
11ba5c36-b7cf-1234-bbc2-bd5b3a9f9511,"Old Confidential label mapping",Classification,Confidential.* |
- There are other old labels\tags that needs to be mapped to Azure Information Protection labels, such as:
- PCI
- PII
- ProjectX
In our example we will associate such labels with the “Secret” label. For such a scenario, you should add another Advanced Setting entry to map each of these labels to the “Secret” label.
|
Advanced Setting Name |
Value |
|
LabelbyCustomProperty |
11ba5c36-b7cf-1234-bbc2-bd5b3a9f9511,"Old PCI label mapping",Classification,PCI |
|
LabelbyCustomProperty |
11ba5c36-b7cf-1234-bbc2-bd5b3a9f9511,"Old PII label mapping",Classification,PII |
|
LabelbyCustomProperty |
11ba5c36-b7cf-1234-bbc2-bd5b3a9f9511,"Old ProjectX label mapping",Classification,ProjectX |
Conclusion
Azure Information Protection enables you to easily migrate from a previous labeling\tagging solution to Azure Information protection by following the instructions above.
We recommend getting started with testing first the migration process with Azure Information Protection labels without protection action associate to it on a small set of users by using the scoped policies. After testing the migration process on small set of documents and users and found it working as you expect you can associate a protection action if needed.
Thanks,
The Information Protection Customer Experience Engineering Team
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.