- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- Discover and protect sensitive data through Azure Information Protection and Windows Defender ATP
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
In September we announced the release of Azure Information Protection analytics Preview at Microsoft Ignite (see blog announcement), providing visibility into how to keep your sensitive data secured. Since then, Azure Information Protection analytics has been widely adopted by the Azure Information Protection community, who is looking for advanced capabilities to understand the state of their classified, labeled and protected data within the organization.
Today we are announcing the release of two new and powerful additions to Azure Information Protection analytics: Windows Defender ATP integration, and information protection investigation with analytics Activity logs.
Gain visibility into sensitive data on endpoints with Windows Defender ATP and Azure Information Protection analytics
Windows Defender Advanced Threat Protection is a platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats.
Now with its new integration with Azure Information Protection, when a file with a sensitivity label is created or modified on a Windows 10 device, Windows Defender ATP automatically reports the signal to Azure Information Protection. With this integration, Windows Defender ATP applies two methods to help discover and protect data:
- Data discovery - Identify sensitive data on Windows devices at risk
- Data protection - Apply Windows Information Protection (WIP) policy as an outcome of a sensitivity label
Data discovery
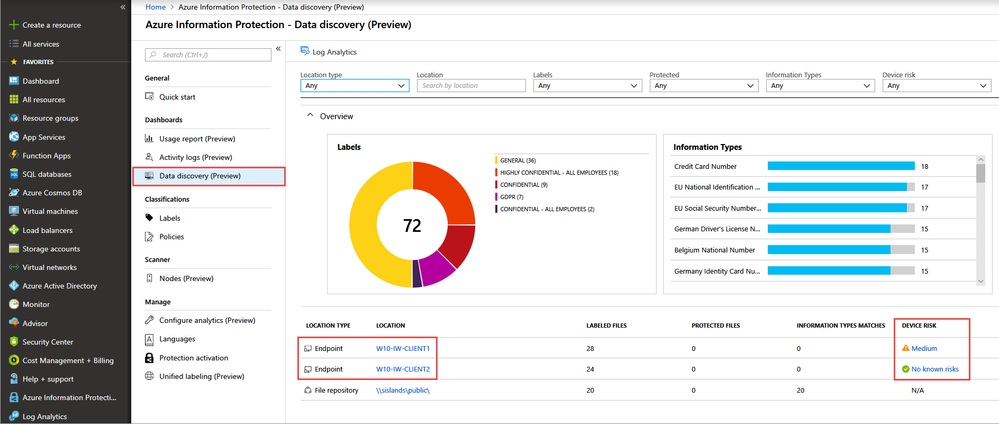
The Data discovery dashboard in the Azure Information Protection analytics blade in the Azure portal presents summarized discovery information of data discovered by both Windows Defender ATP and Azure Information Protection. The dashboard shows the sensitive data found on endpoint devices of interest, along with an assessment of the device’s risk status, indicating the security risk level of the device where the file was discovered – based on the active security threats detected by Windows Defender ATP.
Data from Windows Defender ATP is marked with Location Type - Endpoint
Data protection
When you create sensitivity labels in the Office Security and Compliance (SCC), you can also configure the information protection actions that will be applied to the file. Windows Defender ATP uses sensitivity labels to identify the sensitive files that need Windows Information Protection (WIP) policy applied on them. For example, a Microsoft Word document with a label of “Highly Confidential” that is on a Windows device can get protected with Windows Information Protection policy to prevent the inappropriate copying, sharing or transfer of that information to “non-work” locations on the device, such as personal email accounts or social media accounts.
For more information on Window Defender ATP and Azure Information Protection integration, see Information Protection in Windows overview.
Information Protection Investigation using Analytics Activity logs
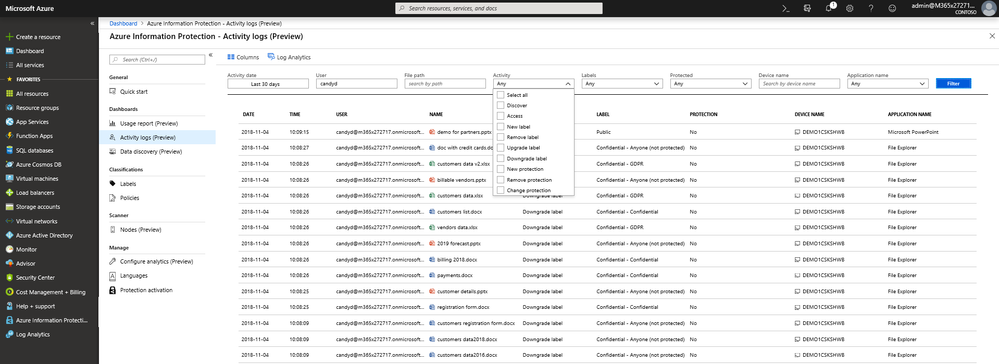
With the ability to classify, label, protect and consume sensitive data comes the necessity to track and audit information protection activities. Analyzing your organization’s information protection activities of interest by user, device, application, file label and location is now easier than ever using Azure Information Protection analytics Activity logs. Analytics Activity logs allows you to slice and dice your information protection audit data and drill down into users, devices, and label classification activities, providing a comprehensive view of how your users classify and consume sensitive data.
Activity logs provides you visibility into your information protection activities by users, devices and labels
For more information on analytics Activity logs, see Central reporting for Azure Information Protection.
We look forward to your feedback!
Azure Information Protection team
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.