- Home
- Azure
- Azure Governance and Management
- An activity log alert should exist for specific Policy operations : Wrong category in the rules sec
An activity log alert should exist for specific Policy operations : Wrong category in the rules sec
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 23 2020 01:51 AM
Hi,
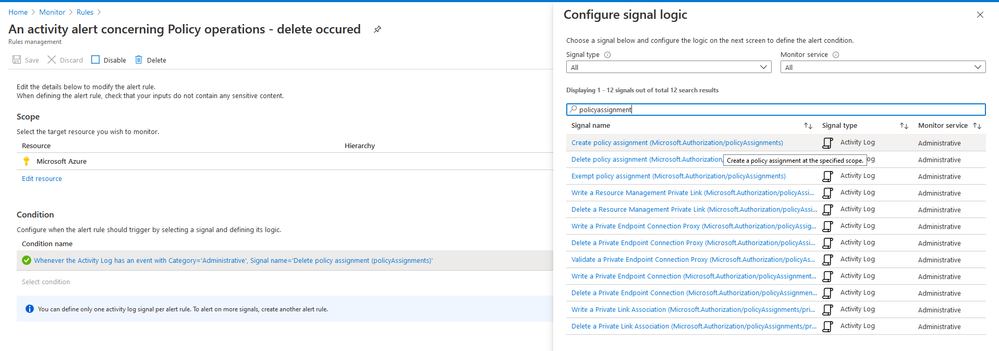
I have "CIS Microsoft Azure Foundations Benchmark 1.1.0" assigned to my subscription and the policy "An activity log alert should exist for specific Policy operations" is non-compliant even though I created necessary alert rules. I noticed that the category for the necessary alert rules (allowed values in the policiy definition) is "Administrative" rather than "Policy" which is indicated in the policy rules. When I duplicate the policy and change the category into "Administrative" it becomes compliant but the built-in policy is not effected from this and the whole initiative stay non-compliant which also effects my compliance level for industry standards. What can I do to make this policy and initiative to be compliant and getting compliant with industry standards? Or should it be updated by the relevant team?
Sahin
- Labels:
-
Azure Policy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 02 2021 06:39 PM
https://github.com/Azure/azure-policy/blob/569022638bf0518edb463eff23918240faa1843a/built-in-policie...