- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Feb 15 2023
07:20 PM
- last edited on
Mar 05 2024
02:26 PM
by
TechCommunityAP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 15 2023
07:20 PM
- last edited on
Mar 05 2024
02:26 PM
by
TechCommunityAP
In Azure Pipelines, we need to get source code of another organization's Azure Repos. Currently we use personal access token, but it links to a user who might leave the organization. Can we use a service principle to authenticate? How to grant the service principle access right to the other organization's Azure Repos?
- Labels:
-
Azure DevOps
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 15 2023 08:48 PM
Use a service principal to authenticate and access another organization's Azure Repos in Azure Pipelines.
Here are the steps to grant the service principal access rights:
- Create a service principal in the Azure Active Directory tenant of your organization, if you haven't done so already. You can create a service principal using the Azure Portal or the Azure CLI.
- Assign the "Contributor" role to the service principal at the organization level. This will give the service principal access to all resources in the organization, including the Azure Repos.
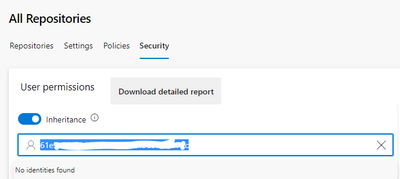
- Go to the Azure DevOps project that contains the pipeline, and navigate to the "Repos" tab. From there, click the "..." button next to the repo you want to access, and select "Security".
- Add the service principal as a user in the repo's security settings, and grant it the "Read" permission.
Check out out document for further details .https://learn.microsoft.com/en-us/azure/devops/repos/git/set-git-repository-permissions?view=azure-d...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 28 2023 12:46 AM
for the 2nd step, the organization level means Azure DevOps Organization? How to assign "Contributor" Role to service principle at the organization level?
Auzre DevOps API permission was granted to the service principle.
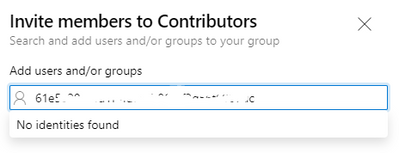
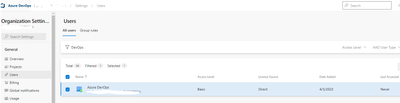
But I cannot find the service principle in Azure Devops organization users, project contributor, and repos security settings tab.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 28 2023 06:38 AM - edited Mar 28 2023 07:17 AM
Azure DevOps, an organization is the top-level container that holds all your projects, teams, and other resources.To assign the "Contributor" role to a service principle at the organization level in Azure DevOps, you can follow these steps:
- Go to your Azure DevOps organization and click on the "Organization settings" gear icon in the lower left corner.
- In the left-hand menu, click on "Permissions".
- Click on "Security groups".
- Create a new security group or select an existing one.
- Click on "Members" to add members to the security group.
- Click on "Add" and select "Service principal".
- Type in the name or ID of the service principal and click "Add".
- Click on the security group again and click on "Permissions".
- Click on "Add" to add a new permission.
- Select the "Contributor" role from the list of available roles.
- Choose the scope of the permission (in this case, the organization).
- Click "Add" to save the permission.
After completing these steps, the service principal should have the "Contributor" role at the organization level. If you cannot find the service principal in the Azure DevOps organization users, project contributor, and repos security settings tab, make sure that you have granted the appropriate Azure DevOps API permissions to the service principal and that it has been added to the appropriate security group with the "Contributor" role.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 03 2023 12:35 AM
For step 8-12, I cannot find the "Add" button to add a new permission (role) for the security group, but can only set the permission for items listed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 04 2023 10:56 AM
To check if this is the case, you can navigate to the "Permissions" section again and select the security group you created or selected. Then, look for the "Permissions" tab and check if there are any available permissions listed that can be assigned to the security group at the organization level.
If there are no available permissions listed, then it's likely that the security group can only be assigned permissions at the individual or team project level. In that case, you will need to navigate to the specific project or team and assign the "Contributor" role to the security group there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 04 2023 09:43 PM
Would like to share a similar post for reference:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 06 2023 12:08 AM
I encountered the same authentication error when creating Azure Repos Connection with the Service Principle's APP ID and secret.
So it is not workable to use Service Principle to access another organization's Azure Repository.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 07 2023 11:26 AM
First, you will need to ensure that the service principal has been granted access to the Azure DevOps organization where the repositories are located. This can be done by adding the service principal as a member of the Azure DevOps organization, and granting it the appropriate permissions.
Next, you will need to grant the service principal access to the specific Azure Repositories that you want to access. This can be done by going to the Azure Repositories security settings and adding the service principal as a contributor or a reader, depending on the level of access you require.
Once the service principal has been granted access to the Azure DevOps organization and the Azure Repositories, you can use its App ID and secret to authenticate your connection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 13 2023 12:12 AM
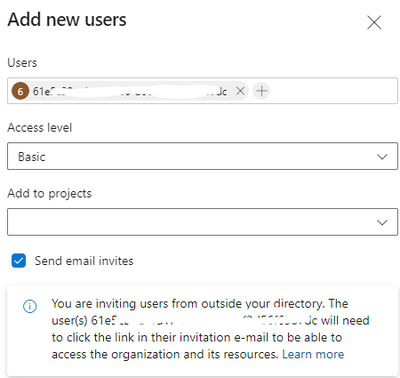
Have added the service principle to the organization
Have granted the service principle "Project Reader" Role for the project
Have granted read access right to all repositories of the project.
But still got the error message when verify the service connection
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 14 2023 10:18 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 18 2023 02:24 AM
Failed to query service connection API: 'https://email address removed for privacy reasons/xxx/xxx/_git/xxxx/_apis/projects'. Status Code: 'Unauthorized', Response from server: ''
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 19 2023 01:58 AM