- Home
- Azure
- Microsoft Developer Community Blog
- The Azure Security Architect Map
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Hi,
Recently, I built the Azure Solution Architect Map aimed at helping Architects finding their way in Azure. Given the unexpected success and the very positive feedback I received, I decided to come up with other maps, namely the Azure Security Architect Map, the Azure Infrastructure Architect Map and the Azure Application Architect Map.
Here are all the maps in my series of Architecture Maps:
- The OpenID Connect (OIDC) Architecture Map
- The Azure Kubernetes Service (AKS) Architecture Map
- The Cloud-native Azure Application Architect Map
- The Azure Infrastructure Architect Map
- The Azure Security Architect Map - This map
- The Azure Solution Architect Map
The purpose of the Solution Architect map is to give a high-level view and quick insights about what is available and how to choose between the different services according to some functional needs.
It covers a few key areas, mostly about putting in place the foundations of an Azure Platform, and cannot go into the details because this would make the map very indigestible.
Today I come with the Azure Security Architect Map:
which focuses on security only and goes much deeper into that key area. It is by no means the holy grail but it should help you take informed decisions on how you plan to use and deploy services and how you will govern your Azure workloads. I bring business drivers such as TTM, cost optimization and true elasticity into the equation to highlight the consequences of choosing an option over another.
The map focuses on the following areas:
- Network Layer
- Identity Layer
- Application Service Layer
- Application Data
- Security Posture
- Keys, Certificates and Secrets Management as well as Encryption capabilities
- MDM & MAM
How to read this map?
Whenever you see the attachment icon 
I want to catch your attention on the following:
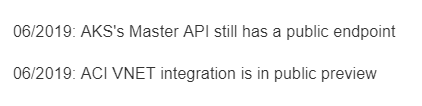
The rationales behind certain routes are based on my own experience and do not represent the only option, but they should be considered as advisory only. So the idea is to review these maps frequently since the above information is likely to change over the coming months and I'll simply keep adding notes or remove them when it does not make sense anymore.
The link icon 
With this tool, any Security Architect (Cloud or not) will quickly grasp the security landscape of Azure.
Here is the pointer to the map:
Update (02/2021): the online MindMapMaker tool deletes maps that are older than 1 year....A pointer to the last version is available in the below table.
| Last MindMapMaker map |
https://app.mindmapmaker.org/#m:mmd329ac370bf141948f565b79c40b0ff6 |
| Last PDF map |
Here are all the maps in my series of Architecture Maps:
- The OpenID Connect (OIDC) Architecture Map
- The Azure Kubernetes Service (AKS) Architecture Map
- The Cloud-native Azure Application Architect Map
- The Azure Infrastructure Architect Map
- The Azure Security Architect Map - This map
- The Azure Solution Architect Map
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.