- Home
- Azure Data
- Azure Database Support Blog
- Restore a DB encrypted with a TDE key into a server/instance having a different encryption key
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
If you need to restore a database that was encrypted with a TDE (transparent data encryption) customer-managed key into a server that is encrypted with a different key, you can follow the steps below:
- If necessary, restore the TDE customer-managed key that was used to encrypt the database you will restore into the Azure Key Vault (AKV) you intend to use.
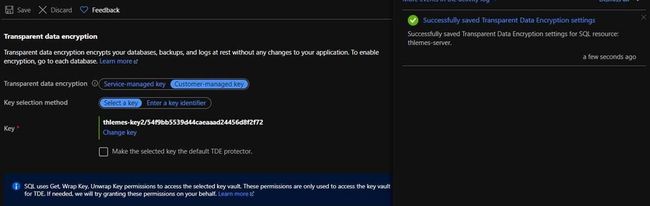
- On the “Transparent data encryption” blade of the target server/instance, click on “change key” and select the key with which the source backup was encrypted:
- Uncheck the “Make the selected key the default TDE protector” and save. By unchecking the key as TDE Protector, you will add the key to the server/instance without changing the encryption key of Its databases:
Note: They key was changed from thlemes-sqldb-k to thlemes-key2
- After the operation completes, you will see the key you selected in ‘Key’, but with the ‘Make the selected key the default TDE protector’ unchecked:
- However, if you refresh the page, It will show again the TDE Protector key:
This is because the TDE Protector key wasn’t changed and It’s shown by default in the Portal. However, after adding the source key as non-TDE Protector, you will be able to successfully perform the restore from the source backup into the target server/instance.
Although you can’t see the keys that are not the TDE Protector in the Portal, you can list them using REST API:
SQL Managed Instance: https://docs.microsoft.com/en-us/rest/api/sql/managedinstancekeys
SQL Server: https://docs.microsoft.com/en-us/rest/api/sql/serverkeys
There is also a REST API command to delete the key if you need to, as you can see in the links above.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.