- Home
- Security, Compliance, and Identity
- Microsoft Entra Blog
- Ring in the New Year with automated user provisioning from SAP SuccessFactors to Azure AD
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Howdy folks,
Today, I’m very excited to announce the public preview of automated inbound user provisioning from SAP SuccessFactors to Azure AD and on-premises AD.
This builds on the momentum we have already established in simplifying how identities are managed in Azure AD. Early this year, we delivered inbound user provisioning from Workday to Azure AD. We also added more pre-built provisioning capabilities to your favorite SaaS apps including the ability to manage users in bulk. And last week, we announced the public preview of Azure AD Connect cloud provisioning.
The public preview of inbound user provisioning from SuccessFactors allows customers to easily orchestrate users from SuccessFactors into Azure AD.
With this built-in cloud-based integration of Azure AD with SuccessFactors, you can:
- Securely tap into the rich workforce identity and organization data present in SuccessFactors.
- Implement end-to-end identity lifecycle management covering the entire spectrum of Joiner-Mover-Leaver scenarios.
- Eliminate error prone custom scripts to sync employee and contractor data.
Give this a try today
There are five simple steps for you to get started on this capability.
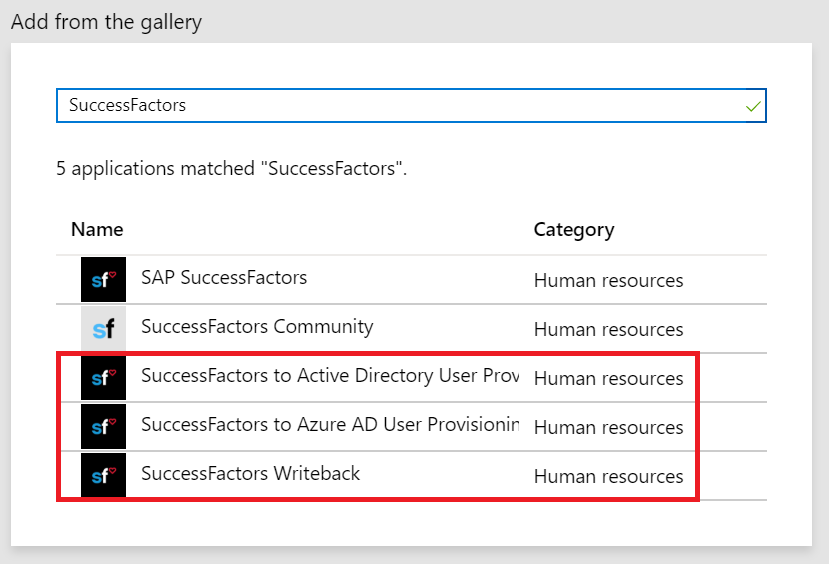
Step 1—Select the right provisioning app from the gallery
In the Enterprise App gallery, there are three new pre-integrated applications designed to meet your requirements around SuccessFactors integration.
- SuccessFactors to Active Directory User Provisioning—Use this app if you have a hybrid identity setup and would like to provision users directly from SuccessFactors to on-premises Active Directory.
- SuccessFactors to Azure AD User Provisioning—Use this app if you have cloud only users and would like to provision users directly from SuccessFactors to Azure AD.
- SuccessFactors Writeback—Use this app to writeback email address from Azure AD to SuccessFactors.
For more information, refer to the decision flowchart in the Cloud HR deployment plan.
Step 2—Configure connectivity to SuccessFactors ODATA API server
Azure AD needs to be configured with the account that has permissions to read data from SuccessFactors.
If you’re configuring integration with on-premises AD, there is an additional step of installing and configuring Azure AD Connect provisioning agent that is capable of provisioning to multiple AD domains. Refer to the integration tutorial for detailed steps.
Step 3—Configure scoping to define identities that will be managed with this integration
Identify which users should be provisioned from SuccessFactors to Azure AD or on-premises AD. If you want to rollout SuccessFactors HR integration gradually based on location, department or division, then you can use the scoping filters to determine which users should be provisioned.
The example below uses a scoping filter based on the department attribute:
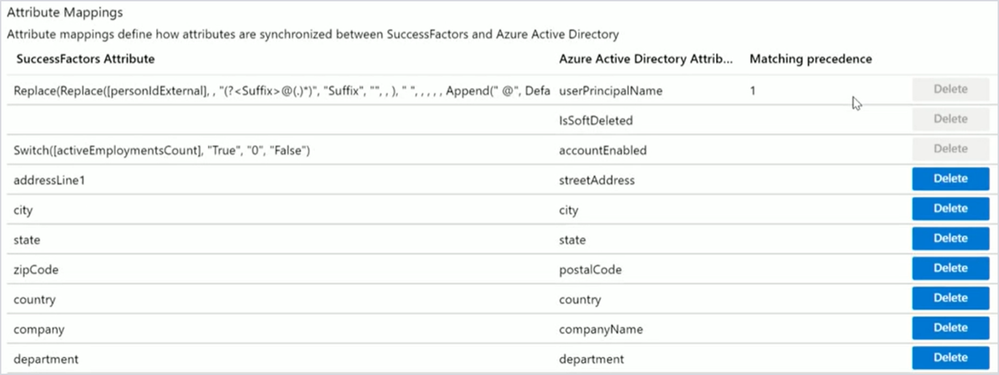
Step 4—Configure attribute mappings
The pre-built SuccessFactors provisioning connector supports mapping 70+ different attributes from SuccessFactors. With expression mapping functions, you can apply attribute transformations such as replacing strings, concatenating values and generating unique identifiers.
Step 5—Turn on the provisioning cycle
Start the provisioning cycle and use the progress bar and provisioning logs to track the provisioning process.
The SuccessFactors-driven inbound user provisioning feature requires Azure AD Premium P1 subscription. To help you plan your deployment, we have published a comprehensive cloud HR deployment plan as well as a tutorial for configuring SuccessFactors for Inbound User Provisioning
Let us know what you think in the comments below. You can also post your feedback or suggestions for new capabilities that you would like to see in our Azure AD UserVoice feedback forum.
Best regards,
Alex Simons (@Alex_A_Simons )
Corporate VP of Program Management
Microsoft Identity Division
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.