- Home
- Security, Compliance, and Identity
- Microsoft Entra Blog
- Introducing security defaults
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Hey folks,
In 2012, we started the Identity security and protection team for our consumer accounts (Microsoft accounts used for signing in to OneDrive, Skype, Xbox and such). We started out by doing two things – putting metrics in place for everything (so we could be confident we’d know what works) and establishing a security minimum standard for our consumer accounts. This includes measures like registering a second factor, challenging accounts when we see risk on the login, and forcing folks to change their passwords when we found them in the hands of criminals. The results have been very good; while there was some angst involved in requiring multi-factor authentication (MFA) registration to play Xbox or on that Hotmail account that’s “worked fine for 16 years!”, the net impact was massively positive – e.g., measuring from 2014 to 2019:
- Unaided password recovery jumped from less than 20% to more than 90%
- Account retention increased by more than 10%
- Our ability to challenge users when we see risk led to a 6x decrease in compromise rate. This means that even as we’ve had a substantial increase in users, we have fewer compromised Microsoft accounts than ever before.
In 2014, we started making these technologies available to our Azure Active Directory (AD) organizational customers, and we’ve learned that they’re very effective – for example, our telemetry tells us that more than 99.9% of organization account compromise could be stopped by simply using MFA, and that disabling legacy authentication correlates to a 67% reduction in compromise risk (and completely stops password spray attacks, 100% of which come in via legacy authentication).
Unfortunately, we’ve been less successful than we’d like at raising awareness and getting folks to adopt the technologies. While the tools are in place for customers to stop these attacks, adoption is significantly low. Despite marketing, tweeting, and shouting from the rooftops, the most optimistic measurement of MFA usage shows that only about 9% of organizational users ever see an MFA claim.
If you’re reading this blog, you’re probably a security or identity enthusiast. You’re aware of the importance of securing identities and taking advantage of key capabilities in the platform. But for most people, especially individual developers, small businesses, or folks just experimenting with our Azure, Office, or Dynamics services, security isn’t the first thing on their minds. The goal is just to find the shortest path to setting up email and document sharing, or building that first Azure application – they won’t configure security settings until they’ve been hacked.
With millions of organizational accounts vulnerable to preventable compromise each year, we felt we needed to take a different tack – to protect organizational accounts just like we do the consumer accounts. We experimented with a few different approaches (including “Baseline protection”), listened to partners and customers, and learned a ton along the way. The result of all this learning is Security Defaults.
Security defaults provide secure default settings that we manage on behalf of organizations to keep customers safe until they are ready to manage their own identity security story. For customers like this, we’ll manage their security settings like we do for our Xbox, OneDrive, Skype and Outlook users.
For starters, we’re doing the following:
- Requiring all users and admins to register for MFA.
- Challenging users with MFA - mostly when they show up on a new device or app, but more often for critical roles and tasks.
- Disabling authentication from legacy authentication clients, which can’t do MFA.
We will judiciously expand these security defaults to maximize protection for our users, but as MFA prevents >99.9% of account compromise, that’s where we’re starting. We are applying security defaults for all license levels, even trial tenants, ensuring every account can be protected by MFA.
None of this replaces the rich security capabilities in Azure Active Directory. If you are a person who uses Conditional Access to manage your break glass accounts with terms of use controls, chooses MFA based on device compliance, or integrates Identity protection reports into your SIEM, you’re far more sophisticated than our target user for Security Defaults. If you’re thinking of break glass accounts or exception scenarios, Security Defaults isn’t for you – you want Azure AD Conditional Access.
Since introducing the feature, we’ve enabled Security Defaults for more than 60k newly created tenants. More than 5k other tenants have opted into Security Defaults. All of these organizations have significantly reduced their compromise rates; only a few hundred have opted out, mostly to use Conditional Access. We’ll take the learnings from these tenants and continuously tune as we eventually roll this out to all new tenants, then to tenants who have never looked at security settings. We will expand first to apply security defaults to all new tenants as well as applying it retroactively to existing tenants who have not taken any security measures for themselves. We’re experimenting, listening and adapting as we go.
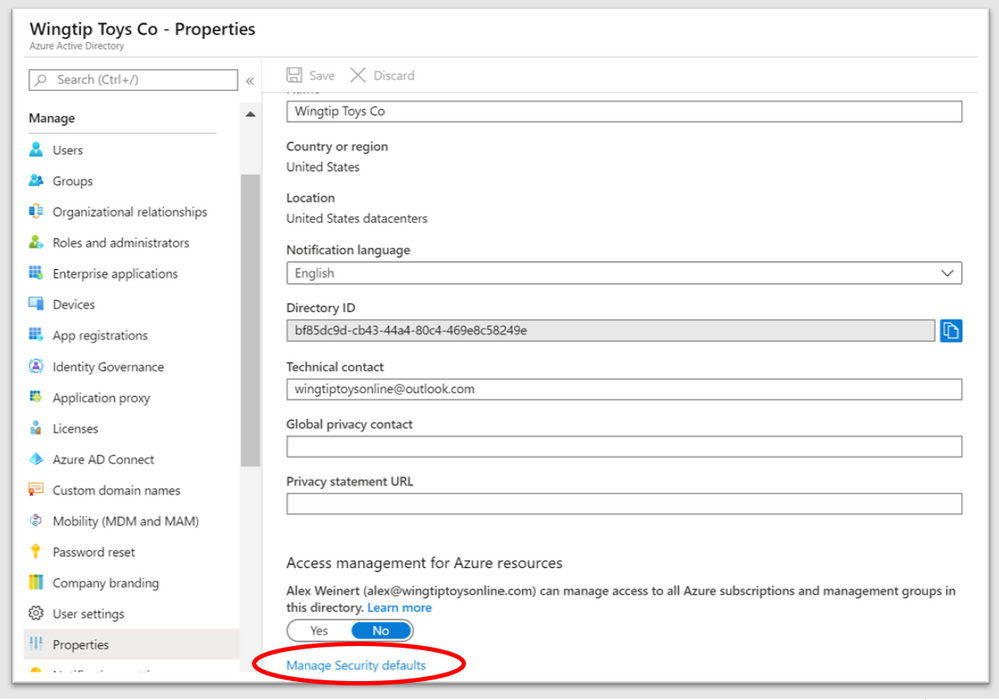
If you have an existing tenant where you’d like to enable security defaults, or are ready to turn it off and move up to using Conditional Access to manage your access policies, you’ll find the settings in your Azure AD tenant configuration in Azure Active Directory, Manage, Properties – look for “Manage Security Defaults” at the bottom of the page:
Click there and you’ll see the blade that allows you to enable security defaults. But again, security and identity enthusiast – you probably want the advanced controls that Azure Active Directory Conditional Access gives you.
You can’t enable Security Defaults if you’re already using conditional access policies or other settings which conflict. If you do, you’ll see this warning:
Some of you may have tried out baseline protection policies – security defaults replaces all those settings, and we will stop enforcing them on Feb 29th. If you’re reading this, you probably want the granular control Conditional Access gives you, so in place of baseline, set up the equivalent Conditional Access policies as outlined here.
The Identity Security team is super-focused on preventing account compromise, and ensuring there is no barrier to secure, multi-factor authentication using secure protocols is a critical step forward. As always, we’d love your feedback. Reach out to me at @alex_t_weinert on twitter!
Stay safe out there,
Alex
- « Previous
-
- 1
- 2
- Next »
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.