- Home
- Security, Compliance, and Identity
- Microsoft Entra
- Re: Detect compromised passwords
Detect compromised passwords
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Feb 28 2020
08:18 AM
- last edited on
Jan 14 2022
03:56 PM
by
TechCommunityAP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 28 2020
08:18 AM
- last edited on
Jan 14 2022
03:56 PM
by
TechCommunityAP
After looking in the Sign-in view and seeing all the login attempts trying to guess passwords we implemented MFA, so feel a little more secure! However we still get phishing emails and users will be users so passwords are still going to get compromised, now any attempt to login should get blocked by MFA but i would like to be able to detect these and reset the users passwords, so any suggestions on how i would recognise a login attempt where a correct password was entered but it was blocked by MFA?
Thanks
Huw
- Labels:
-
Access Management
-
Microsoft 365
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 28 2020 12:06 PM
Those are visible in the Sign in logs, not sure what the question is here?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 28 2020 07:34 PM - edited Feb 28 2020 07:34 PM
There are two types of log detections and they’re both migrated to MCAS (Cloud Apps Security)-> Alerts.
1. Multiple logon failures: Which represent logins from different countries with brute force attacks.
2. Sign in from unfamiliar locations: These are legit, someone trying to access accounts using right password from unfamiliar locations.
Recommendations
1. I highly recommend enabling Geo-Fencing to access your O365 by location.
https://cloudbymoe.com/f/geo-fencing-access-to-o365-using-conditional-access
2. Use PowerBI to connect to MSFT Graph Security API to have dynamic rich reports that refresh automatically.
https://cloudbymoe.com/f/connect-powerbi-to-microsoft-graph-security
Hope this helps!
Moe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 29 2020 06:47 AM
You could configure an extra rule in Azure Sentinel which detects certain Azure AD Sign-in Error codes and throw an alert on certain conditions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 29 2020 08:32 AM
@Huw Weatherhead you have quite a few options.
https://docs.microsoft.com/en-us/cloud-app-security/getting-started-with-cloud-app-security
from there you will be able to automate rules and receive notifications via email
Azure AD Sentinel
https://docs.microsoft.com/en-us/azure/active-directory/reports-monitoring/concept-risky-sign-ins
more difficult and you have to learn how to use this tool
O365 ATP with E5 licence
https://docs.microsoft.com/en-us/microsoft-365/compliance/alert-policies?view=o365-worldwide
A very informative place to start looking if you have E5 license in addition with E5 you can also configure "safe links"
and of course third party tool like Mimecast :)
Regards _tim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 01 2020 04:36 AM
Hi @Huw Weatherhead,
There’s a distinction here between identifying, and alerting on this type of activity. As the previous replies have indicated there are proactive alerting mechanisms in the form of MCAS / Sentinel, but clearly these may carry over a cost to you over more manual ways of identifying this sort of behaviour.
As Vasil suggested, at a base level you will see these reflected in the Azure AD sign-in logs as failed sign-ins (due to lack of MFA, as opposed to an incorrect password which you will be able to distinguish from the log data). Not as elegant as an alert based solution (which I’d recommend), but it will allow you to identify those accounts where passwords have been compromised with a bit of leg work.
Obviously this will be supplemented by Microsoft’s leaked credential detection service assuming you have AAD P1 or P2 :)
Hope this helps,
Kelvin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 02 2020 12:32 AM
Thanks for your response, I guess my question is really what should i look for in the sign in logs to spot a login attempt which presents a correct password but then fails the MFA check?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 02 2020 01:46 AM
Solution
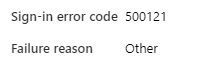
You'll see a failure reason of "other" in the sign-in logs, as opposed to "invalid username or password":
or...
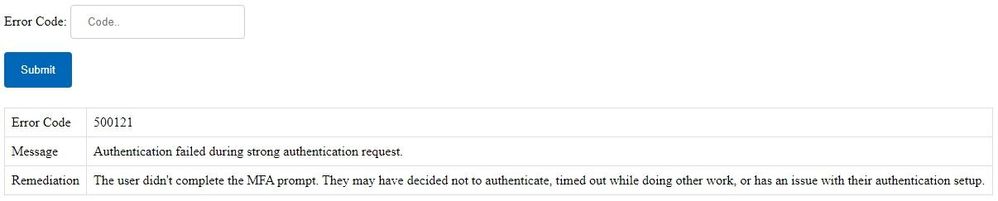
The sign-in error code is also key - 500121 above relates to a failed strong authentication in the context of "other":
Regards,
Kelvin
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 02 2020 01:46 AM
Solution
You'll see a failure reason of "other" in the sign-in logs, as opposed to "invalid username or password":
or...
The sign-in error code is also key - 500121 above relates to a failed strong authentication in the context of "other":
Regards,
Kelvin