- Home
- Security, Compliance, and Identity
- Microsoft Entra Blog
- Custom roles for app registration management is now in public preview!
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Howdy folks,
I’m excited to announce the public preview of custom RBAC roles for Azure AD. Custom roles give you fine-grained control over what access your admins have. This first release of custom roles builds on our previous work for delegating application management and includes the ability to create a role to assign permissions for managing app registrations. Over time, we’ll release additional permissions to delegate management of enterprise applications, users, groups, and more. Azure AD custom roles requires an Azure AD Premium P1 subscription.
Custom RBAC roles for Azure AD surfaces the underlying permissions of built-in admin roles, so you can create and organize your own custom roles. Let’s walk through an example of how to build a custom role and assign it to an administrator!
Create and assign a custom role
In the following example we’ll create a custom role called, “Application Support Administrator” that has permissions to update app registration credentials. Once the custom role is created, we’ll assign the role to a specific user to manage registration of a specific application.
Create a custom role
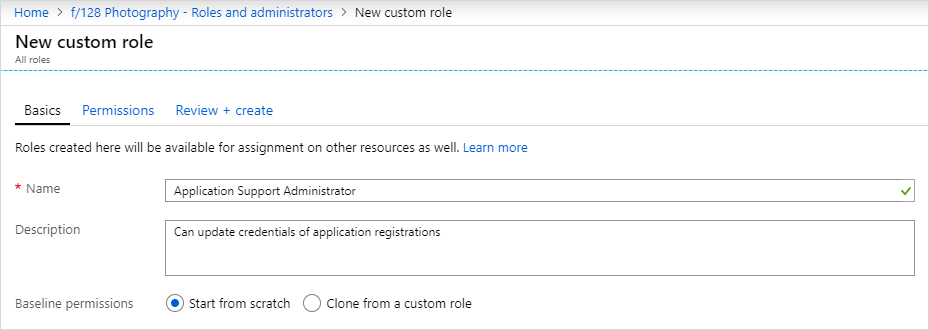
- On the Roles and administrators tab, select New custom role.
- Provide a name and description for the role and select Next.
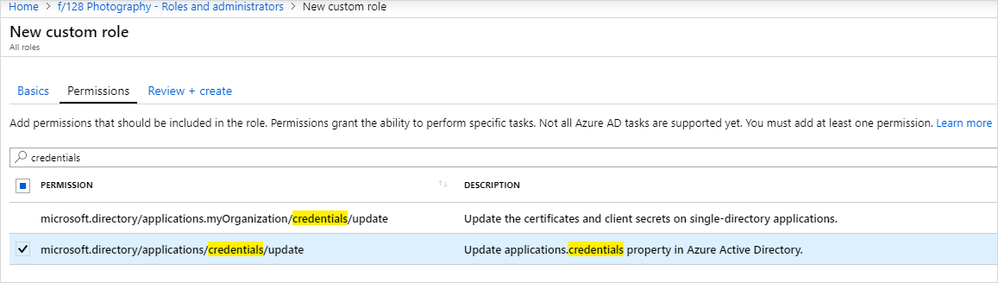
- Assign the permissions for the role. Search for credentials to select the microsoft.directory/applications/credentials/update permission.
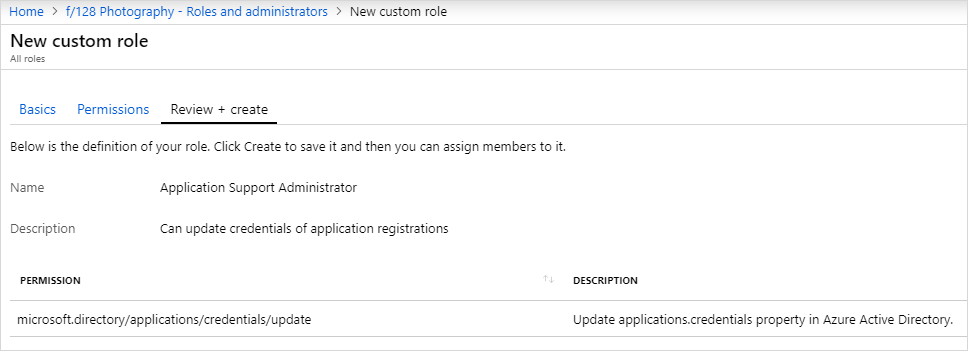
- Review the new role and if everything looks good, select Create to create the new role.
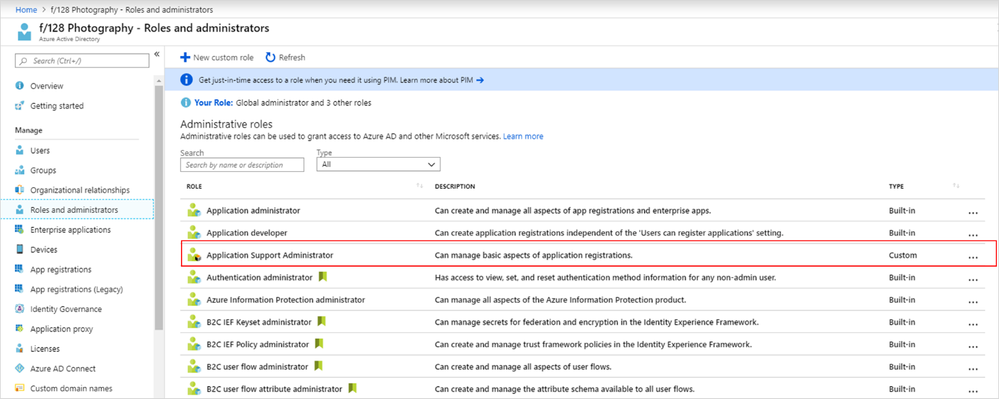
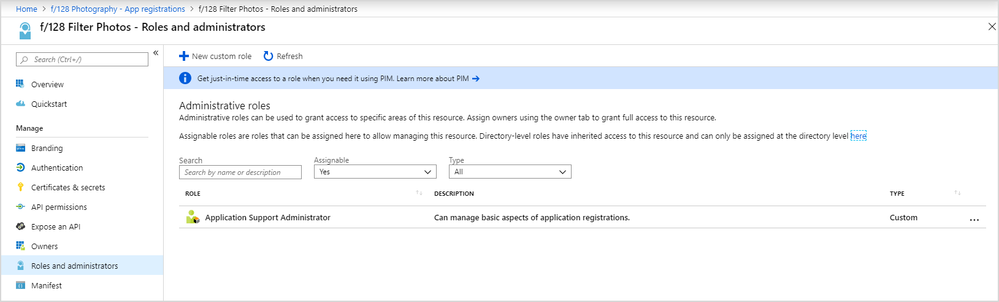
Your custom role will show up in the list of available roles to assign.
Assign the custom role
Like built-in roles, custom roles can be assigned at the directory level to grant access over all app registrations. Additionally, you can assign custom roles over just one application, as shown in our example. This allows you to give the assignee the permission to update credentials of just one app registration without having to create a second custom role.
- Select the App registrations tab and pick an app registration that you want to give someone access to manage credentials.
- Navigate to the new Roles and administrators tab. You’ll see the Application Support Administrator custom role created above.
- Select the role to open the assignment blade, select Add assignment, and then select a person to add to the role.
All done! In our example, Abby Brekkan now has the ability to manage credentials for the f/128 Filter Photos app registration. She won’t have any permissions over any other app registrations.
Privileged Identity Management customers should be pleased to know that time-bound activation into custom roles is supported as part of this preview as well. And if APIs are your thing, we support PowerShell, and Microsoft Graph APIs are in the process of rolling out now.
App registration permissions is just the first step for us. We’ll continue to release additional permissions for other areas of Azure AD including enterprise applications, users, groups, and more. You can find more information in our documentation, including an overview and supported permissions.
As always, we'd love to hear your feedback, thoughts, and suggestions! Feel free to share with us on the Azure AD administrative roles forum or leave comments below. We look forward to hearing from you.
Best regards,
Alex Simons (@Alex_A_Simons)
Corporate VP of Program Management
Microsoft Identity Division
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.